ECC
All offers in
ECC
Filter
Compare
29
ECC
from
11
vendors
(1
-
10)
-
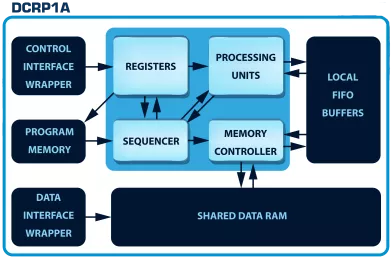
100% Secure Cryptographic System for RSA, Diffie-Hellman and ECC with AMBA AHB, AXI4 and APB
- The DCRP1A - CryptOne IP is a 100% secure cryptographic system
- CryptOne is a fully scalable, hardware-accelerated cryptographic system
- Designed for next-generation SoCs, FPGAs, and secure embedded systems, it delivers 100% secure asymmetric cryptography acceleration for demanding applications.
-
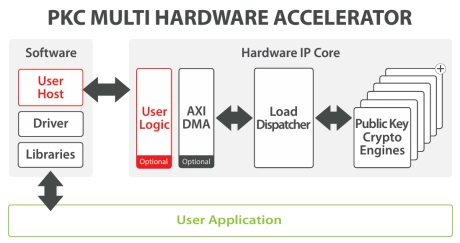
PKC Multi Hardware Accelerator IP
- The PKC Multi hardware accelerator is a secure connection engine that can be used to offload the compute intensive Public Key operations (Diffie-Hellman Key Exchange, Signature Generation and Verification), widely used for High-performance TLS Handshake.
-
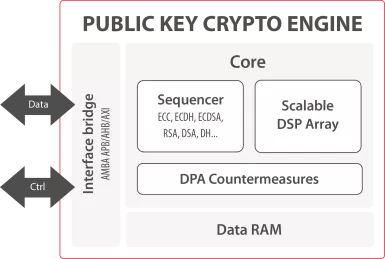
Public Key Crypto Engine
- The Public Key Crypto Engine is a versatile IP core for hardware offloading of all asymmetric cryptographic operations.
- It enables any SoC, ASIC and FPGA to support efficient execution of RSA, ECC-based algorithms and more.
- The IP core is ready for all ASIC and FPGA technologies.
-
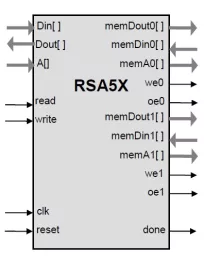
Scalable RSA and Elliptic Curve Accelerator
- The core implements the exponentiation operation of the RSA cryptography Q = Pk.
- The operands for the exponentiation: k and P as well as the modulus are programmed into the memory and the calculation is started.
- Once the operation is complete, the result Q can be read through the interface.
-
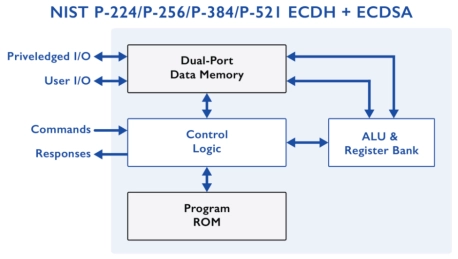
NIST P-256/P-384 ECDH+ECDSA - Compact ECC IP Cores supporting ECDH and ECDSA on NIST P-256/P-384
- Minimal Resource Requirements
- Secure Architecture
- FIPS 186-4 and SP 800-56A compliant
-
ECDSA IP Core
- ECDSA IP Cores perform digital signature generation and verification in compliance with the Elliptic Curve Digital Signature Algorithm (ECDSA) specifications defined in 'FIPS 186'.
- This standard specifies methods for digital signature generation and verification using the Elliptic Curve Digital Signature Algorithm (ECDSA).
-
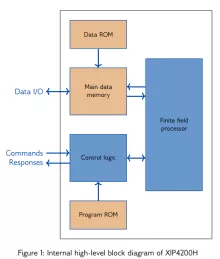
High-Speed Elliptic Curve Cryptography Accelerator for ECDH and ECDSA
- Fully digital design
- Portable to any ASIC or FPGA technology
- Fully standard compliant
- Easy to integrate
-
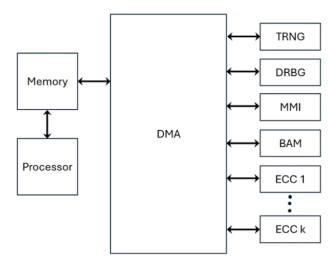
RSA/ECC Public Key Accelerators with TRNG and AHB
- Up to 4160-bit modulus size for RSA & 768-bit modulus for prime field ECC operations
- Public key signature generation, verification and key negotiation with little involvement of host
- NIST CAVP compliant for FIPS 140-3
-
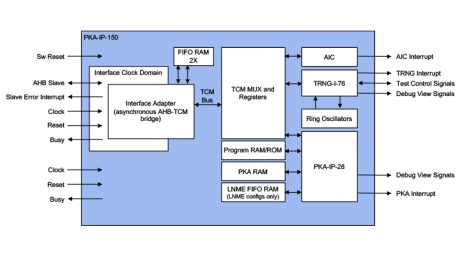
Small RSA/ECC Public Key Accelerators
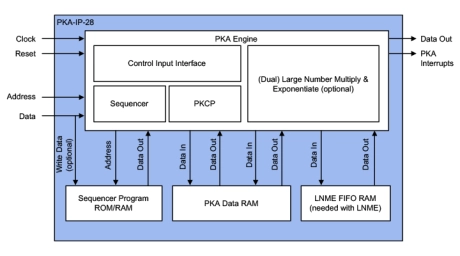
- The PKA-IP-28 is a family of Public Key Accelerator IP cores designed for full scalability and an optimal “performance over gate count” deployment.
- Proven in silicon, the PKA-IP-28 public key accelerator addresses the unique needs of semiconductor OEMs and provides a reliable and cost-effective solution that is easy to integrate into SoC designs.
-
ECC Secure Accelerator - Compact and Secure ECC IP Core for Resource-Constrained Devices
- Compact and Secure ECC IP Core for Resource-Constrained Devices