AndeSentry – Andes’ Security Platform
Security has become a critical requirement across a wide range of applications, including mobile devices, automotive infotainment systems, and embedded platforms such as robotics. These systems must deliver robust security functionality with minimal performance overhead, which in turn requires tight and seamless integration between hardware and software to achieve optimal efficiency.
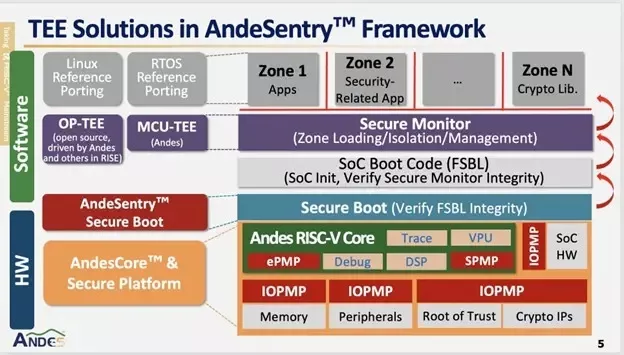
AndeSentry is Andes’ comprehensive security platform, consisting of both hardware and software components. On the hardware side, SPMP, ePMP and IOPMP provide strong isolation at the CPU core and SoC levels, respectively. On the software side, the OP-TEE stack delivers a Trusted Execution Environment (TEE) that enables hardware-enforced isolation of sensitive code and data. OP-TEE provides a secure operating system and application framework for executing security-critical functions independently of the main operating system. For deeply embedded use cases, Andes also offers an MCU-TEE Secure Monitor, designed for single-core 32-bit embedded processors that can be integrated with Bare Metal, FreeRTOS, and Zephyr environments.
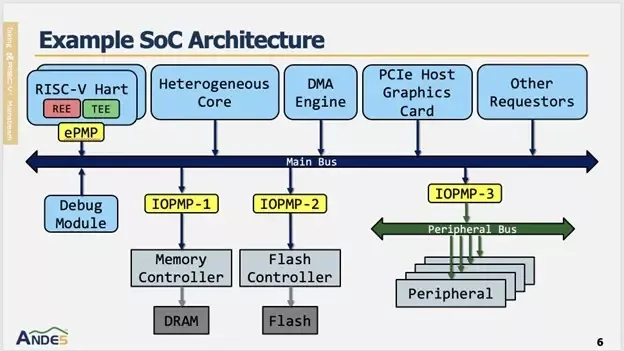
A typical SoC architecture includes multiple bus initiators, such as RISC-V harts and DMA engines. These initiators generate bus transactions targeting system resources, including memory and peripherals. Each RISC-V hart supports two types of execution environments: a Trusted Execution Environment (TEE) which provides a secure, isolated area in a processor to run sensitive code and data , ensuring confidentiality and integrity even if the main OS is compromised and a Rich Execution Environment (REE) which refers to the primary, standard operating system and application environment on a computing device (like Linux). Every bus initiator or hart is allocated a defined set of system resources, such as specific memory regions and peripherals.
To enforce isolation between execution environments on a hart, enhanced Physical Memory Protection (ePMP) is used to restrict the physical address ranges that a hart is permitted to access for each execution environment; any unauthorized memory access is blocked by ePMP. For non-CPU bus initiators, such as DMA engines, IOPMP performs address validation to ensure that transactions comply with the access permissions configured by software, and any invalid transaction is similarly blocked by the IOPMP.
