SRAM PUF: A Closer Look at the Most Reliable and Most Secure PUF
By Geert-Jan Schrijen (Intrinsic ID)
A recent article on the reliability of SRAM PUFs as a security mechanism for connected devices raised points worthy of discussion. Certainly, in today’s ever-more-connected world of the internet of things (IoT) and proliferating 5G networks, hardware-based security is more important than ever. So, if you’re looking for a way to secure a connected device, how do you evaluate the security and reliability of the various options available?
What is an SRAM PUF?
First, what is a PUF, and how does it provide security? A PUF is a Physical Unclonable Function – a physical structure placed within a physical entity to create a unique identity. This unique identity is used as the foundation, or “root of trust,” for security.
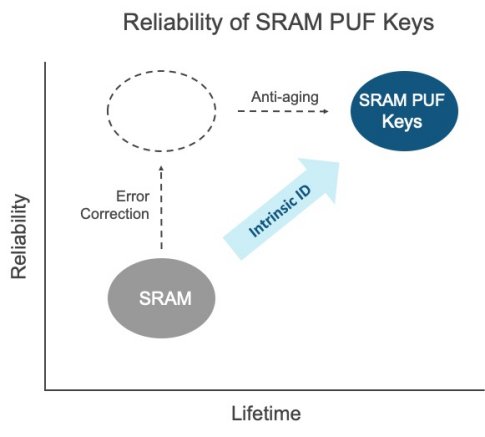
Multiple approaches to using a PUF to secure a device exist. One such approach is SRAM PUF, which uses the random differences in the SRAM’s threshold voltages to create a digital fingerprint unique to that device. This digital fingerprint is then used to create a secret key that forms the basis of the security subsystem for that device. Critically, this secret key is not stored but is dynamically regenerated from the SRAM PUF inside a secure perimeter. This means that even if the memory is breached, no key is stored there, so it can’t be stolen or compromised.
Intrinsic ID SRAM PUFs have been used in production for more than a decade, and so the technology has been honed and has matured over time. These SRAM PUFs are deployed in hundreds of millions of devices from leading-edge suppliers, including four of the five leading microprocessor suppliers. One of the reasons SRAM PUFs are so reliable and secure is that they have had the benefit of extended field use to influence their development.
Evaluating SRAM PUF Reliability
Let’s dig deeper into questions that might arise as you evaluate the reliability of the SRAM PUF. You may wonder if the random differences in the threshold voltages used to create the SRAM PUF are smaller with advanced process nodes, causing more start-up SRAM cell values to flip at repetitive readout. While it is true that the absolute differences in threshold voltages become smaller, it is also known that the impact of process variation becomes bigger with smaller technology nodes (Pelgrom’s law 1). In deployment, we have seen that smaller nodes – down to 7nm so far – often show fewer bit flips (less noise) in the SRAM PUF values. Intel has published their experience with SRAM PUFs at 14nm. 2
Some might question if variations such as temperature and voltage variations, as well as time, cause more noise in the random values extracted from the SRAM. Ambient conditions have an impact on all electronic devices, and devices do simply age. SRAM PUFs are mainly impacted by negative bias temperature instability (NBTI); it has been observed that the impact of aging depends strongly on the data stored in the SRAM. Based on this knowledge, anti-aging measures can be applied that cause the SRAM PUF to grow more reliable over time, and can actually extend the life of the SRAM!
Finally, you may have heard that SRAM PUFs use error-correction
codes to account for variations in start-up values, and so might
worry that this process is time-consuming or cumbersome. To the
contrary it has been well established that helper
data algorithms 3 4 or Fuzzy
Extractors 5 are used to
ensure that exactly the same key can be reconstructed under all
circumstances, from winter in Alaska to summertime in Death
Valley. Any PUF without some kind of correction system would be
vulnerable to ambient effects and aging. However, if designed and
deployed correctly, helper data ensures the reliability of a PUF
system. In fact, even if the PUF system had to correct an error
rate of up to 25 percent, SRAM PUFs would still function within
specification. In field deployment, the noise level encountered by
SRAM PUF systems is typically smaller than 10 percent, well within specification boundaries 6. In fact, SRAM PUFs
are so robust that they have been chosen for use in devices
intended to be deployed in outer space.
In God We Trust. All Others Bring Data.
