Nine Compelling Reasons Why Menta eFPGA Is Essential for Achieving True Crypto Agility in Your ASIC or SoC
By Menta
Today’s world is already overly complicated to provide robust product security, with extremely motivated hackers creating novel threats exposing new vulnerabilities every day. But considering tomorrow’s world with the looming threat of quantum computing, expanding AI possibilities and rapidly evolving regional regulations and export control risk with severe financial penalties, this is a daunting challenge. The concept of crypto agility emerged as a convincing solution to this intimidating and unsettling problem, offering organizations a flexible framework to adapt their security protocols in response to these ever-changing threats. Crypto agility protects against threat evolution, enables quantum readiness and support for novel cryptography algorithms, adapts to regional requirements and offers product life extension – especially in critical markets like industrial, space and automotive where product lifespans can exceed 10+ years.
The good news? The solution to this problem is available today! And many may assume they can simply handle this with software running on their processor. But let’s be crystal clear: processors and software fall woefully short as this solution harbors numerous vulnerabilities and limitations that inevitably compromise security, performance and reliability. Software consistently proves susceptible to timing and cache attacks as well as power and electromagnetic emissions analysis. Furthermore, cryptography keys remain perpetually at risk due to well-documented issues including RAM scraping, swap leaks and cold boot attacks. And regarding performance – the evidence is undeniable – software simply cannot keep pace, particularly in high-performance systems and edge-based devices where efficiency is paramount.
Table 1: Vulnerabilities of Software Cryptography
| Risk Category | Examples |
| Side Channel Attacks | Timing and cache attacks, power analysis |
| Key Exposure | RAM scraping, cold boot, swap leakage |
| Performance | Slow cryptography operation, CPU & memory bottlenecks |
| Implementation Flaws | Bugs, misuse of APIs, non-standard protocols |
| Reverse Engineering | Code tampering, key extraction, behavior modification |
| Weak Entropy | Poor RNGs, especially in embedded or virtual systems |
| OS Intrusion | TCB replacement tampering or Ring 1 ICP tampering |
Hardware-based security solutions are essential to address modern threats, and they can only be effectively implemented through adaptable hardware platforms such as embedded FPGA (eFPGA). In this article, we will examine how Menta’s eFPGA IP specifically provides solutions to these security challenges. Our analysis will focus on the various attack vectors that pose significant threats to device security in this evolving environment.
Solution #1 – Enable Any Future Cryptography Algorithm
We have witnessed the evolution of encryption algorithms over the years, primarily through increases in key size to match growing computer capabilities. With quantum computing becoming an imminent reality, certain public-key algorithms—specifically RSA and ECC—face significant vulnerability to quantum attacks. In response, organizations such as NIST are actively searching for and developing quantum-resistant algorithms to ensure future security.
Figure 1: NIST Computer Security Resource Center for Post Quantum Cryptography Solutions
Algorithms like these can be efficiently run on embedded FPGAs (eFPGA) technology. Let’s look a couple of examples from our partners Xiphera and PQSecure. Below is Xiphera’s xQlave® ML-KEM (Kyber) Key Encapsulation Mechanism IP core that provides quantum-resistant key exchange, offering a secure solution against the growing threat posed by quantum computing. This solution can be implemented efficiently, using less that 10K LUTs with high performance of over 110MHz – simulated on a 28nm technology node.
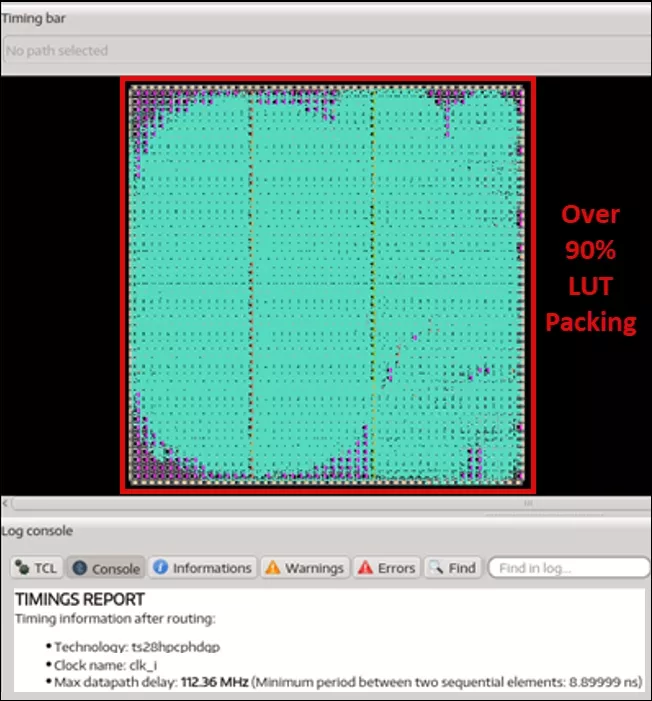
Figure 2: Xiphera ML-KEM (XIP6110B) IP Core
Here is another example using a solution from PQSecure. Their CRYSTALS-1000 core is a unified hardware IP that implements both CRYSTALS-KYBER and CRYSTALS-Dilithium algorithms. This core includes comprehensive security features: it protects against Simple Power Analysis (SPA) and first-order Differential Power Analysis (DPA) attacks through techniques like masking and shuffling. Additionally, it prevents timing attacks by ensuring all operations execute in constant time, regardless of input data. This combined solution runs very efficiently on Menta eFPGA IP utilizing under 14K LUTs and running at nearly 70MHz on 28nm technology.
