Other
All offers in
Other
Filter
Compare
39
Other
from
21
vendors
(1
-
10)
-
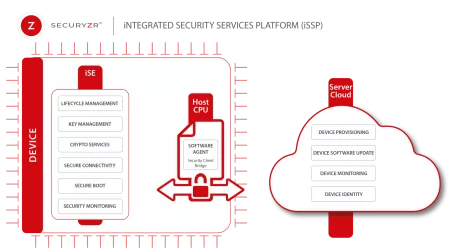
Integrated Security Services Platform (iSSP)
- The Securyzr™ iSSP (integrated Security Services Platform) enables Secure-IC customers and partners to supply, deploy and manage the embedded security of their devices’ fleet all along their lifecycle.
- The Securyzr™ iSSP is an easy & trustful end-to-end solution for zero-touch security lifecycle services such as provisioning, firmware update, security monitoring & device identity management.
-
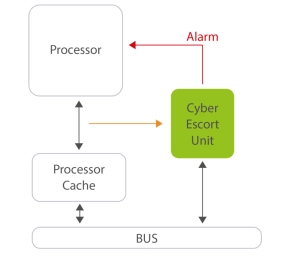
Cyber Escort Unit IP: Bridging Software and Hardware Security Gaps
-
The Cyber Escort Unit is designed to fill the security gap between software cyber security and hardware by escorting step by step the program execution to achieve high execution performances in a secure way, allowing advantageously real-time detection of zero-day attacks. Unique on the market, this product builds the foundation for hardware-enabled cybersecurity
-
-
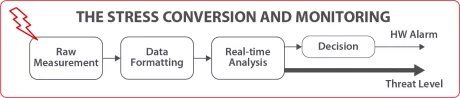
Digital Fault Injection Attack Detector
- Unlike analog sensors which are dedicated to the detection of a specific perturbation attack, the Digital Sensor is designed to detect various threats belonging to the family of Fault Injection Attacks (FIA)
-
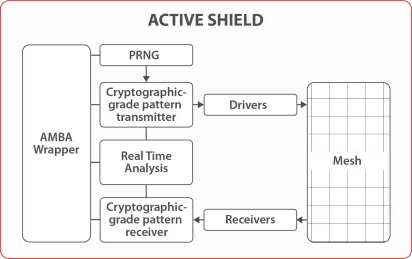
Active Shield
- Anti-tamper solution with a mesh placed over the sensitive parts of the circuit and actively monitored
- Uses random cryptographically generated patterns to detect integrity violations
- Antenna-effect safe
- Security certification ready (incl. Common Criteria)
-
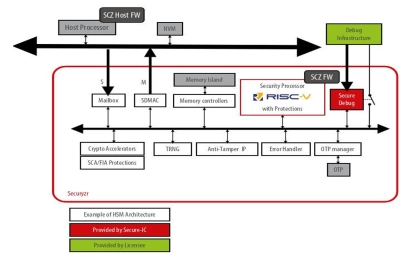
Secure Debug Hardware IP
- Based on challenge response authentication.
- Can be interfaced with already existing cryptographic engines.
- Fully digital and designed with the standard cells library.
- Transferable to any design kit.
-
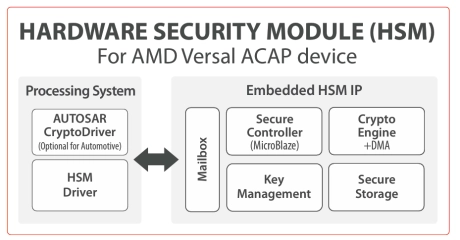
Hardware Security Module (HSM) for AMD Xilinx Versal ACAP device
- The HSM IP module is a Hardware Security Module for a wide range of applications.
- It is developed according to the guidelines set out by the EVITA project and is meant to be implemented on a AMD Xilinx Versal ACAP device.
- It supports TrustZone.
-
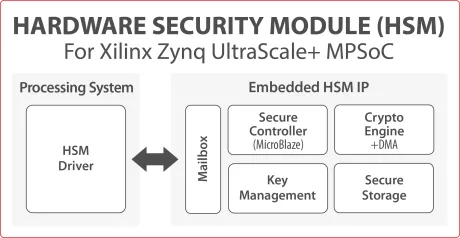
Hardware Security Module (HSM) for Xilinx Zynq UltraScale+ MPSoC platform
- The HSM IP module is a Hardware Security Module for a wide range of applications.
- It is developed, validated and licensed by Secure-IC (partner of Xilinx) as an FPGA-based IP solution dedicated to the Xilinx Zynq UltraScale+ MPSoC platform.
-
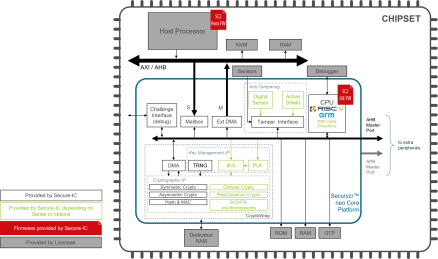
Root of Trust solutions
- Securyzr™ integrated Secure Element (iSE) is Secure-IC Root of Trust solution.
- Embedded in the main SoC, it offers multiple services to its host system: provisioning, secure boot, secure firmware update, cryptographic services, multiple protections, etc.
-
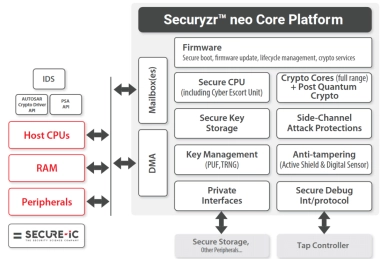
Securyzr™ neo Core Platform
- Securyzr™ neo Core Platform is Secure-IC’s enhanced version of its flagship offering Securyzr™ integrated Secure Element (iSE) Series.
- Thanks to its common platform, the entire Securyzr™ neo Series is now faster and more optimized than ever.
- With an optimal Power Performance Area (PPA), Secure-IC is offering a more comprehensive and mature solution to address all security needs from the different applications: spanning from IoT, Factory Automation, AIoT, Automotive, Cloud & Datacenter, to Mobile.
-
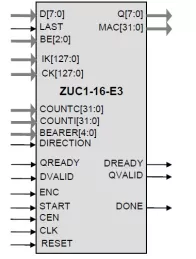
Ultra-Compact 3GPP Cipher Core
- Keystream generation using the ZUC Algorithm version 1.6 (ZUC-2011)
- High throughput: up to 40 Gbps in 65 nm process, 10 Gbps in Altera Stratix III
- Small size: from 7.5K ASIC gates
- Satisfies ETSI SAGE ZUC and EAE3/EIA3 specifications