Root of Trust IP
Welcome to the ultimate Root of Trust IP hub! Explore our vast directory of Root of Trust IP
All offers in
Root of Trust IP
Filter
Compare
36
Root of Trust IP
from
11
vendors
(1
-
10)
-
Highly configurable HW PQC acceleration with RISC-V processor for full CPU offload
- Highly configurable HW PQC acceleration with RISC-V processor for full CPU offload, configurable as Subsystem or RoT, with SCA and FIA protection
- Engineered for crypto and implementation agility, PQPlatform-TrustSys is optimized for PQ/T hybrid secure boot and features industry-leading protections against power, EM, and fault-injection attacks.
-
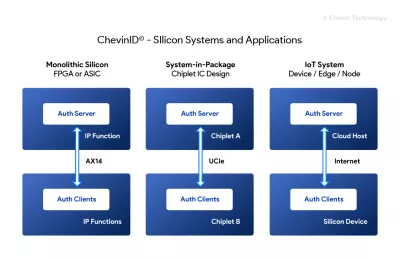
Silicon Security Solution
- Secure Root of Trust
- Protect against cyber hacks, copying, cloning, trojans
- Flexible management and Upgrade path for features
- Reduced complexity with software keys
-
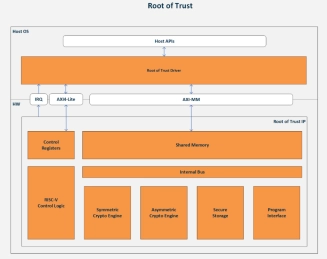
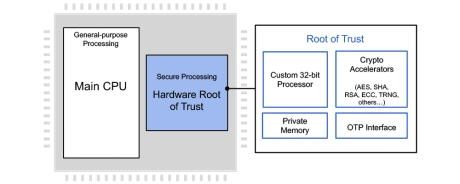
Root of Trust
- Root of Trust IP is a Hardware Secure Module (HSM) solution that provides the security foundation for processors and System on Chips (SoCs).
- It protects critical systems especially devices used in automotive, industrial, cloud, data center, and wireless applications.
-
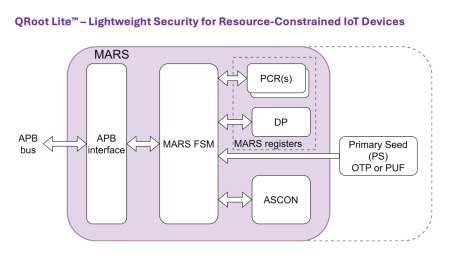
Lightweight and Configurable Root-of-Trust Soft IP
- QRoot Lite™ is a silicon IP solution designed specifically for resource-constrained MCUs and IoT devices. It provides essential security capabilities including secure boot, device attestation, and sealed storage.
- Built on the industry-standard TCG MARS specification, QRoot Lite™ simplifies integration, reduces costs, and accelerates your journey toward regulatory compliance and trusted embedded products.
-
nQrux™ Crypto Module
- Compatible with applicable NIST, IETF, and IEEE standards, RFCs, and test vectors for compliance and certification programs

-
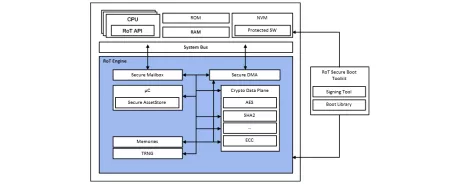
Root of Trust - Foundational security in SoCs and FPGAs for IoT clients and sensors
- Secure Boot assist to host CPU(s) and protection of key material
- Secure firmware upgrade management for Host CPU
- Lifecycle management support
- Secure Debug support
- Secure device authentication and identity protection
-
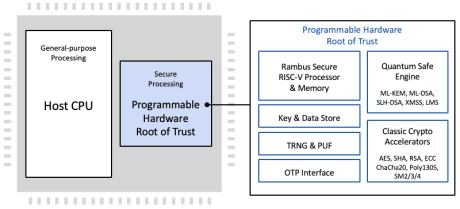
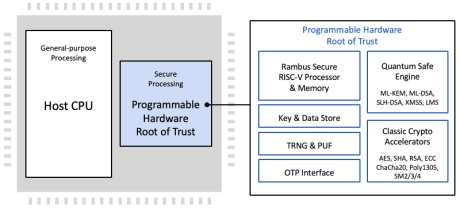
Programmable Root of Trust with Quantum Safe Cryptography acceleration
- The CryptoManager RT-6xx family protects against a wide range of hardware and software attacks through state-of-the-art side channel attack countermeasures and anti-tamper and security techniques.
- The RT-6xx supports various security certifications up to level 3. The RT-6×4 Root of Trust adds Quantum Safe Encryption (QSE) to provide a future-proof hardware security solution to protect data center assets starting today and into the quantum era.
-
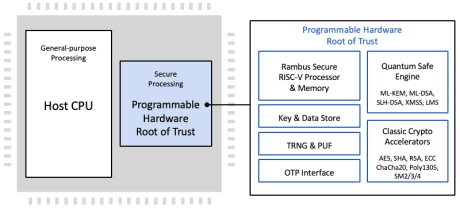
Quantum Safe, ISO 21434 Automotive-grade Programmable Hardware Security Module
- The automotive-grade CryptoManager RT-7xx v3 Root of Trust family is the next generation of fully programmable ISO 26262 and ISO 21434 compliant hardware security modules offering Quantum Safe security by design for secure automotive applications.
- The CryptoManager RT-7xx family protects against a wide range of hardware and software attacks through state-of-the-art side channel attack countermeasures and anti-tamper and security techniques.
-
Embedded Hardware Security Module (Root of Trust) - Automotive Grade ISO 26262 ASIL-B
- The RT-64x Embedded Hardware Security Module (Root of Trust) family are fully programmable, ISO 26262 ASIL-B hardware security cores offering security by design for automotive applications.
- They protect against a wide range of failures such as permanent, transient and latent faults and hardware and software attacks with state-of-the-art anti-tamper and security techniques.
-
Programmable Root of Trust with Quantum Safe Cryptography acceleration, DPA-resistant & FIA-protected cryptographic accelerators and Caliptra RoTM
- The CryptoManager RT-6xx v3 Root of Trust family from Rambus is the latest generation of fully programmable FIPS 140-3 compliant hardware security cores offering Quantum Safe security by design for data center and other highly secure applications.
- Device and system architects face a growing array of security threats, including the threat of quantum computers. Across applications, one constant is the need for a hardware Root of Trust-based security implementation.