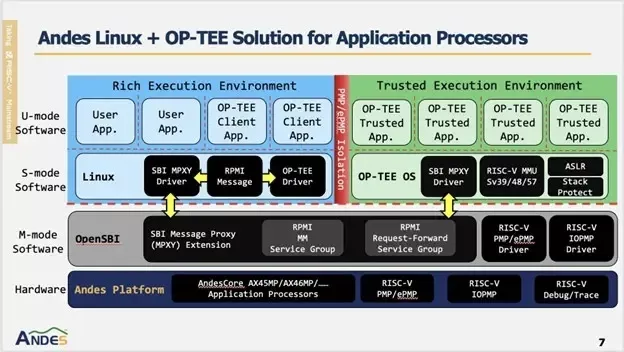
An OP-TEE based system supports two software execution environments: the Rich Execution Environment (REE) and the Trusted Execution Environment (TEE). Typically, the REE runs a general-purpose operating system, while the TEE runs a secure operating system. In the Andes solution, Linux is integrated as the general-purpose OS in the REE, and OP-TEE is deployed as the secure OS in the TEE. Most applications execute in Linux, whereas trusted applications run within OP-TEE. When protection of sensitive assets is required, developers can implement security-critical operations as OP-TEE trusted applications, ensuring that sensitive data is not exposed to the REE.
OP-TEE supports RISC-V MMU page-based virtual memory systems, including Sv39, Sv48, and Sv57. It maintains standalone page tables that are inaccessible to Linux, and the pages associated with trusted applications are isolated by the MMU, strengthening memory isolation between applications. In addition, the OP-TEE kernel virtual address space can optionally be protected using Address Space Layout Randomization (ASLR).
The Andes solution leverages the RISC-V standard SBI MPXY (message proxy) extension and the RISC-V Platform Management Interface (RPMI) specification as the messaging protocol between the REE and TEE. A Linux application can send messages to OP-TEE trusted applications to request secure services. A secure monitor is a critical component in this architecture; it runs at the highest privilege level and manages RISC-V PMP entries to enforce memory isolation. In the Andes OP-TEE implementation, OpenSBI serves as the secure monitor. During context switches between the two execution environments, the secure monitor dynamically reconfigures PMP entries so that only the memory regions permitted for the active execution environment are accessible.
To prevent the secure monitor from inadvertently accessing or executing memory belonging to less-privileged execution environments, RISC-V ePMP can be enabled to provide Supervisor Memory Access Prevention (SMAP) and Supervisor Memory Execution Prevention (SMEP) protections.
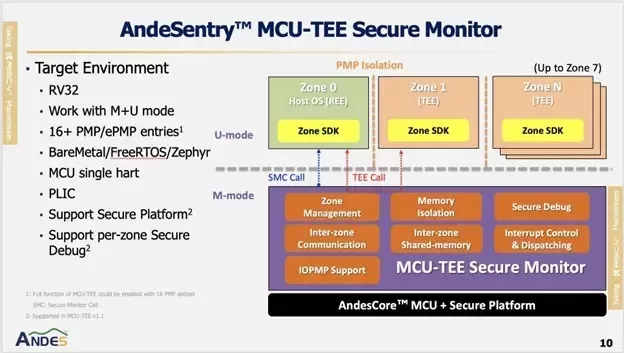
Andes’ MCU-TEE Secure Monitor is designed for single-hart, 32-bit MCU-class systems. The RISC-V hart operates using only M-mode and U-mode and provides 16 or more PMP/ePMP entries for memory protection. This solution targets embedded operating environments such as Bare Metal, FreeRTOS, and Zephyr. A key feature of the MCU-TEE Secure Monitor is support for per-zone Secure Debug, which enhances security when debug capabilities are enabled.

Security is a complex challenge that cannot be addressed by Andes alone. Andes welcomes collaboration with security partners to jointly develop and deliver comprehensive security solutions. If you are interested in becoming an Andes security partner, please contact the Andes Technical Marketing team. We look forward to working with you.
Related Semiconductor IP
- HBM4 PHY IP
- Ultra-Low-Power LPDDR3/LPDDR2/DDR3L Combo Subsystem
- MIPI D-PHY and FPD-Link (LVDS) Combinational Transmitter for TSMC 22nm ULP
- VIP for Compute Express Link (CXL)
- HBM4 Controller IP
Related Blogs
- Post-quantum security in platform management: PQShield is ready for SPDM 1.4
- Best-in-class Security Testing Platform for Side-channel Analysis by Rambus and Riscure
- Accelerating Development Cycles and Scalable, High-Performance On-Device AI with New Arm Lumex CSS Platform
- Ultra Ethernet Security: Protecting AI/HPC at Scale
