Trust at the Core: A Deep Dive into Hardware Root of Trust (HRoT)
While it may not get as much attention as its software counterparts, hardware security is vitally important in modern systems. It plays an essential role in establishing trust, protecting sensitive data, and enhancing system performance.
At the heart of hardware security is Hardware Root of Trust (HRoT), which lays the groundwork for system protection. Despite its importance, the core functions and role of HRoT within modern security architectures remain widely misunderstood.
Why Hardware Root of Trust matters
As the connectivity and scale of modern applications and devices — from IoT and AI systems to software-defined vehicles and government platforms — continue to expand, the volume and sophistication of cyber threats are also increasing. A Hardware Root of Trust is a critical component in defending against these threats.
Embedded at the silicon level, HRoT provides a secure foundation for all other security operations within a system. It ensures that even in the presence of potential vulnerabilities, the system can operate in a trusted environment.
The importance of HRoT lies in its ability to:
- Prevent unauthorized access: By verifying the authenticity of the requestor, HRoT ensures only trusted entities can interact with the system.
- Protect sensitive information: HRoT safeguards cryptographic keys, credentials, and other critical data from being exposed or tampered with.
- Mitigate IP theft: By securing intellectual property at the hardware level, HRoT helps protect the competitive edge of chip manufacturers and device makers.
Without a robust HRoT, systems are vulnerable to a range of attacks, from firmware tampering to cryptographic key extraction. In essence, HRoT acts as the trust anchor that underpins the entire security framework of a device.
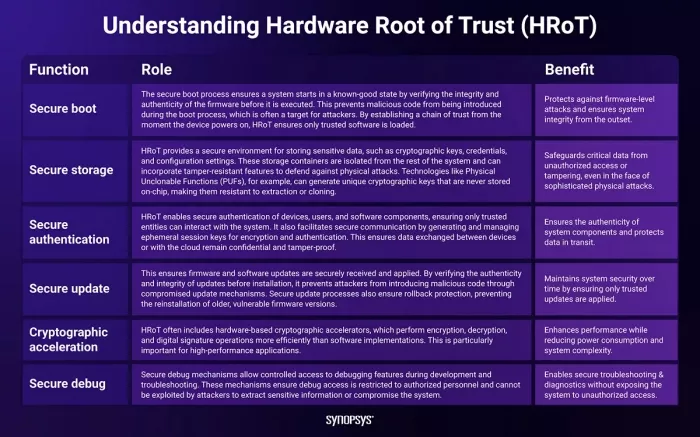
Core functions of a Hardware Root of Trust
At the heart of an HRoT are several critical functions, spanning system boot, data storage, authentication (of devices, users, and software components), firmware and software updates, access to debug features, and even cryptographic acceleration.
By integrating these core functions, HRoT provides a robust foundation for securing devices throughout their lifecycle, addressing both software and hardware threats.
Synopsys HRoT solutions: tRoot and SRAM PUF
Synopsys offers industry-leading solutions to implement HRoT in modern systems. Our tRoot Hardware Secure Modules (HSMs) provide a flexible and highly configurable HRoT solution that integrates seamlessly into a variety of applications, from IoT devices to automotive systems.
In addition to tRoot, our SRAM Physical Unclonable Function (PUF) technology provides a unique and secure way to generate device-specific cryptographic keys. By leveraging the inherent physical variations in silicon, SRAM PUF creates keys that are unique to each device and do not need to be stored in memory, further enhancing security.
Together, these solutions enable chip manufacturers and device makers to implement a strong HRoT that provides exceptional protection against modern cybersecurity threats.
Building a fortress for the future
In an era where connected devices are ubiquitous and cyber threats are continuously evolving, the need for a robust security foundation has never been greater. A Hardware Root of Trust serves as the cornerstone of this foundation, providing the trust, protection, and performance required to secure modern systems.
By integrating HRoT into designs, organizations can ensure their devices are not only secure but also adaptable to future challenges. Whether it’s protecting IoT devices, enabling secure automotive systems, or safeguarding government applications, HRoT is the key to building a fortress that stands the test of time.
As we continue to innovate with solutions like tRoot and SRAM PUF, the path to secure, trusted systems becomes clearer. Trust begins here — with a Hardware Root of Trust.
Related Semiconductor IP
- tRoot V023 FS Hardware Secure Module, ASIL-B compliant (w/ ARC EM22FS)
- tRoot Vx Hardware Secure Modules
- tRoot V500 Hardware Secure Module
- tRoot F004 Hardware Secure Module (w/ ARC EM4)
- Root of Trust
Related Blogs
- Hardware Root of Trust: Everything you need to know
- Rambus and the OCP: Tackling Cloud Data Security with a Hardware Root of Trust
- Rambus RT-660 Root of Trust IP Achieves FIPS 140-3 Certification
- Rambus CryptoManager Root of Trust Solutions Tailor Security Capabilities to Specific Customer Needs with New Three-Tier Architecture
Latest Blogs
- The Memory Imperative for Next-Generation AI Accelerator SoCs
- Leadership in CAN XL strengthens Bosch’s position in vehicle communication
- Validating UPLI Protocol Across Topologies with Cadence UALink VIP
- Cadence Tapes Out 32GT/s UCIe IP Subsystem on Samsung 4nm Technology
- LPDDR6 vs. LPDDR5 and LPDDR5X: What’s the Difference?