security engine IP
Filter
Compare
249
IP
from
42
vendors
(1
-
10)
-
Low Power Security Engine
- Protocol Supported : ECDHE, ECDSA
- Acceleration units : ECC, SHA256, AES128
- TRNG
- AMBA standard interface
-
Security Hash, SM3 Hash and HMAC Engine
- The hash processor is a fully compliant implementation of the secure hash algorithm (SHA-1, SHA-224, SHA-256, SHA-384, SHA-512), the MD5 (message-digest algorithm 5) and SM3 hash algorithm and the HMAC (keyed-hash message authentication code) algorithm suitable for a variety of applications. HMAC is suitable for applications requiring message authentication.
-
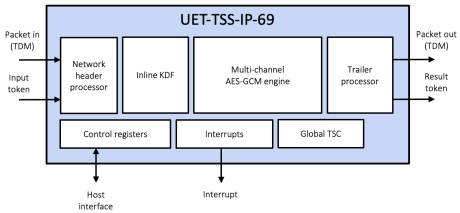
Multi-channel Ultra Ethernet TSS Transform Engine
- The UET-TSS-IP-69 (EIP-69) is a high-performance, multi-channel transform engine that provides the complete TSS packet transformation (including KDF and IP/UDP updates), bypass/drop and basic crypto processing at rates up to 1.6Tbps.
- The engine is designed for integration into the systems that require TSS processing for one or more ports. The engine is provided as separate ingress and egress data paths.
-
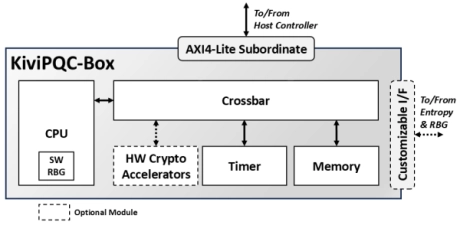
ML-KEM Key Encapsulation & ML-DSA Digital Signature Engine
- The KiviPQC™-Box is a hardware accelerator for post-quantum cryptographic operations.
- It implements both the Module Lattice-based Key Encapsulation Mechanism (ML-KEM) and the Module Lattice-based Digital Signature Algorithm (ML-DSA), standardized by NIST in FIPS 203 and FIPS 204, respectively.
-
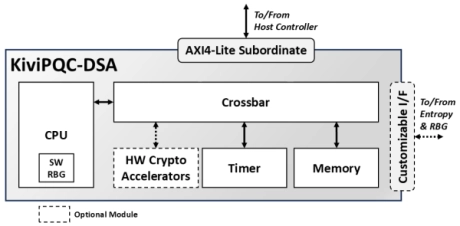
ML-DSA Digital Signature Engine
- The KiviPQC™-DSA is a hardware accelerator for post-quantum cryptographic operations.
- It implements the Module Lattice-based Digital Signature Algorithm (ML-DSA), standardized by NIST in FIPS 204.
- This mechanism realizes the appropriate procedures for securely generating a private/public key pair, digitally signing a message or a data block, and performing digital signature verification.
-
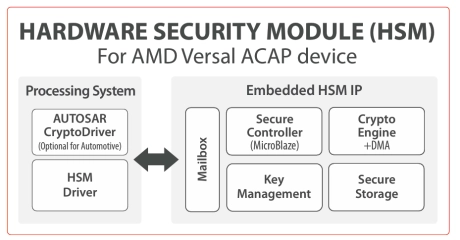
Hardware Security Module (HSM) for AMD Xilinx Versal ACAP device
- The HSM IP module is a Hardware Security Module for a wide range of applications.
- It is developed according to the guidelines set out by the EVITA project and is meant to be implemented on a AMD Xilinx Versal ACAP device.
- It supports TrustZone.
-
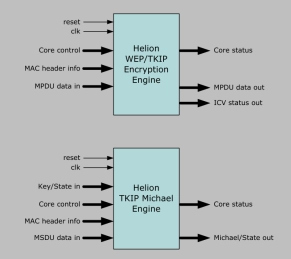
802.11i Wireless Security Cores
- These high performance cores have been designed to provide hardware acceleration of the underlying 802.11 WPA security algorithms, which in combination with the Helion AES-CCM core family, may be used to implement a full 802.11i WPA24 security solution very efficiently in Xilinx FPGA.
- The security processing is split into two parts, since they are likely to be required at different points within the MAC subsystem.
-
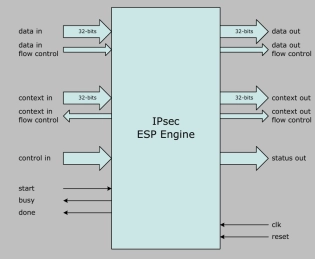
IPsec ESP IP core for FPGA
- Built on the success of Helion's industry proven cryptographic IP cores, the Helion ESP Engine provides hardware acceleration of the key cryptographic algorithms and packet processing required by the IPsec Encapsulating Security Payload (ESP) protocol.
- Its modular architecture provides the flexibility to support only those cryptographic algorithms required for a particular application to provide the optimum logic area and performance trade-off.
-
Data Movement Engine - Turnkey network compute subsystem for data movement applications.
- Industrial Networking: Rapid packet processing of data through multiple, switched ethernet ports with support for factory automation protocols
- 5G/6G Communications: Scalable L2/L3 Ethernet switch with flexible port counts/speeds, including TSN and security
- Automotive Gateway: High-speed data packet networking with multiple communication interfaces and support for switching and bridging
- Datacenter Infrastructure: Standalone data processing units to handle highly multiplexed data streams corresponding to millions of network connections with high efficiency and low power
-
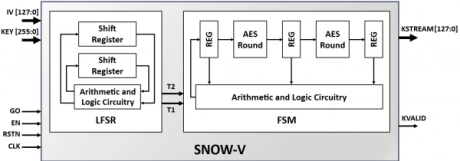
SNOW-V Stream Cipher Engine
- The SNOW-V IP core implements the SNOW-V stream cipher mechanism, aiming to meet the security demands of modern high-speed communication systems.
- It conforms to the official SNOW-V mechanism, published in 2019 by the IACR Transactions on Symmetric Cryptology, as an extensive revision of SNOW 3G stream cipher.