Mitigating Side-Channel Attacks In Post Quantum Cryptography (PQC) With Secure-IC Solutions
Interview with Khaled Karray, our expert on side-channel attacks
 Side-channel attacks (SCA) form an often-overlooked security vulnerability for electronic systems. However, if you want to ensure a comprehensive security, SCA protection should be part of the mix. Khaled Karray explains how Secure-IC’s IP blocks help you keep safe.
Side-channel attacks (SCA) form an often-overlooked security vulnerability for electronic systems. However, if you want to ensure a comprehensive security, SCA protection should be part of the mix. Khaled Karray explains how Secure-IC’s IP blocks help you keep safe.
Khaled Karray is our senior expert in embedded system security and side-channel attacks. After graduating in Computer Science and Telecommunications Engineering from the Tunisia Polytechnic School, he obtained a master’s degree from the University of Montpellier (France) in Microelectronics. He then enrolled in a PhD program with PSA Group (Stellantis since 2021) at the University of Paris-Saclay (Télécom ParisTech).
 He has held several positions at Secure-IC as program manager for pre-silicon security evaluation tools as well as System Level Automotive security. Khaled currently leads the Threat Analysis Business Line in charge of the development of advanced tools for evaluating hardware and software security of embedded systems.
He has held several positions at Secure-IC as program manager for pre-silicon security evaluation tools as well as System Level Automotive security. Khaled currently leads the Threat Analysis Business Line in charge of the development of advanced tools for evaluating hardware and software security of embedded systems.
At Secure-IC, he follows the latest in SCA protection and advises on how to best secure the implementations of security algorithm in the IP blocks. He also keeps an eye on new and future developments. That way, our blocks are future proof and our specialists are already preparing for next generations of SCA threats.
KHALED, FIRST THING FIRST: WHAT ARE SIDE-CHANNEL ATTACK AND WHY SHOULD PEOPLE CARE?
A SCA is a way of breaking into a computer system by exploiting physical signals that the system leaks. This is the equivalent of trying to break into a strongbox by listening to the click sounds that the mechanical lock makes in various positions.
Instead of exploiting logical weaknesses in the algorithms or implementations – the classical way of hacking – the attackers will monitor for example the variation in power consumption of a system, the electromagnetic radiation it emits, or the time it needs to execute certain cryptographic tasks. In fact, they may exploit any source of information that is not a standard input/output signal.
A SIDE-CHANNEL ATTACK IS BASED ON INFORMATION COLLECTED FROM OBSERVING THE OPERATION OF THE SYSTEM OVER A PERIOD, RATHER THAN SOME WEAKNESSES IN THE IMPLEMENTED SECURITY ALGORITHM.
With that information, they may work out information about a system: the algorithms it uses, the security measures that are applied, or even the cryptographic keys.
Simple SCAs require some technical knowledge of the internal operation of a system. However, there are also sophisticated methods that use statistical analysis of signals and that can be used as general, blackbox attacks.
HOW DO HACKERS GET ACCESS TO THE HARDWARE? YOU’D THINK THAT TODAY’S DATA CENTERS ARE ADEQUATELY PROTECTED, ALSO PHYSICALLY?
Yes, they are. There is another issue though, a huge opportunity for hackers. Networked edge devices are everywhere now, think of processors in automotive electronics, medical devices, or smart manufacturing machinery. There are now hundreds of millions of devices out there that are physically accessible to hackers. Devices that they can prob and test as much as they want. Devices that are not always so well protected and through which they could get further access to the core of an application.
Not only today’s many edge devices are vulnerable to SCAs. More complex SoCs that contain a processor and a ASIC/FPGA within the same die may also become a target. These complex SoCs often have a secured and unsecured area, which amongst others contains analog-to-digital converters that can perform power measurements. Assuming an attacker rst gained the ability to run code on the unsecure side of a device, they could then use the on-board analog-to-digital converters to capture power traces of the hardware encryption engine. That way, an advanced SCA could be staged to retrieve the secret keys.
CAN YOU WALK US THROUGH A SIDE-CHANNEL ATTACK? HOW DOES IT WORK?
