ML-KEM explained: Quantum-safe Key Exchange for secure embedded Hardware
1. Introduction
Every reliable system starts with security. From IoT devices sending data to the cloud, to automotive ECUs verifying their identity, to industrial machines coordinating in real time, all depend on cryptographic keys that are generated, stored, and exchanged safely.
In the future cryptographic algorithms that protect today's systems will be threatened by quantum computers. RSA and ECC, used in protocols such as TLS, IPSec, and MACsec, will no longer be secure as quantum computers become more advanced.
For embedded system developers developing systems with a lifespan of 5 to 20 years, this is not a future issue, but a design requirement of today. The solution: Post-Quantum Cryptography (PQC).
This article explains ML-KEM, the new NIST standard for quantum-secure key exchange, and shows how KiviCore's IP cores enable the integration of PQC into FPGA-based embedded systems, even with limited resources.
2. Why Key Exchange matters in embedded Systems
A cryptographic key is more than just a random number. It is a fundamental element that enables confidentiality (only the intended recipient can read the data), authenticity (verification of the data source), and integrity (ensuring that data has not been altered).
There are two main types of keys:
- Symmetric keys use the same key for encryption and decryption on both sides. They are fast and efficient, but require that both parties securely share the key in advance.
- Asymmetric keys use public/private key pairs that are mathematically linked. Although they are slower, they solve the problem of secure secret sharing and also enable digital signatures for authentication.
The problem: When two parties communicate over an open network, they must first agree on a shared secret key. Without a secure method of key exchange, attackers could obtain the shared key and view and tamper with all encrypted data. Public-key cryptography solves this problem by enabling two parties to generate a secret key over an insecure channel.
3. How Key Exchange works Today
For decades, secure communication has been based on two main approaches relying on mathematical problems.
- RSA (Rivest-Shamir-Adleman) is based on the difficulty of factoring large prime numbers.
- Diffie-Hellman algorithms: Particularly the Elliptic Curve Diffie-Hellman (ECDH). ECDH is based on the discrete logarithm problem in Diffie-Hellman.
With ECDH, the process begins with the generation of an asymmetric key: Each participant first creates a public/private key pair and keeps the private key secret while sharing the corresponding public key with the other participant. Having exchanged public keys, each participant can generate the same secret key using their private key and the other participant's public key.
4. From classic to Post-Quantum resilient Key Exchange
Quantum computing poses an immediate threat to today’s security. With Shor’s algorithm (quantum computer algorithm that can solve prime factors of an integer in polynomial time), future quantum computers will break RSA- and ECDH-based key exchanges, making current encrypted communications vulnerable. This is not a distant risk. The “collect now, decrypt later” attack allows adversaries to record encrypted data today and decrypt it once quantum capabilities arrive. For systems with long lifecycles, like cars, industrial machines, and critical infrastructure, data secured now must remain protected for decades.
To address this, NIST launched a global initiative to standardize quantum-resistant algorithms. For key exchange, the winner is CRYSTALS-Kyber, now formalized as ML-KEM (Module-Lattice-based Key Encapsulation Mechanism) under the NIST FIPS 203 standard. Governments, industries, and standardization bodies (ISO, ETSI, IETF) are coordinating migration efforts. In Europe for instance, the roadmap recommends:
- 2026: Planning & pilot projects
- 2030: Critical infrastructure quantum-secure
- 2035: Full migration completed
The need for PQC is directly related to upcoming security regulations such as the Cyber Resilience Act (CRA). The CRA requires manufacturers to implement state-of-the-art security measures throughout the entire product lifecycle. As quantum computers are expected to break traditional algorithms such as RSA and ECC, PQC is anticipated to become the new state-of-the-art technology and thus become a mandatory requirement for compliance.
The shift to PQC is already underway. It is crucial to prepare early in order to ensure long-term data security in the quantum era.
5. How PQC ML-KEM works
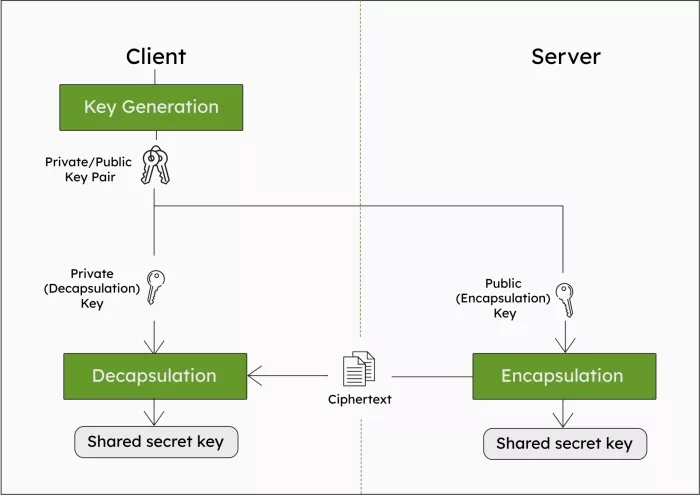
ML-KEM allows two devices to securely agree on a shared key over an insecure channel. The process involves three main operations:
- Key Generation (KeyGen): The client generates a public/private key pair. The public key (encapsulation key) is shared with the server. The private key (decapsulation key) is kept secret.