Claims about the Hamming weight and distance for any particular solution are easy to publish. But if you’re evaluating IoT device security options and hear conflicting claims, ask to see the data behind the claims – not just a summary chart, but real, operational data. If you’d like to learn more about the reliability of Intrinsic ID SRAM PUFs 6, this whitepaper provides a detailed overview. You might also want to review this peer-reviewed paper, presented at CHES 2013 and published by Springer.7
Some Final Questions to Ask
Ask to see a list of customers, application types, and supported process platforms. We believe that when you see the data, hear the stories of actual customers and their applications, you’ll come to the same conclusion as the leaders in IoT devices: SRAM PUFs are the most reliable, secure solution available today.
Finally, ask if the security option you’re considering stores a key. Not only are they reliable enough to be used in space, but SRAM PUFs do not store a key. What isn’t stored can’t be stolen or compromised. Any solution that stores a key is vulnerable to attackers.
1 M. J. M. Pelgrom, C. J. Duinmaijer, and A. P. G. Welbers, “Matching properties of MOS transistors,” IEEE J. Solid-State Cir- cuits, vol. 24, no. 5, pp. 1433–1440, Oct. 1989.
2 Ting Lu, Ryan Kenny, Sean Atsatt, “Secure Device Manager for Intel® Stratix® 10 Devices Provides FPGA and SoC Security”, Intel White Paper,
3 Linnartz JP., Tuyls P. (2003) New Shielding Functions to Enhance Privacy and Prevent Misuse of Biometric Templates. In: Kittler J., Nixon M.S. (eds) Audio- and Video-Based Biometric Person Authentication. AVBPA 2003. Lecture Notes in Computer Science, vol 2688. Springer, Berlin, Heidelberg
4 Guajardo J., Kumar S.S., Schrijen GJ., Tuyls P. (2007) FPGA Intrinsic PUFs and Their Use for IP Protection. In: Paillier P., Verbauwhede I. (eds) Cryptographic Hardware and Embedded Systems - CHES 2007. CHES 2007. Lecture Notes in Computer Science, vol 4727. Springer, Berlin, Heidelberg
5 Dodis, Y., Reyzin, L., Smith, A.: Fuzzy extractors: How to generate string keys from biometrics and other noisy data. In: Cachin, C., Camenisch, J.L. (eds.) EUROCRYPT 2004. LNCS, vol. 3027, pp. 523–540. Springer, Heidelberg (2004)
6 “The Reliability of SRAM PUF”, Intrinsic ID White Paper: https://www.intrinsic-id.com/landing-page-white-paper-reliability-sram-puf
7 Maes R. (2013) An Accurate Probabilistic Reliability Model for Silicon PUFs. In: Bertoni G., Coron JS. (eds) Cryptographic Hardware and Embedded Systems - CHES 2013. CHES 2013. Lecture Notes in Computer Science, vol 8086. Springer, Berlin, Heidelberg
Related Semiconductor IP
- AI processing engine - Voice control, Context detection and Speaker ID
- Super low-power and high accuracy AI processing engine for Wake Word, Voice Commands, Acoustic Event Detection, Speaker ID and Sensors
- ARC HS47Dx4 quad-core version of dual-issue HS47D ARCv2DSP ISA, with 100+ DSP instructions and I&D cache
- ARC HS47Dx2 dual-core version of dual-issue HS47D ARCv2DSP ISA, with 100+ DSP instructions and I&D cache
- ARC HS47D 32-bit, dual-issue processor core, ARCv2DSP ISA, with 100+ DSP instructions and I&D cache
Related White Papers
- NeoPUF, A Reliable and Non-traceable Quantum Tunneling PUF
- Why a True Hardware PUF is more Reliable as RoT
- PUF is a Hardware Solution for the Sunburst Hack
- Basics of SRAM PUF and how to deploy it for IoT security
Latest White Papers
- Ramping Up Open-Source RISC-V Cores: Assessing the Energy Efficiency of Superscalar, Out-of-Order Execution
- Transition Fixes in 3nm Multi-Voltage SoC Design
- CXL Topology-Aware and Expander-Driven Prefetching: Unlocking SSD Performance
- Breaking the Memory Bandwidth Boundary. GDDR7 IP Design Challenges & Solutions
- Automating NoC Design to Tackle Rising SoC Complexity