DRsam: Detection of Fault-Based Microarchitectural Side-Channel Attacks in RISC-V Using Statistical Preprocessing and Association Rule Mining
By Muhammad Hassan ∗, Maria Mushtaq †, Jaan Raik ∗, Tara Ghasempouri ∗
∗ Department of Computer Systems, Tallinn University of Technology, Tallinn, Estonia
† Télécom Paris, Institut Polytechnique de Paris, Palaiseau, France
Abstract
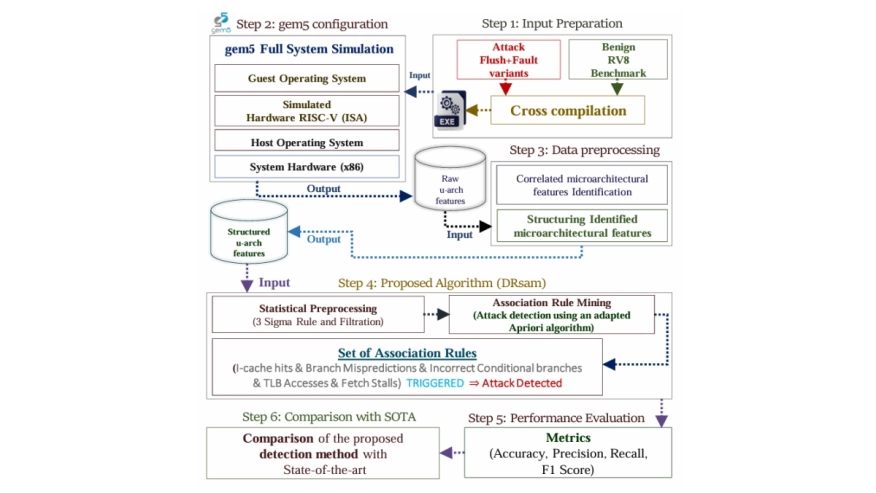
 RISC-V processors are becoming ubiquitous in critical applications, but their susceptibility to microarchitectural side-channel attacks is a serious concern. Detection of microarchitectural attacks in RISC-V is an emerging research topic that is relatively underexplored, compared to x86 and ARM. The first line of work to detect flush+fault-based microarchitectural attacks in RISC-V leverages Machine Learning (ML) models, yet it leaves several practical aspects that need further investigation. To address overlooked issues, we leveraged gem5 and propose a new detection method combining statistical preprocessing and association rule mining having reconfiguration capabilities to generalize the detection method for any microarchitectural attack. The performance comparison with state-of-the-art reveals that the proposed detection method achieves up to 5.15% increase in accuracy, 7% rise in precision, and 3.91% improvement in recall under the cryptographic, computational, and memory-intensive workloads alongside its flexibility to detect new variant of flush+fault attack. Moreover, as the attack detection relies on association rules, their human-interpretable nature provides deep insight to understand microarchitectural behavior during the execution of attack and benign applications.
RISC-V processors are becoming ubiquitous in critical applications, but their susceptibility to microarchitectural side-channel attacks is a serious concern. Detection of microarchitectural attacks in RISC-V is an emerging research topic that is relatively underexplored, compared to x86 and ARM. The first line of work to detect flush+fault-based microarchitectural attacks in RISC-V leverages Machine Learning (ML) models, yet it leaves several practical aspects that need further investigation. To address overlooked issues, we leveraged gem5 and propose a new detection method combining statistical preprocessing and association rule mining having reconfiguration capabilities to generalize the detection method for any microarchitectural attack. The performance comparison with state-of-the-art reveals that the proposed detection method achieves up to 5.15% increase in accuracy, 7% rise in precision, and 3.91% improvement in recall under the cryptographic, computational, and memory-intensive workloads alongside its flexibility to detect new variant of flush+fault attack. Moreover, as the attack detection relies on association rules, their human-interpretable nature provides deep insight to understand microarchitectural behavior during the execution of attack and benign applications.
To read the full article, click here
Related Semiconductor IP
- Multi-channel Ultra Ethernet TSS Transform Engine
- Configurable CPU tailored precisely to your needs
- Ultra high-performance low-power ADC
- HiFi iQ DSP
- CXL 4 Verification IP
Related Articles
- ShuffleV: A Microarchitectural Defense Strategy against Electromagnetic Side-Channel Attacks in Microprocessors
- COVERT: Trojan Detection in COTS Hardware via Statistical Activation of Microarchitectural Events
- Real-Time ESD Monitoring and Control in Semiconductor Manufacturing Environments With Silicon Chip of ESD Event Detection
- Hardware vs. Software Implementation of Warp-Level Features in Vortex RISC-V GPU
Latest Articles
- GenAI for Systems: Recurring Challenges and Design Principles from Software to Silicon
- Creating a Frequency Plan for a System using a PLL
- RISCover: Automatic Discovery of User-exploitable Architectural Security Vulnerabilities in Closed-Source RISC-V CPUs
- MING: An Automated CNN-to-Edge MLIR HLS framework
- Fault Tolerant Design of IGZO-based Binary Search ADCs