- Encapsulation (Encaps): The server uses the client’s public key to generate a random shared secret and a ciphertext. Then the server sends the ciphertext to the client.
- Decapsulation (Decaps): The client uses their private key to recover the same shared secret. Both devices now hold an identical key for symmetric encryption.
NIST defines three parameter sets for different use cases:
- ML-KEM-512: Smallest footprint, highest performance
- ML-KEM-768: Balanced for most applications
- ML-KEM-1024: Maximum security for long-lived systems
6. KiviPQC IP Core for Key Exchange
The KiviPQC-KEM is a hardware accelerator implementing the ML-KEM , a post-quantum cryptographic standard defined by NIST FIPS 204. It supports all parameter sets specified in the standard.
Easy to integrate
The integration of the KiviPQC-KEM IP into any SoC or FPGA design is fast and straightforward. The IP core is LINT-clean, reusable, and built for easy system integration. The communication with the host system is managed by an AMBA® AXI4-Lite interface.
A platform-agnostic C API and a comprehensive reference software package simplifies software integration and testing. Detailed documentation guides developers through the entire integration and implementation process.
All KiviCore IP cores are developed in Germany. For evaluation they are instantly available via online delivery. Dedicated web support (typically responding within 8 business hours) ensures a smooth transition from delivery to integration, implementation, and evaluation.
Minimal logic utilization
KiviPQC-KEM is engineered specifically for area-constrained and performance-critical designs. Unlike typical PQC implementations that rely on large parallel arithmetic units and extensive memory, KiviCore’s architecture employs sequential computation and highly optimized logic paths to deliver minimal resource utilization without sacrificing security. Designed as a self-contained cryptographic engine, it inherently reduces the attack surface and provides built-in protection against timing-based side-channel attacks, ensuring robust security even in compact FPGA environments.
KiviPQC-KEM is available in two configurations:
- KiviPQC-KEM-Tiny: Optimized for minimal logic resource utilization
- KiviPQC-KEM-Fast: Optimized for fast processing
7. Conclusion
Quantum computing is reshaping the foundation of digital security and the transition to post-quantum cryptography is no longer optional. For FPGA-based embedded systems, ML-KEM provides the essential building block for secure key exchange in a quantum-safe world.
However, implementing PQC efficiently poses a real engineering challenge. This requires careful balancing of performance, area, and power, while also maintaining resistance against new attack vectors.
This is where KiviCore steps in. The KiviPQC-KEM IP core provides a compact, and secure implementation of ML-KEM that can be seamlessly integrated into existing FPGA and SoC architectures. It is easy to integrate, resource-efficient, and fully supported enabling developers to progress swiftly from evaluation to production.
With regulations such as CRA calling for cutting-edge security throughout product lifecycles, PQC is set to become a compliance requirement. By integrating KiviPQC-KEM now, developers can be sure that their designs will remain compliant and secure in the quantum era.
Related Semiconductor IP
- Post-Quantum Key Encapsulation IP Core
- ML-KEM Key Encapsulation & ML-DSA Digital Signature Engine
- Post-Quantum ML-KEM IP Core
- xQlave® ML-KEM (Kyber) Key Encapsulation Mechanism IP core
- ML-KEM Key Encapsulation IP Core
Related Blogs
- ML-DSA explained: Quantum-Safe digital Signatures for secure embedded Systems
- Embedded Security explained: IPsec and IKEv2 for embedded Systems
- HDCP 2.2: Authentication and Key Exchange (AKE)
- Secure Development Lifecycle for Hardware Becomes an Imperative
Latest Blogs
- The Memory Imperative for Next-Generation AI Accelerator SoCs
- Leadership in CAN XL strengthens Bosch’s position in vehicle communication
- Validating UPLI Protocol Across Topologies with Cadence UALink VIP
- Cadence Tapes Out 32GT/s UCIe IP Subsystem on Samsung 4nm Technology
- LPDDR6 vs. LPDDR5 and LPDDR5X: What’s the Difference?
