Bluetooth Mesh - the Next Wave of IoT Technology
1- Introduction:
The market for Bluetooth low energy devices is expected to reach 1.4 Billion, growing at a CAGR of 34% between 2015 to 2021, as per ABI Research. While investments in Internet-of-Things (IoT) technology are ever increasing, there are many wireless technologies such as Zigbee, Wi-Fi, Bluetooth and Z-wave competing for adoption. The choice of wireless technology depends on the use case and key requirements such as power, latency, reliability, scalability, interoperability, range, cost and bandwidth.
The adoption of the Bluetooth low energy (Bluetooth LE) specifications v4.0/v4.2 standards is being driven by adoption in several markets such as the Health and Fitness devices, Beacons, Asset tracking, Home automation, PC Peripherals etc. Bluetooth low energy 5, together with the Bluetooth LE Mesh specifications are set to make Bluetooth the ‘Connectivity of Choice’ in IoT markets such as Connected Home, Commercial Lighting and Industrial Wireless Sensor Network markets.
The rest of this article focuses on introducing the Bluetooth Mesh technology.
2- Introducing Bluetooth Mesh
The Bluetooth SIG has recently adopted the specifications for adding Mesh networking capability to any Bluetooth LE enabled device. As we have come to expect from Bluetooth, Mesh too is fully backwards compatible, with any Bluetooth low energy device (Version 4.0 and above).
The Mesh v1.0 is a flooding based mesh technology which uses the advertisement packets to transmit messages. Use of the advertisement packets makes the Bluetooth Mesh a non-connectible mesh network – where each node of the mesh networks simply broadcast the message securely. There is no need for a “Connection” to be made between the various nodes of the Mesh Network.
A very simple implementation of the Mesh network may simply include nodes which will continuously scan for broadcast messages, and relay messages not intended for itself to be transmitted forward – extending the range of the network. One of the greatest advantage of flooding mesh is that it is more resilient to intermittent failures and offers redundancy – which is critical in the crowded ISM bands like 2.4 GHz
The Mesh specification provides 2-level security based on 128-bit AES encryption. The lower level of encryption as part of the network layer encrypts all the communication in the mesh network. The higher level of encryption (Application encryption) protects the data and allows message relay by intermediary nodes of the mesh network.
3- Life Cycle of a Mesh Node:
The Life cycle of a Mesh node starts with an un-provisioned device. This is a stage where the device will have an unassigned unique ID (Device UUID) and is ready to be provisioned.

Figure 1 – Life cycle of Mesh node
3.1- Provisioning
For any Bluetooth Device to be a part of the Mesh network it has to be provisioned. Provisioning is done with the help of a Provisioner device which is generally a Mobile Application.
The Device which supports the Bluetooth Mesh sends out a message (similar to Beacon) that is available for provisioning into a Mesh Network. This message includes the device’s unique ID (Device UUID). The Provisioner device invites a new device to the network, and the two devices agree on an authentication algorithm to be used, and share public keys. Once the node is provisioned as part of a Mesh network, it will undergo the process of configuration.
3.2- Configuration:
Mesh device configuration involves the addition of the Application keys which provide the 2nd level of security to the application data. Further the configuration will define the “Publish/Subscribe” model of the device. The devices can be configured to only Publish (send data addressing a particular node), only Subscribe (receive data with address corresponding to its unique ID) or support both Publish and Subscribe.
3.3- Reset and Key refresh
Once the node reset is done, all the addresses are cleared and it becomes an un-provisioned device and it will have an unassigned unique ID. For replacing a faulty node the Provisioner has to Black list the particular node. Once a node is black listed, the key refresh procedure will be initiated, then the Provisioner sends new keys to the other nodes in the network ensuring security of the Mesh Network.