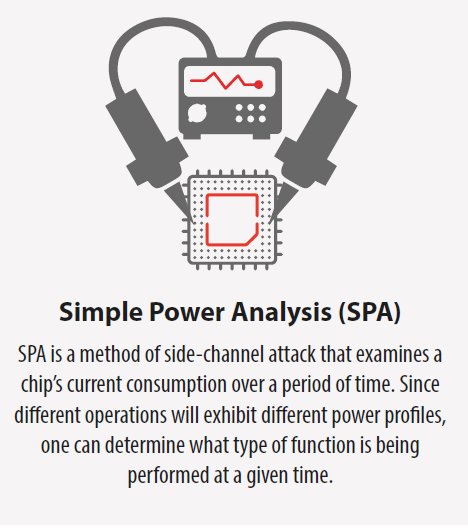
Let’s take one of the more straightforward techniques: simple power analysis (SPA). With SPA, an attacker measures the power consumption of a processor as it works through a certain computation. Let’s say the processor is processing a secret key and depending on the value of a bit, another sequence of instructions is executed. So for a 0-bit, there is sequence A, and for a 1-bit sequence B. Now if sequence A uses more or less power than sequence B, it is rather straightforward to extract information about a secret key from a simple power consumption profile.
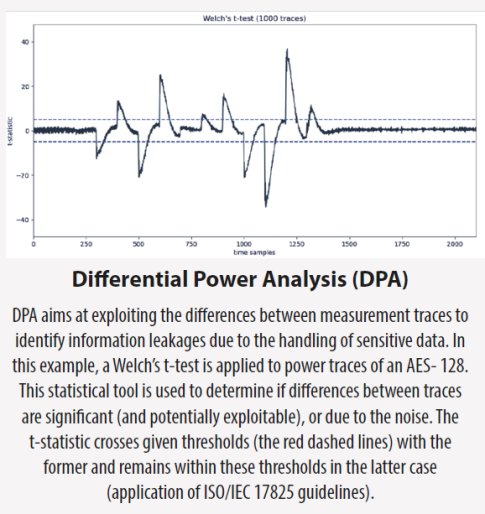
Other types of power attacks are more sophisticated. Differential Power Analysis (DPA) for example will build a power usage profile by looking at the average variations in power consumption over a number of computations. Once this prole is established, statistical methods allow to deduce information about single computations. So first the attacker makes a model predicting how the power usage profile of an average computation looks like, and then they will compute how a single computation differs from that model.
These are just two possibilities; there are many more types of SCAs, such as electromagnetic attacks, which are based on leaked electromagnetic radiation, that can directly provide plaintexts and other information. The common theme is that attackers compute information from physical signals that are leaked by hardware.
HOW CAN THESE ATTACKS BE PREVENTED?
First, for power attacks to work, attackers have to be able to distinguish the exploitable power usage from meaningless noise. It follows that a system can protect itself by adding more noise. That includes for example adding parallelism in the execution, using random delays, inserting random dummy operations, or randomly shuing operations. Those countermeasures are implementations of Secure-IC know-how and patented techniques. It will, in many cases, require a system to have a number generator that is perfectly random.
Second, the various cryptographic algorithms should be implemented in a way that they don’t expose exploitable signals. It can be done by randomizing the data processed by the algorithm with specic countermeasures (for example masking). At Secure-IC, it is one of my tasks to take a hard look at our crypto implementations to see if they are able to withstand today’s and tomorrow’s SCAs.
AT SECURE-IC, IT IS ONE OF MY TASKS TO TAKE A HARD LOOK AT OUR CRYPTO IMPLEMENTATIONS TO SEE IF THEY ARE ABLE TO WITHSTAND TODAY’S AND TOMORROW’S SIDE-CHANNEL ATTACKS.
We have to take into account that hackers have ever more sophisticated equipment at their disposal. To be secure, the countermeasures we implement should therefore make hacking much more dicult, exponentially more dicult.
WHAT DOES SECURE-IC DO TO HELP ITS CUSTOMERS BUILD SECURE PROCESSORS AND APPLICATIONS?
The bulk of our effort goes into making sure that the implementations of our crypto algorithms are hardened against today’s SCAs. We are currently concentrating on power attacks, i.e. attacks that try to collect information by measuring the power usage of a system. However, if we see that other threats become prominent, we will also tackle these (for example physical fault injections).
We harden our algorithms to make it exponentially more dicult for hackers to glean power information from our crypto modules. Whereas they could for example attack a naive implementation by taking a 1,000 power measurements, our implementations will require orders of magnitude more effort. Namely, a first-order protection require 1 million traces, a second-order protection 1 billion traces, and so on. Secure-IC masking is protected at third-order. That way, we make a power attack very hard, infeasible to execute with success in any practical way. This allows to comply to "high" attack potenttial, as per Common Criteria (namely, AVA_VAN.5), and to FIPS 140-3 appendix F.
To test our IP blocks and potentially also the boards of our customers, we have our own test lab where we can stage all sorts of SCAs against our implementations. That is key to learn how our solutions and countermeasures fare against sophisticated attacks and attack equipment that are out there today.