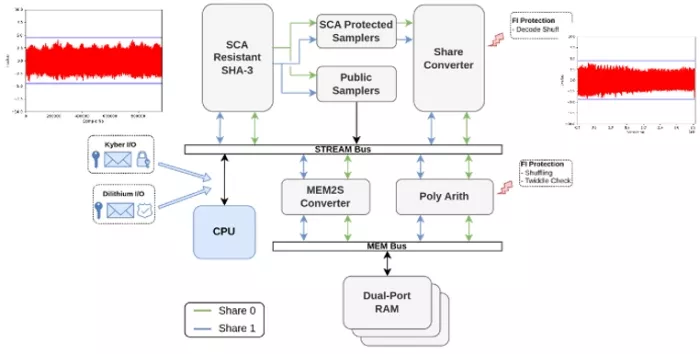
Figure 3: PQSecure Crystals-1000 PQC Architecture
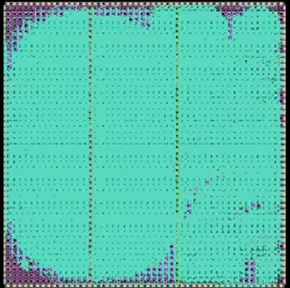
Figure 4: PQSecure CRYSTALS-1000 PQC IP Core Implementation on Menta eFPGA IP
These two examples show that future PQC solutions can be efficiently run on Menta eFPGA IP.
Solution #2 – Enable Any Future Side Channel Mitigation Implementation
Currently there are over 100 catalogued known vulnerabilities from side-channel attacks. These include timing and electromagnetic and power attacks, optical and acoustic, memory and many other forms of leakage that hackers search for to reverse engineer security algorithms and keys.
Table 2: Side Channel Attack Vectors and Threat Levels
| Attack Type | Leakage Channel | Example Target | Risk Level |
| Power Analysis | Current Consumption | Smartcards, HSMs, Crypto ICs | High |
| Timing Attacks | Execution Time | SSL/TLS, RSA/ECC on MCUs | Medium |
| EM Analysis | Radiated EM Fields | RFID, Contactless cards, SoCs | High |
| Glitching/Fault | Voltage, Clock, Light | Secure boot, key storage | High |
| Cache Attacks | Shared memory/cache | CPUs, embedded Linux | Medium |
| Acoustic/Optical | Sound/Photons | Niche | Low (for now) |
The key to solving this is eFPGA hardware-based countermeasures that include constant-time logic and datapaths, using masking and balancing to randomize intermediate values to enable power and EM analysis resistance, real-time sensor monitoring and redundant computing to detect and mitigate fault injections and glitches. And this list of leakage mitigation techniques will continue to evolve to offset novel threats, and adaptable hardware solutions may be the only answer.
Solution #3 – Enable Adaptable Anti-Tamper Mitigation
Using eFPGAs inside ASICs for anti-tamper protection is an increasingly popular strategy in secure hardware design. eFPGAs provide in-field reconfigurability, which helps combat physical, side-channel, and reverse-engineering attacks without compromising performance or security. The table below highlights the benefits of using eFPGA for anti-tamper mitigation in ASICs.
Table 3: Anti-Tamper Benefits of eFPGA
| Benefit | How it Helps with Anti-Tamper |
| Reconfigurability | Hide critical logic; Ability to change post-deployment |
| Obfuscation | Delay or confuse reverse engineering attempts |
| Runtime Adaptability | Respond to detected threats in real-time; key, logic self-destruct |
| Interface Masking | Minimize surface attacks by disconnecting unused interfaces |
| Secure Updates | Patch vulnerabilities or switch crypto algorithms based on tamper |
| Dynamic Logic Unlocking | Lock key functions until authenticated at runtime |
Solution #4 – Enable Security Autonomy
Many security vendors offer packaged solutions that tightly link your system’s resilience to their specific products. This dependency creates several challenges, particularly regarding trust and control over the intellectual property. With more contributors involved in developing these security systems, there’s an increased statistical probability of trojan insertion and potential compromise. eFPGA allows flexibility to implement your own additional security layer, you regain control and can establish security enforcement policies that truly meet your specific needs.
