Cryptography IP
Welcome to the ultimate Crypto Accelerator IP hub! Explore our vast directory of Crypto Accelerator IP
All offers in
Cryptography IP
Filter
Compare
337
Cryptography IP
from 62 vendors
(1
-
10)
-
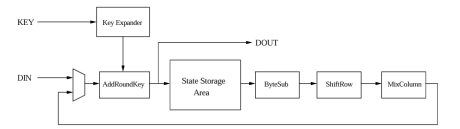
AES core
- Implemented according to the FIPS 197 documentation.
- Also available in CBC, CFB and OFB modes.
- Key size of 128, 192 and 256 bits.
- Both encryption and decryption supported.
-
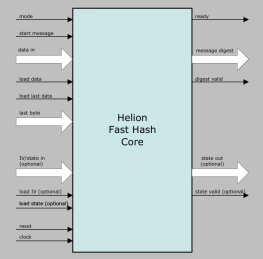
SHA-1 Processor
- Suitable for data authentication applications.
- Fully synchronous design.
- Available as fully functional and synthesizable VHDL or Verilog soft-core.
- Xilinx and Altera netlist available for various devices.
-
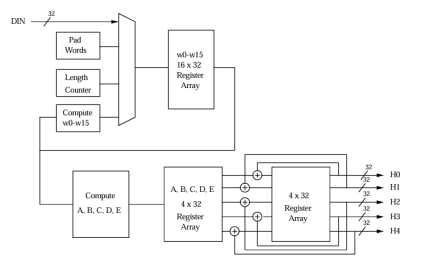
MD5 Processor
- RFC 1321 compliant.
- Suitable for data authentication applications.
- Fully synchronous design.
- Available as fully functional and synthesizable VHDL or Verilog soft-core.
-
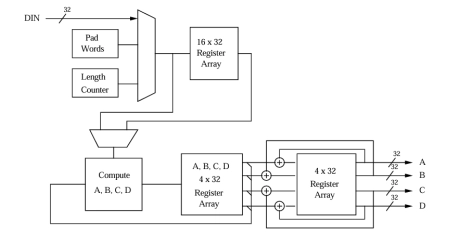
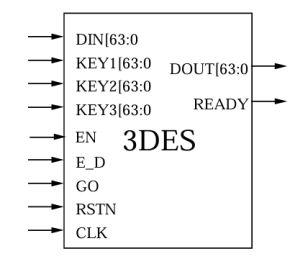
Triple DES core
- Implemented according to the X9.52 standard
- Implementation based on NIST certified DES core
- Also available in CBC, CFB and OFB modes.
- 112 or 168 bits keys supported.
-
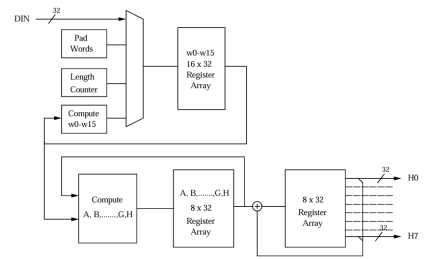
SHA-256 Processor
- This core is a fully compliant implementation of the Message Digest Algorithm SHA-256. It computes a 256-bit message digest for messages of up to (264 – 1) bits. Simple, fully synchronous design with low gate count.
- The OL_SHA256 core is a fully compliant hardware implementation of the SHA-256 algorithm, suitable for a variety of applications.
-
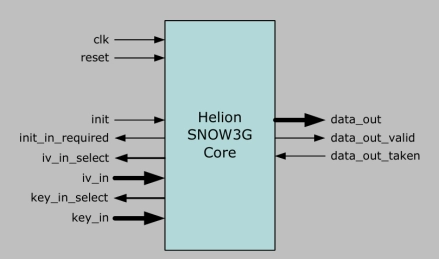
SNOW3G Stream Cipher Core
- The Helion SNOW3G core efficiently implements the stream cipher used as the basis for the UEA2 confidentiality algorithm and UIA2 integrity algorithm which provide data security within the 3GPP UMTS and LTE mobile communication standards.
- The core also fully supports the 128-EEA1 confidentiality and 128-EIA1 integrity algorithms which were introduced in 3GPP Specification Release 8, and which are identical to UEA2 and UIA2 respectively.
-
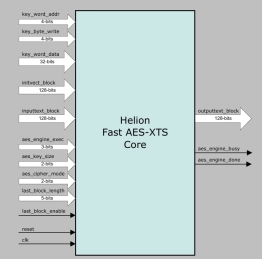
AES-XTS IP core
- The Helion Fast AES XTS core implements the AES “XEX-based Tweaked Codebook with Ciphertext Stealing” cipher mode (abbreviated to XTS) specified by NIST SP800-38E and in IEEE 1619 to provide Narrow-Block Encryption as part of its Standard for Cryptographic Protection of Data on Block-Oriented Storage Devices.
- XTS is also specified in IEEE 1619.1 for use in tape storage applications. In addition, some versions optionally implement the AES Cipher Block Chaining (AES-CBC) mode of operation which is sometimes used in legacy storage applications.
-
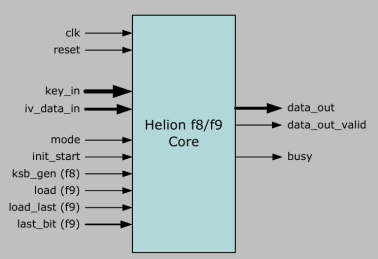
3GPP KASUMI f8 and f9 cores
- The Helion 3GPP KASUMI cores perform the f8 confidentiality and f9 integrity algorithms required to provide data security within the GSM/EDGE and UMTS mobile communication standards.
- Both algorithms are based on the KASUMI 64-bit block cipher which uses a 128-bit key. The KASUMI algorithm was designed by the Security Algorithms Group of Experts (SAGE) within ETSI, and is an optimised version of the MISTY1 block cipher originally developed by Mitsubushi Electric Corporation of Japan. Within ETSI, the f8 and f9 algorithms are now known as UEA1 and UIA1 respectively.
-
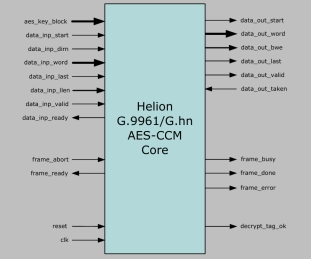
G.9961 AES-CCM Frame Encryption Core
- The Helion G.9961 AES-CCM (“AES-G.hn”) core is designed to sit near the top of the LLC sublayer and provide the security functionality described in Section 9.1 of ITU-T G.9961.
- The core integrates all of the underlying functions required to implement AES in CCM mode for G.9961 including nonce and header formation, round-key expansion, counter management, block chaining, final block masking, and tag appending and checking features.
- The only external logic required is to insert the CCMP header field for frames that are to be encrypted.
-