Of course, the knowledge about attacks and countermeasures grows over time, both at the side of the bad guys and the good guys (the security implementors like Secure-IC). It is my task to follow the field closely, give advice to the people who implement the algorithms, test the implementations, and watch out for new developments. I leverage our Virtualyzr™ tool to check for residual leakage, leveraging the methodology standardized in ISO/IEC 17825*.
In addition, Secure-IC has pioneered pre-silicon evaluation, which allows to find issues early in the design cycle with quick analyses. These evaluations are automated by the Virtualyzr™ tool and integrated into a non-regression analysis platform (SecOps). Besides, Secure-IC offers as well post-silion verification, leveraging its Analyzr™ tool, to ensure security at emulation (FPGA) and on engineering samples (ASIC).
On top of this, at Secure-IC we have a cybersecurity innovation center (Security Science Factory) that focuses on collaboration, knowledge dissemination and research as well as development and implementation of cutting-edge and advanced technologies. With our dedicated team of experts we conduct R&D activities, collaborative projects and carry out various activities to disseminate our expertise through scientific publications (more than 300 papers) and more than 200 patents, of which many of them include SCA.
WITH OUR DEDICATED TEAM OF EXPERTS WE CONDUCT R&D ACTIVITIES, COLLABORATIVE PROJECTS AND CARRY OUT VARIOUS ACTIVITIES TO DISSEMINATE OUR EXPERTISE THROUGH SCIENTIFIC PUBLICATIONS (MORE THAN 300 PAPERS) AND MORE THAN 200 PATENTS, OF WHICH MANY OF THEM INCLUDE SIDE-CHANNEL ATTACKS.
HOW DOES SIDE-CHANNEL ATTACK PREVENTION FIT IN WITH OVERALL SECURITY PROTECTION?
Perfect security doesn’t exist; securing an environment or a system requires a multilevel approach. The technological countermeasures against SCAs are only a last line of defense, and they should always be complemented with strong policies.
PERFECT SECURITY DOESN’T EXIST; SECURING AN ENVIRONMENT OR A SYSTEM REQUIRES A MULTILEVEL APPROACH.
Take for example the millions of networked edge devices, a particular attractive target for attackers. Such edge devices should never store or use master keys, as a single successful attack would compromise the whole infrastructure. Also, passwords and keys should never be shared among a community of people. And last, people shouldn’t rely on hardware being new or innovative when they assess threats. Instead, apply the principle that an adversary can eventually get access to everything except the key.
HOW ARE SIDE-CHANNEL ATTACKS CURRENTLY BEING ADDRESSED IN POST QUANTUM CRYPTOGRAPHY?
There are several techniques that can be used to improve the side-channel resistance of Post Quantum Cryptographic systems. One approach is to use software countermeasures, such as masking or blinding, to obscure the sensitive information from the attacker. Hardware-based solutions, such as physically unclonable functions (PUFs) or physically random functions (PRFs), can also be used to protect against side-channel attacks. Additionally, implementing hardware-based random number generators can help to mitigate the effect of the side-channel attack on the cryptographic implementation.
HOW IMPORTANT IS IT TO CONSIDER SIDE-CHANNEL ATTACK RESISTANCE WHEN DESIGNING POST QUANTUM CRYPTOGRAPHIC SYSTEMS?
It is crucial to consider side-channel attack resistance when designing Post Quantum Cryptographic systems. As Post Quantum algorithms are typically more complex than their classical counterparts, they may be more vulnerable to side-channel attacks. Therefore, it is important to implement countermeasures to protect against these types of attacks in order to ensure the security of the cryptographic system.
ARE THERE ANY SPECIFIC POST QUANTUM ALGORITHMS THAT ARE MORE VULNERABLE TO SIDE-CHANNEL ATTACKS THAN OTHERS?
In general, Post Quantum algorithms that are more complex, such as lattice-based or code-based algorithms, may be more vulnerable to side-channel attacks than simpler algorithms, such as hash-based algorithms. However, it is important to note that all cryptographic algorithms can be vulnerable to side-channel attacks if not implemented and protected properly.
HOW DO YOU SEE THE FIELD OF SIDE-CHANNEL ATTACK RESEARCH EVOLVING IN RELATION TO POST QUANTUM CRYPTOGRAPHY?
As Post Quantum cryptography continues to gain traction, I anticipate that side-channel attack research will also increase in importance. As Post Quantum algorithms become more widely adopted, attackers will likely focus more on finding new and innovative ways to exploit physical characteristics of devices to extract sensitive information. As a result, the field of side-channel attack research will continue to evolve and adapt to new post-quantum algorithms and technologies.