4- Advanced Concepts Bluetooth Mesh:
The Bearer Layer of the Mesh stack (Figure 2) defines how the Mesh messages are transported between nodes. Currently, there are 2 Bearers defined by the specification- Advertising Bearer and GATT Bearer. The Advertising Bearer uses the GAP functionality to receive and retransmit messages to the other nodes and is the primary mode of Mesh Communication between devices. The GATT Bearer later is used to enable backward connectivity where any legacy Bluetooth LE device (not supporting Advertising Bearer) can still be a part of the Mesh Network
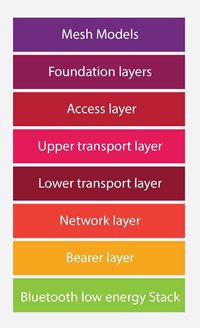
Figure 2 – The Mesh Stack
Leveraging the configuration option of Publish/Subscribe and that of the Advertising/GATT Bearer, the devices of the mesh network can be configured to Relay node, Proxy node, Low power node or a Friend node. Here we will introduce the node configurations and their functionality.
| Node Configuration | Functionality | Application |
| Relay Node Example Node 2 of Figure 3 | Configured to support both Publish/Subscribe, the relay nodes are capable of receiving and re-transmit the message over the Advertising bearer. In the below figure Node 1, Node 2 and Node 3 are relay nodes | The Relay Nodes are expected to be awake all the time, preferably not battery operated. The Relay Node positioning is critical to ensure Mesh Network coverage. |
| Proxy Node Example Node 1 of Figure 3 | This node can receive and re-transmit the message to other nodes with the help of GATT and Advertising Bearers In the below figure Node 1 is a proxy node | Proxy Nodes are important to allow backward compatibility since Advertisement Bearers are not supported by some devices such as smartphones. |
| Low Power Node Example Node 4 of Figure 3 | These nodes are not-awake all the time to save power, and need to be associated with a “Friend Node”. The Friend Node communicates with the Mesh Network on behalf of the Low-power node In the below figure Node 4 is a low power node | The Low Power Node is designed to wake at pre-determined intervals to receive/send messages from/to the Friend Node. |
| Friend Node Example Node 2 of Figure 3 | The Friend Node is a special case of Relay Node, with additional functionality of communicating on behalf of one or more Low Power Nodes In the below figure Node 3 is a friend nodes | The Friend Node is expected to store the messages intended for all Low-power nodes to which it is associated, until requested by Low-power nodes. |
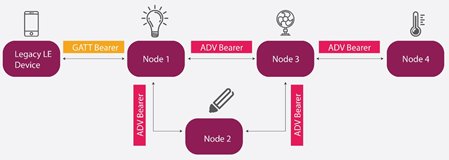
Figure 3 – Sample Mesh Network
Conclusion
The Bluetooth Mesh fills a key gap in Bluetooth technology, which hitherto restricted wide deployment in emerging IoT applications such as Lighting. The ecosystem for adoption of Bluetooth Mesh Network is expected to grow exponentially over the next few years. Most Bluetooth chipset suppliers, OEMs and System Integrators have begun investing in mesh capability support to their offerings and products are expected to be in Production over next few quarters.
References:
Bluetooth Mesh FAQs on the Bluetooth SIG website
Bluetooth Mesh and Mesh Models core specification
Bluetooth Mesh Networking – An introduction for Developers.
Related Semiconductor IP
- Bluetooth MESH v1.1 Software IP
- Android and iOS mobile commissioning and provisioning application for Bluetooth Mesh network
- a robust lighting control technology based on the globally interoperable Bluetooth mesh standard.
- Mindtree's Metal to Cloud Solution for Wireless lighting industry based on Bluetooth Mesh
Related White Papers
- Bluetooth settling into comfortable niche
- SoC Test and Verification -> Testing mixed-signal Bluetooth designs
- Wireless lan standard holds back Bluetooth
- Report sees strong prospects for Bluetooth
Latest White Papers
- Ramping Up Open-Source RISC-V Cores: Assessing the Energy Efficiency of Superscalar, Out-of-Order Execution
- Transition Fixes in 3nm Multi-Voltage SoC Design
- CXL Topology-Aware and Expander-Driven Prefetching: Unlocking SSD Performance
- Breaking the Memory Bandwidth Boundary. GDDR7 IP Design Challenges & Solutions
- Automating NoC Design to Tackle Rising SoC Complexity