Secure Element IP
Filter
Compare
54
IP
from
9
vendors
(1
-
10)
-
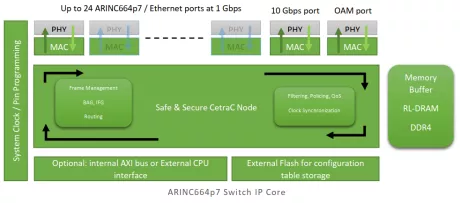
Multi Protocol Switch IP Core for Safe and Secure Ethernet Network
- "TSN/Ethernet/ARINC664P7 Switch with customizable number of ports up to 1 Gbps.
- Support IEEE 1588 PTPV2 as GrandMaster or User
- Safe & Secure Ethernet communication
- Multi-protocol
-
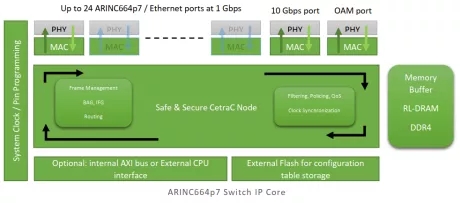
Multi Protocol Switch IP Core for Safe and Secure Ethernet Network
- "Ethernet/TSN/ARINC664P7 Switch with customizable number of ports up to 1 Gbps.
- Support IEEE 1588 PTPV2 as GrandMaster or User
- Safe & Secure Ethernet communication
- Multi-protocol
-
AES-SX-GCM-XTS-up Secure Core - AES Encryption Core with Extreme SCA Protection for Ultra-High-Security Applications
- The Ultra-Secure AES IP core is designed for applications where maximum resistance to side-channel attacks (SCA) is paramount, even beyond certification-grade requirements.
- Supporting AES-128/256 encryption in ECB, CBC, CTR, GCM, and XTS modes, the core is built for environments where redundancy in protection is a feature, not a cost.
-
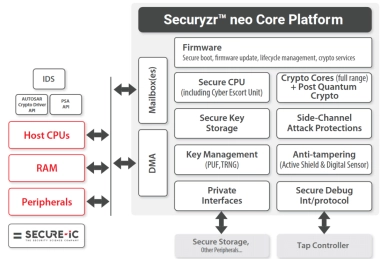
Securyzr™ neo Core Platform
- Securyzr™ neo Core Platform is Secure-IC’s enhanced version of its flagship offering Securyzr™ integrated Secure Element (iSE) Series.
- Thanks to its common platform, the entire Securyzr™ neo Series is now faster and more optimized than ever.
- With an optimal Power Performance Area (PPA), Secure-IC is offering a more comprehensive and mature solution to address all security needs from the different applications: spanning from IoT, Factory Automation, AIoT, Automotive, Cloud & Datacenter, to Mobile.
-
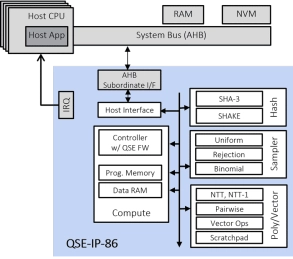
Fast Quantum Safe Engine for ML-KEM (CRYSTALS-Kyber) and ML-DSA (CRYSTALS-Dilithium)
- The Quantum Safe Engine (QSE) IP provides Quantum Safe Cryptography acceleration for ASIC, SoC and FPGA devices.
- The QSE-IP-86 core is typically integrated in a hardware Root of Trust or embedded secure element in chip designs together with a PKE-IP-85 core that accelerates classic public key cryptography and a TRNG-IP-76 core that generates true random numbers.
-
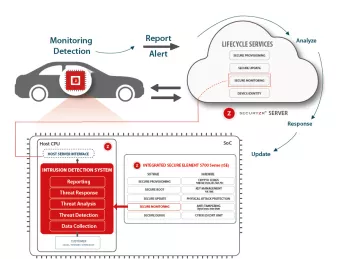
Intrusion Detection System (IDS)
- Part of a global threat detection, analysis and response solution form Chip-to-Cloud relying on Securyzr™ iSSP (integrated Security Services Platform).
- Compliance with standard and Regulation.
-
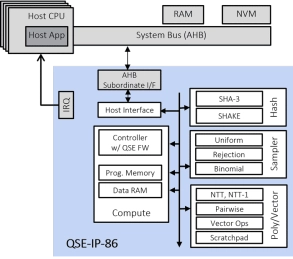
Fast Quantum Safe Engine for ML-KEM (CRYSTALS-Kyber) and ML-DSA (CRYSTALS-Dilithium) with DPA
- Compliant with FIPS 203 ML-KEM and FIPS 204 ML-DSA standards
- Uses CRYSTALS-Kyber, CRYSTALS-Dilithium quantum-resistant algorithms
- Includes SHA-3, SHAKE-128 and SHAKE-256 acceleration
- The embedded QSE CPU combined with Rambus-supplied firmware implements the full FIPS 203/204 protocols
-
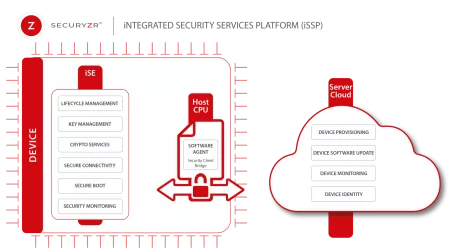
Integrated Security Services Platform (iSSP)
- The Securyzr™ iSSP (integrated Security Services Platform) enables Secure-IC customers and partners to supply, deploy and manage the embedded security of their devices’ fleet all along their lifecycle.
- The Securyzr™ iSSP is an easy & trustful end-to-end solution for zero-touch security lifecycle services such as provisioning, firmware update, security monitoring & device identity management.
-
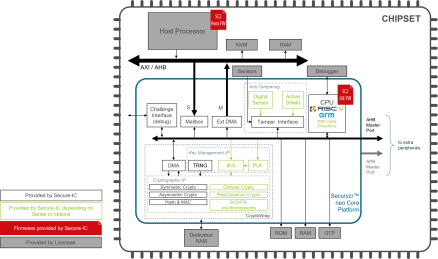
Root of Trust solutions
- Securyzr™ integrated Secure Element (iSE) is Secure-IC Root of Trust solution.
- Embedded in the main SoC, it offers multiple services to its host system: provisioning, secure boot, secure firmware update, cryptographic services, multiple protections, etc.
-
PUF Software Premium with key wrap and certification support
- Most flexible and scalable PUF-based security solution for new and existing designs
- Uses standard SRAM as a physical unclonable function (PUF) to create a hardware-based trust anchor which can be installed later in the supply chain, or even retrofitted on deployed devices
- Offers key provisioning, secure key storage, symmetric and asymmetric key cryptography, and data encryption on the fly
- Easy and collision-free identification of billions of devices (from various vendors)