PUF (Physical Unclonable Function)
Welcome to the ultimate Physical Unclonable Function (PUF) IP hub! Explore our vast directory of Physical Unclonable Function (PUF)
All offers in
PUF (Physical Unclonable Function)
Filter
Compare
16
PUF (Physical Unclonable Function)
from
8
vendors
(1
-
10)
-
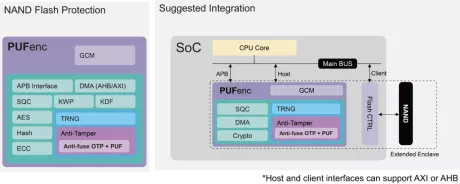
External NAND flash protection, designed to secure stored assets with a local key from PUF
- PUFenc is designed to protect external flash memory and its stored assets.
- The IP provides asset encryption, such as a learning model for AI or firmware for the chip with a local key from the PUF.
- It adds an additional layer of security by avoiding using the global key, which is a shared key among ICs after the chip leaves the manufacturing floor.
-
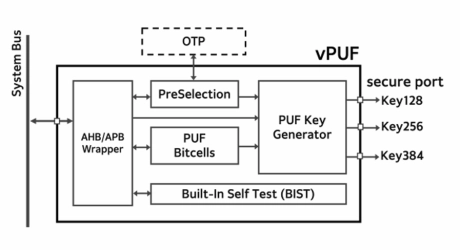
Via-PUF Security Chip for Root of Trust
-
The vPUF® IP, powered by Via PUF (Physically Unclonable Function) technology, provides a unique silicon fingerprint for inborn identity function, essential for the Root of Trust in security applications
-
-
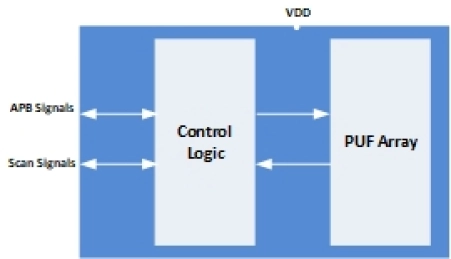
PUF Security
- A physical unclonable function, or PUF, is a "digital fingerprint" that serves as a unique identity for a semiconductor device such as a microprocessor
- PUFs are based on physical variations which occur naturally during semiconductor manufacturing, which makes it possible to differentiate between otherwise identical semiconductors
- The PUF IP consists of PUF array and control logic
-
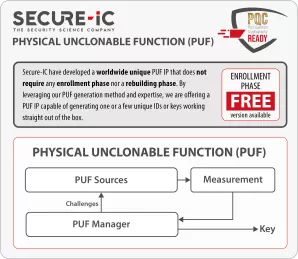
Fully Digital Physically Unclonable Function (PUF) - PQC Ready
- Secure storage without the use of any non volatile memory
- No external key provisioning required
- Does not require costly SRAM blocks
- Proven reliability regarding voltage, temperature and aging with error probability much lower than 10-9
-
Digital PUF IP
- Generate unclonable 128 or 256-bit seeds with a compact, logic-based PUF that drops into any SoC.
- Digital PUF IP adds true hardware identity for secure boot, key generation, and device authentication with minimal silicon overhead.
-
PUF IP
- Secure provisioning
- Secured identities
- High entropy seeds
- Built-in resistance to side channel attacks
-
PUF FPGA-Xilinx Premium with key wrap
- Proven “Soft” PUF implementation for AMD/Xilinx FPGAs, part of the FPGA configuration file
- Offers FPGA users a cryptographic technology to secure their own keys and to authenticate devices and communications between them on networks.
- Enables remote “brownfield” installation of hardware-based security
-
PUF FPGA-Xilinx Base
- Proven “Soft” PUF implementation for AMD/Xilinx FPGAs, part of the FPGA configuration file
- Offers FPGA users a cryptographic technology to secure their own keys and to authenticate devices and communications between them on networks.
- Enables remote “brownfield” installation of hardware-based security
- Offers key provisioning, wrapping, and unwrapping to enable secure key storage across the supply chain and for the lifetime of the device
-
ASIL-B Ready PUF Hardware Premium with key wrap and certification support
- Synopsys AP PUF is a physical unclonable function (PUF)-based RoT component that can be applied easily to almost any MCU/SoC/ASIC and is fab and process agnostic.
- This IP has been developed following an ISO 26262 functional-safety-compliant flow and meets the ISO 26262 Automotive Safety Integrity Level (ASIL) B fault metric.
-
ASIL-B Ready PUF Hardware Base
- Synopsys AP PUF is a physical unclonable function (PUF)-based RoT component that can be applied easily to almost any MCU/SoC/ASIC and is fab and process agnostic.
- This IP has been developed following an ISO 26262 functional-safety-compliant flow and meets the ISO 26262 Automotive Safety Integrity Level (ASIL) B fault metric.