Cryptography IP
Welcome to the ultimate Crypto Accelerator IP hub! Explore our vast directory of Crypto Accelerator IP
All offers in
Cryptography IP
Filter
Compare
346
Cryptography IP
from
57
vendors
(1
-
10)
-
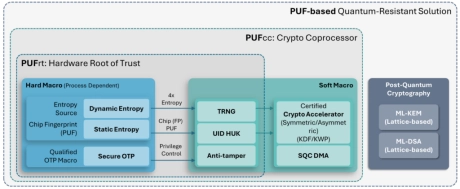
PUF-based Post-Quantum Cryptography (PQC) Solution
- PUFsecurity is proud to pioneer the world’s first PUF-based Post-Quantum Cryptography (PQC) solution, delivering cutting-edge, hardware-level security that sets a new standard.
- Our innovative solution integrates PUF technology with quantum-resistant cryptographic algorithms, ensuring robust key protection and seamless transition to a quantum-secure future.
-
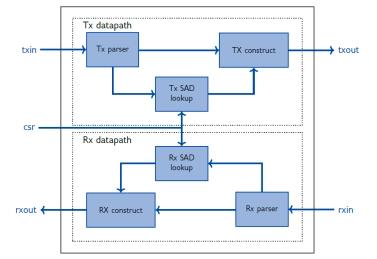
IPSEC AES-256-GCM (Standalone IPsec)
- XIP7213E implements the Internet Protocol Security (IPsec) as standardised in RFC4303 and RFC4305.
- The IPsec protocol defines a security infrastrucure for Layer 3 (as per the OSI model) traffic by assuring that a received packet has been sent by the transmitting station that claimed to send it.
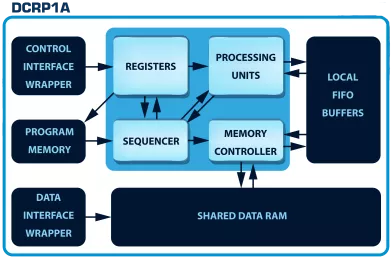
-
100% Secure Cryptographic System for RSA, Diffie-Hellman and ECC with AMBA AHB, AXI4 and APB
- The DCRP1A - CryptOne IP is a 100% secure cryptographic system
- CryptOne is a fully scalable, hardware-accelerated cryptographic system
- Designed for next-generation SoCs, FPGAs, and secure embedded systems, it delivers 100% secure asymmetric cryptography acceleration for demanding applications.
-
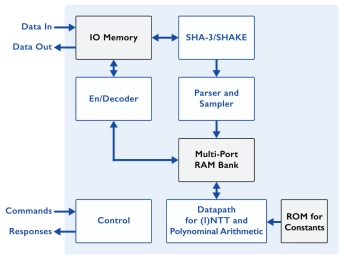
xQlave® ML-KEM (Kyber) Key Encapsulation Mechanism IP core
- Quantum-resistant key exchange for future-proof security
- Compliant with NIST's ML-KEM standard
- Pure RTL without hidden CPU or software components
- Optimised architecture with constant-time execution
-
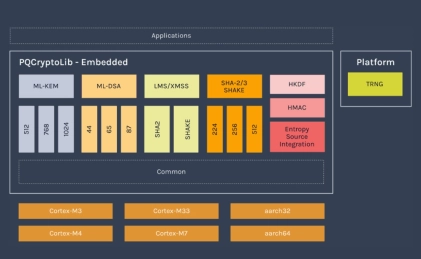
Highly-optimized PQC implementations, capable of running PQC in under 15kb RAM
- PQCryptoLib-Emebedded is a versatile, CAVP-ready cryptography library designed and optimized for embedded devices.
- With its design focused on ultra-small memory footprint, PQCryptoLib-Embedded solutions have been specically designed for embedded systems, microcontrollers and memory-constrained devices. It provides a PQC integration to devices already in the field.
-
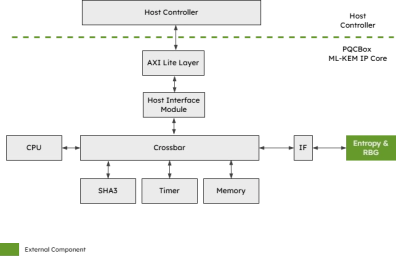
Post-Quantum Key Encapsulation IP Core
- The PQC-KEM is an IP Core for ML-KEM Key Encapsulation that supports key generation, encapsulation, and decapsulation operations for all ML-KEM variants standardized by NIST in FIPS 203.
- ML-KEM is a post-quantum cryptographic (PQC) algorithm, designed to be robust against a quantum computer attack.
-
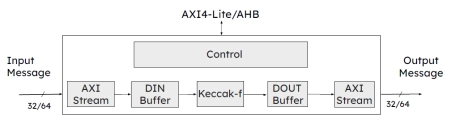
SHA-3 Crypto IP Core
- The SHA-3 – secure hash algorithms – crypto engine is a hardware accelerator for cryptographic hashing functions.
- It is an area efficient and high throughput design and compliant to NIST’s FIPS 202 standard.
- Additionally it supports all SHA-3 hash functions – SHA-3-224, SHA-3-256, SHA-3-384 and SHA-3-512 – as well as extendable output functions (XOF) – SHAKE-128 and SHAKE-256.
-
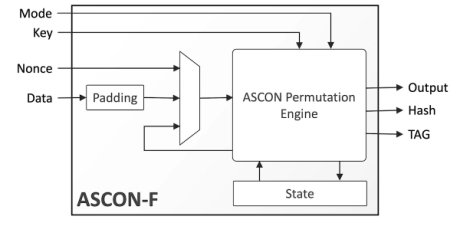
ASCON Authenticated Encryption & Hashing Engine
- The ASCON-F IP core is a compact, high-throughput hardware engine implementing the lightweight authenticated encryption with associated data (AEAD) and hashing algorithms described in the Ascon v1.2 specification.
- A single instance of the ASCON-F IP core can encrypt or decrypt data using the Ascon-128 and Ascon-128a functions or perform Cryptographic hashing Hash per the Ascon-Hash and Ascon-Hasha functions.
-
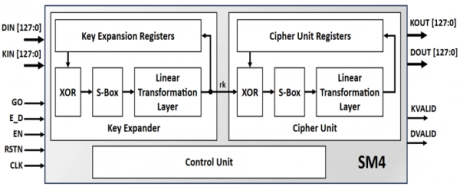
SM4 Cipher Engine
- The SM4 IP core implements a custom hardware accelerator for the SM4 symmetric block cipher, specified in Chinese national standard GB/T 32907-2016, and ISO/IEC 18033-3:2010/Amd 1:2021.
- Designed for easy integration, the core, internally expanding the 128-bit key, is capable of both encryption and decryption and features a simple handshake input and output data interface.
-
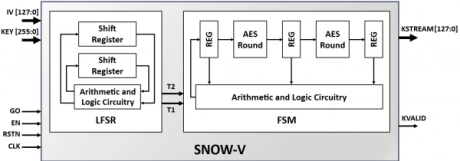
SNOW-V Stream Cipher Engine
- The SNOW-V IP core implements the SNOW-V stream cipher mechanism, aiming to meet the security demands of modern high-speed communication systems.
- It conforms to the official SNOW-V mechanism, published in 2019 by the IACR Transactions on Symmetric Cryptology, as an extensive revision of SNOW 3G stream cipher.