Attack on a PUF-based Secure Binary Neural Network
By Bijeet Basak, Nupur Patil, Kurian Polachan, Srinivas Vivek
International Institute of Information Technology, Bangalore, India
Abstract
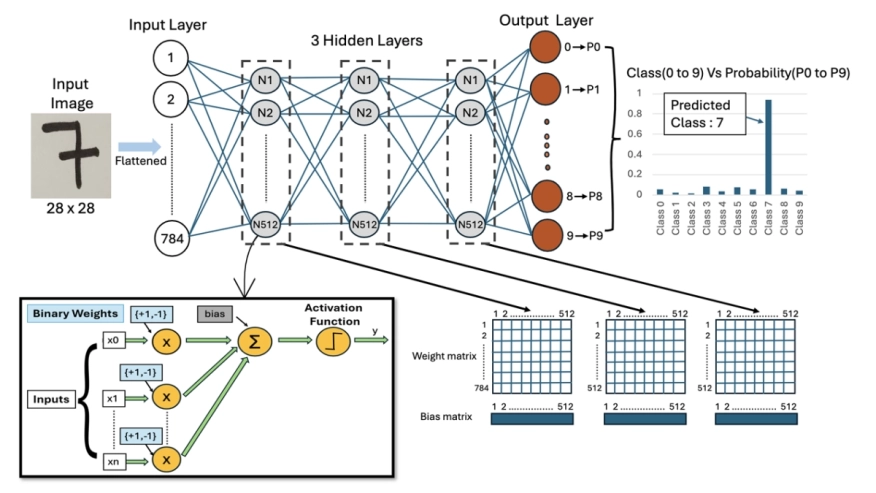
 Binarized Neural Networks (BNNs) deployed on memristive crossbar arrays provide energy-efficient solutions for edge computing but are susceptible to physical attacks due to memristor nonvolatility. Recently, Rajendran et al. (IEEE Embedded Systems Letter 2025) proposed a Physical Unclonable Function (PUF)-based scheme to secure BNNs against theft attacks. Specifically, the weight and bias matrices of the BNN layers were secured by swapping columns based on device's PUF key bits.
Binarized Neural Networks (BNNs) deployed on memristive crossbar arrays provide energy-efficient solutions for edge computing but are susceptible to physical attacks due to memristor nonvolatility. Recently, Rajendran et al. (IEEE Embedded Systems Letter 2025) proposed a Physical Unclonable Function (PUF)-based scheme to secure BNNs against theft attacks. Specifically, the weight and bias matrices of the BNN layers were secured by swapping columns based on device's PUF key bits.
In this paper, we demonstrate that this scheme to secure BNNs is vulnerable to PUF-key recovery attack. As a consequence of our attack, we recover the secret weight and bias matrices of the BNN. Our approach is motivated by differential cryptanalysis and reconstructs the PUF key bit-by-bit by observing the change in model accuracy, and eventually recovering the BNN model parameters. Evaluated on a BNN trained on the MNIST dataset, our attack could recover 85% of the PUF key, and recover the BNN model up to 93% classification accuracy compared to the original model's 96% accuracy. Our attack is very efficient and it takes a couple of minutes to recovery the PUF key and the model parameters.
To read the full article, click here
Related Semiconductor IP
- Digital PUF IP
- PUF IP
- PUF FPGA-Xilinx Premium with key wrap
- PUF FPGA-Xilinx Base
- ASIL-B Ready PUF Hardware Premium with key wrap and certification support
Related Articles
- Input-Triggered Hardware Trojan Attack on Spiking Neural Networks
- MultiVic: A Time-Predictable RISC-V Multi-Core Processor Optimized for Neural Network Inference
- FPGA-Accelerated RISC-V ISA Extensions for Efficient Neural Network Inference on Edge Devices
- Neural Networks Can Help Keep Connected Vehicles Secure
Latest Articles
- GenAI for Systems: Recurring Challenges and Design Principles from Software to Silicon
- Creating a Frequency Plan for a System using a PLL
- RISCover: Automatic Discovery of User-exploitable Architectural Security Vulnerabilities in Closed-Source RISC-V CPUs
- MING: An Automated CNN-to-Edge MLIR HLS framework
- Fault Tolerant Design of IGZO-based Binary Search ADCs