An AUTOSAR-Aligned Architectural Study of Vulnerabilities in Automotive SoC Software
By Srijita Basu 1, Haraldsson Bengt 2, Miroslaw Staron 1, Christian Berger 1, Jennifer Horkoff 1, Magnus Almgren 1
1 Chalmers University of Technology and University of Gothenburg, Sweden
2 Scania CV AB, Sweden
Abstract
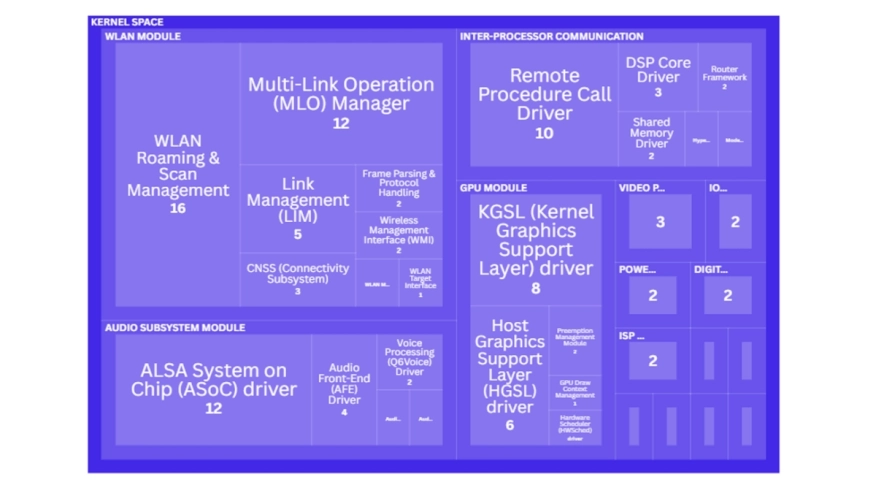
 Cooperative, Connected and Automated Mobility (CCAM) are complex cyber-physical systems (CPS) that integrate computation, communication, and control in safety-critical environments. At their core, System-on-Chip (SoC) platforms consolidate processing units, communication interfaces, AI accelerators, and security modules into a single chip. AUTOSAR (AUTomotive Open System ARchitecture) standard was developed in the automotive domain to better manage this complexity, defining layered software structures and interfaces to facilitate reuse of HW/SW components. However, in practice, this integrated SoC software architecture still poses security challenges, particularly in real-time, safety-critical environments. Recent reports highlight a surge in SoC-related vulnerabilities, yet systematic analysis of their root causes and impact within AUTOSAR-aligned architectures is lacking. This study fills that gap by analyzing 180 publicly reported automotive SoC vulnerabilities, mapped to a representative SoC software architecture model that is aligned with AUTOSAR principles for layered abstraction and service orientation. We identify 16 root causes and 56 affected software modules, and examine mitigation delays across Common Weakness Enumeration (CWE) categories and architectural layers. We uncover dominant vulnerability patterns and critical modules with prolonged patch delays, and provide actionable insights for securing automotive CPS platforms, including guides for improved detection, prioritization, and localization strategies for SoC software architectures in SoC-based vehicle platforms.
Cooperative, Connected and Automated Mobility (CCAM) are complex cyber-physical systems (CPS) that integrate computation, communication, and control in safety-critical environments. At their core, System-on-Chip (SoC) platforms consolidate processing units, communication interfaces, AI accelerators, and security modules into a single chip. AUTOSAR (AUTomotive Open System ARchitecture) standard was developed in the automotive domain to better manage this complexity, defining layered software structures and interfaces to facilitate reuse of HW/SW components. However, in practice, this integrated SoC software architecture still poses security challenges, particularly in real-time, safety-critical environments. Recent reports highlight a surge in SoC-related vulnerabilities, yet systematic analysis of their root causes and impact within AUTOSAR-aligned architectures is lacking. This study fills that gap by analyzing 180 publicly reported automotive SoC vulnerabilities, mapped to a representative SoC software architecture model that is aligned with AUTOSAR principles for layered abstraction and service orientation. We identify 16 root causes and 56 affected software modules, and examine mitigation delays across Common Weakness Enumeration (CWE) categories and architectural layers. We uncover dominant vulnerability patterns and critical modules with prolonged patch delays, and provide actionable insights for securing automotive CPS platforms, including guides for improved detection, prioritization, and localization strategies for SoC software architectures in SoC-based vehicle platforms.
Keywords: Architecture · Automotive · SoC · Vulnerability
To read the full article, click here
Related Semiconductor IP
- Multi-channel Ultra Ethernet TSS Transform Engine
- Configurable CPU tailored precisely to your needs
- Ultra high-performance low-power ADC
- HiFi iQ DSP
- CXL 4 Verification IP
Related Articles
- RISCover: Automatic Discovery of User-exploitable Architectural Security Vulnerabilities in Closed-Source RISC-V CPUs
- Software Infrastructure of an embedded Video Processor Core for Multimedia Solutions
- How to manage changing IP in an evolving SoC design
- The Growing Imperative Of Hardware Security Assurance In IP And SoC Design
Latest Articles
- GenAI for Systems: Recurring Challenges and Design Principles from Software to Silicon
- Creating a Frequency Plan for a System using a PLL
- RISCover: Automatic Discovery of User-exploitable Architectural Security Vulnerabilities in Closed-Source RISC-V CPUs
- MING: An Automated CNN-to-Edge MLIR HLS framework
- Fault Tolerant Design of IGZO-based Binary Search ADCs