THE FIELD OF SIDE-CHANNEL ATTACK RESEARCH WILL CONTINUE TO EVOLVE AND ADAPT TO NEW POST QUANTUM ALGORITHMS AND TECHNOLOGIES.
WHAT ARE SECURE-IC DOING WHEN IT COMES TO POST QUANTUM CRYPTOGRAPHY AND SIDE-CHANNEL ATTACKS?
First, we are heavily investing in research and development to improve the side-channel resistance of Post Quantum Cryptographic algorithms and systems. This includes developing new countermeasures, but also improving existing ones.
In addition, we are implementing countermeasures such as masking or blinding, to protect their Post Quantum Cryptographic systems against side-channel attacks.
OUR INTEGRATED SECURE ELEMENT (iSE) IS ALREADY PQC ENABLED.
Furthermore, our integrated Secure Element is PQC enabled, in that it already implements secure-boot with XMSS and crypto service with Lattice based algos (namely CRYSTALS Kyber & Dilithium), plus custom code-base crypto for sovereign use. These services are of course backed by hardware-based solutions, such as physically unclonable functions (PUFs) or physically random functions, to improve the side-channel resistance of post-quantum cryptographic systems. Additionally, we have a flexible implementation, whereby the HW provides "constant-time" acceleration and FW provides control over the algos parameters, PPA constraints, and security (including side-channel attack protection). This qualifies our iSE-PQC as a certification-ready silicon-proven technology, and that implements two protection levels: against "differential attacks" and against "single trace attacks".
Another thing that might not be so known is that we are on top of the previous mentioned we are oering services to help companies implement Post Quantum Cryptography and protect against side-channel attacks.
We are excited about the future of Post-Quantum Cryptography and the opportunities it presents. With the advancements in quantum computing, it is crucial that we stay ahead of the curve in developing secure and robust cryptographic solutions. All of us at Secure-IC are dedicated to research and to implement the latest PQC algorithms and countermeasures to protect against potential quantum attacks.
We are confident that our cutting-edge solutions will continue to provide the highest level of security for our customers in the years to come. We look forward to the continued evolution of PQC and the role we will play in shaping its future.
THANK YOU SO MUCH KHALED. ANYTHING YOU’D LIKE TO ADD TO CONCLUDE?
The possibility of SCAs has often been overlooked. Today, with both edge devices and complex ASIC/FPGA systems on a steep rise, it is essential that people are aware of the risks and take the necessary precautions. In addition SCA is an important matter to connected devices across all industries, and not to forget, it plays a key role to security certication processes.
At Secure-IC, we try to be ahead of the curve, and we are ready to answer any questions or requests that our customers may have.
DID YOU KNOW?
 During the Cold War days of the 1980s, Soviet eavesdroppers were suspected of having planted miniature microphones inside the IBM Selectric typewriters commonly used by Western organizations. By monitoring the electrical noise generated as the type ball rotated and pitched to strike the paper, the characteristics of those signals could determine which key was pressed.
During the Cold War days of the 1980s, Soviet eavesdroppers were suspected of having planted miniature microphones inside the IBM Selectric typewriters commonly used by Western organizations. By monitoring the electrical noise generated as the type ball rotated and pitched to strike the paper, the characteristics of those signals could determine which key was pressed.
About Secure-IC
With presence and customers across 5 continents, Secure-IC is the rising leader and the only global provider of end-to-end cybersecurity solutions for embedded systems and connected objects.
Driven by a unique approach called PESC (Protect, Evaluate, Service & Certify), Secure-IC positions itself as a partner to support its clients throughout and beyond the IC design process. Relying on innovation and research activities, Secure-IC provides Silicon-proven and cutting-edge protection technologies, integrated Secure Elements and security evaluation platforms to reach compliance with the highest level of certification for different markets (such as automotive, AIoT, defense, payments & transactions, memory & storage, server & cloud).
Related Semiconductor IP
- Multi-channel Ultra Ethernet TSS Transform Engine
- Configurable CPU tailored precisely to your needs
- Ultra high-performance low-power ADC
- HiFi iQ DSP
- CXL 4 Verification IP
Related Blogs
- Side-Channel Attacks On Post-Quantum Cryptography
- Integrating Post-Quantum Cryptography (PQC) on Arty-Z7
- Protecting electronic systems from side-channel attacks
- An introduction to side-channel attacks
Latest Blogs
- AI is stress-testing processor architectures and RISC-V fits the moment
- Rambus Announces Industry-Leading Ultra Ethernet Security IP Solutions for AI and HPC
- The Memory Imperative for Next-Generation AI Accelerator SoCs
- Leadership in CAN XL strengthens Bosch’s position in vehicle communication
- Validating UPLI Protocol Across Topologies with Cadence UALink VIP