Solution #5 – Eliminate Reverse Engineering with Obfuscation
eFPGA technology serves as a powerful security mechanism for ASICs, providing robust protection against reverse engineering, intellectual property theft, and unauthorized tampering. The key advantage of eFPGAs lies in their post-fabrication programmability, which introduces a critical element of uncertainty into otherwise fixed ASIC designs. When IP is implemented on an eFPGA, it becomes inherently obfuscated due to the non-volatile, programmable nature of the technology. This security feature delivers significant protection because if an adversary physically deconstructs an ASIC, they will only encounter an unprogrammed matrix of configurable logic gates, making it impossible to determine the intended functionality. Additionally, eFPGA technology can effectively obscure internal routing paths – shielding critical hardware components – and disable external interfaces to prevent unauthorized access to internal circuitry. This comprehensive protection also delivers the substantial benefit of preventing unauthorized cloning and overproduction of your ASIC designs.
Solution #6 – Enable SW Crypto Agility with HW/SW Co-Design
A way to reduce the impact of eFPGA area in an ASIC is to implement cryptography algorithms in software while offloading only the most computationally intensive functions that would otherwise slow down processor performance. Consider our collaborative project with PQSecure as an example. In this design, we divided the XMSS cryptography algorithm strategically: the processor handles dataflow and memory management, while the eFPGA specifically accelerates the complex lattice-based functions. This approach delivers performance nearly equivalent to a full hardware implementation while reducing eFPGA die area by approximately 25%. An additional benefit is that algorithm control remains in the software domain, keeping it accessible to software engineers.
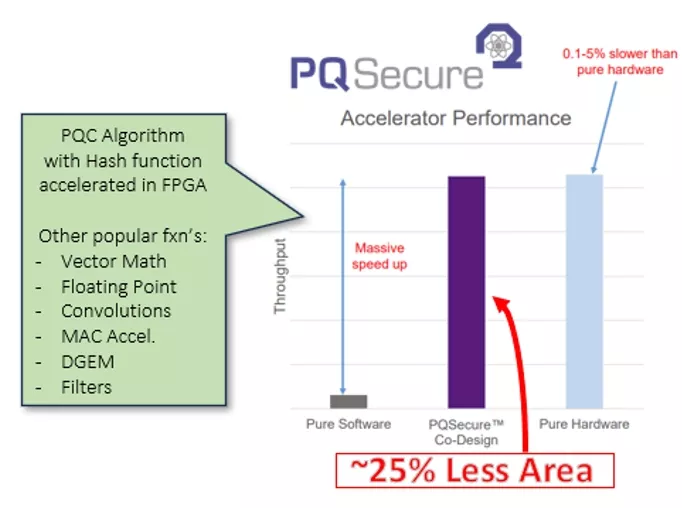
Figure 5: An XMSS Algorithm Accelerated with HW/SW Co-Design
Many tools are available for profiling software and implementing complex functions in hardware. For more information on this, please reach out to us. We have proven solutions with Siemens Catapult, Codasip and Andes Tech CoPilot.
Solution #7 – Added co HW/SW OS authentication and security at Ring 0 CPU level
Another way to strengthen security is by implementing CPU-based authentication for operating system tasks. In this approach, when the OS initiates a task switch, the CPU transitions into privileged/Supervisor mode. Within this protected state, specialized instructions stored in the eFPGA can execute authentication protocols using rolling keys. These protocols verify the legitimacy of task switches and confirm that task control blocks (TCBs) remain untampered. This security framework extends beyond basic task management to include Inter-Process Communications (IPC) mechanisms like memory pools and pipes. Because the eFPGA operates within the CPU’s highest privilege level (RING 0), it creates a secure binding between the operating system and the CPU. The eFPGA’s bitstream configuration adds yet another security layer to this architecture.
Solution #8 – Unique IP Identifier – Watermark and Blockchain

Each Menta eFPGA IP is specifically tailored to individual customer implementations and is securely tracked using a unique blockchain ID and certificate. This ensures complete isolation between implementations and superior security by generating a distinct bitstream for every IP instance – making it virtually impossible for unauthorized parties to reverse-engineer or compromise the FPGA design.
Solution #9 – Instantaneous Mitigation to Tamper Detection
Menta’s eFPGA configuration utilizes a D Flip Flop scan chain rather than custom cells or SRAM. This approach provides numerous advantages for testing, reliability, aging, and yield since these standard cells inherit the proven characteristics of the specific fabrication facility used for IC production. Regarding security, this design offers a crucial benefit: the D Flip Flop scan chain can be completely reset with a single clock cycle. This capability proves extremely valuable when malicious attacks are detected, as the entire FPGA design can be instantaneously erased, interfaces disabled, and even the complete ASIC shut down—effectively safeguarding data and firmware from unauthorized access or tampering.
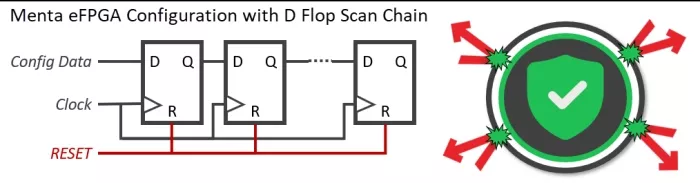
Figure 6 : Immediate Tamper Detection Mitigation with Menta eFPGA IP
Conclusion
As we’ve demonstrated in this paper, incorporating embedded FPGA intellectual property into your ASIC or SoC provides substantial security advantages that cannot be achieved through alternative methods. Designers who rely exclusively on processor-based software solutions may soon discover their products are susceptible to attacks. Our analysis clearly shows that the investment required to implement adaptable hardware using Menta eFPGA technology is significantly less than the potential costs of security breaches—particularly as we observe increasing financial penalties emerging from regional regulatory requirements. We trust these nine key points have clarified the essential security considerations you should be addressing today and demonstrated how Menta eFPGA technology can effectively support your security implementation strategy.
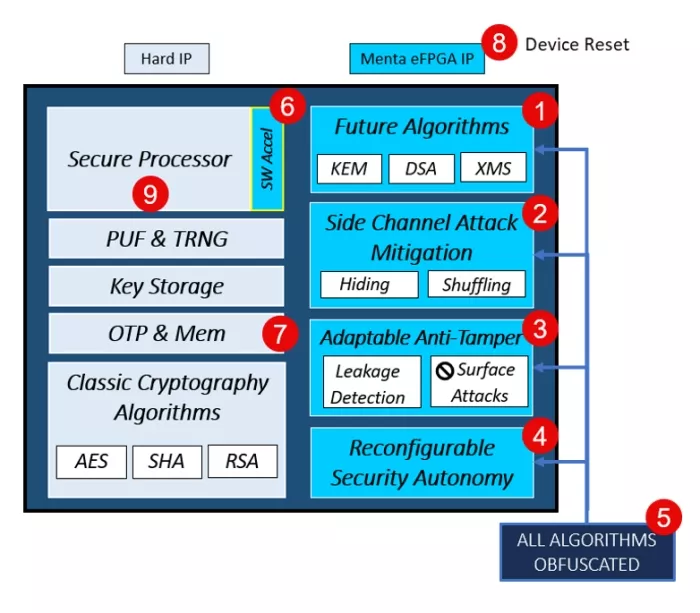
Figure 7: Agile Cryptography Controller Architecture enabled by Menta eFPGA
And let’s not forget that this intellectual property can handle multiple tasks by alternating between different applications over time. For example, one moment it can run an authentication algorithm, then switch to key encapsulation, followed by decryption, and then compression. With adaptable hardware, you can respond effectively to any challenge that comes your way! Want to learn more, reach out to us today!
About Menta
Menta, a privately held company, provides 100% third-party standard-cell embedded FPGA intellectual property (IP) for system-on-chip (SoC), application-specific integrated circuit (ASIC) and application-specific standard product (ASSP) designs. Our innovative technology allows users to easily update silicon post-production, whether to fix a bug, implement customer-specific features, adapt to evolving standards or enhance security. Menta’s IPs are delivered with the Origami toolchain, which generates the bitstream directly from register transfer level (RTL), including synthesis.
Related Semiconductor IP
- eFPGA Soft IP
- eFPGA on GlobalFoundries GF12LP
- eFPGA IP — Flexible Reconfigurable Logic Acceleration Core
- Heterogeneous eFPGA architecture with LUTs, DSPs, and BRAMs on GlobalFoundries GF12LP
- Radiation-Hardened eFPGA
Related Articles
- Seven Powerful Reasons Why Menta eFPGA Is the Clear Choice for A&D ASICs
- Add Security And Supply Chain Trust To Your ASIC Or SoC With eFPGAs
- Why FIR sensing technology is essential for achieving fully autonomous vehicles
- Top 5 Reasons why CPU is the Best Processor for AI Inference
Latest Articles
- GenAI for Systems: Recurring Challenges and Design Principles from Software to Silicon
- Creating a Frequency Plan for a System using a PLL
- RISCover: Automatic Discovery of User-exploitable Architectural Security Vulnerabilities in Closed-Source RISC-V CPUs
- MING: An Automated CNN-to-Edge MLIR HLS framework
- Fault Tolerant Design of IGZO-based Binary Search ADCs