Crypto Coprocessor IP
Filter
Compare
11
IP
from
5
vendors
(1
-
10)
-
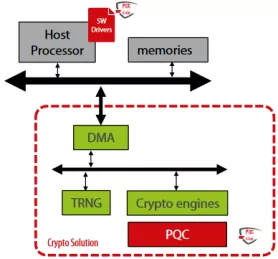
Crypto Coprocessor with integrated Post-Quantum Cryptography IPs
- The Crypto Coprocessors are a hardware IP core platform that accelerates cryptographic operations in System-on-Chip (SoC) environment on FPGA or ASIC.
- Symmetric operations are offloaded very efficiently as it has a built-in scatter/gather DMA. The coprocessors can be used to accelerate/offload IPsec, VPN, TLS/SSL, disk encryption, or any custom application requiring cryptography algorithms.
-
TLS 1.3 Compliant Crypto Coprocessor
- NIST CAVP certified and OSCCA standard compliant crypto engine suite
- Includes private/public key ciphers, message authentication code, hashes, and key derivation
- Key wrapping function for the secure export of keys
- Public-key coprocessor for digital signatures and key agreements over elliptic/Edward curves
-
Crypto Coprocessor
- Comprehensively support all CPU architectures
- Crypto engine collective, consisting of private key cipher, message authentication code, hash, and key derivation functions that are NIST CAVP certified and OSCCA standards compliant
- Key wrapping function aiding the export of keys for external use
-
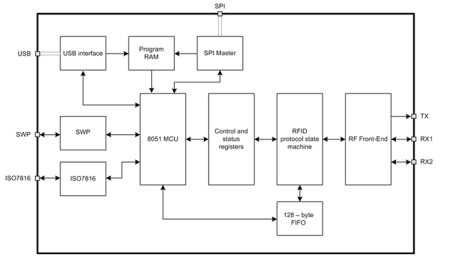
NFC/RFID Controller
- UMC CMOS 180 nm technology
- Complete RFID reader solution, including RF front-end and 8051-based MCU
- Supports ISO14443A* and ISO14443B standards in both reader and card emulation mode
- Supports NFC Initiator in both Active and Passive modes with speeds 212 and 424 Kbps
-
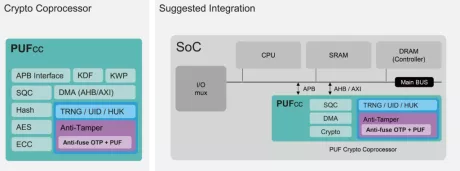
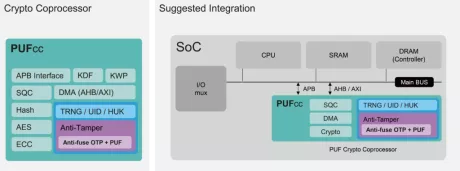
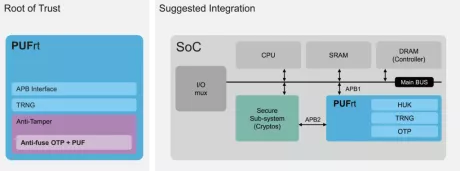
Hardware Root of Trust IP
- Built-in standard APB controller with privilege control to create secure/non-secure separation. Additionally, interface customization is available for different design requirements.
- Four 256-bit hardware PUF chip fingerprints, include a self-health check that can be used as a unique identification(UID) or a root key(seed).
- High-quality true random number generator (TRNG)
- 8k-bit mass production OTP with built-in instant hardware encryption (customization available)
-
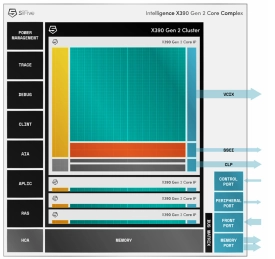
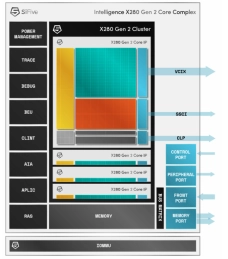
Multi-core capable RISC-V processor with vector extensions
- The SiFive® Intelligence™ X280 Gen 2 is an 8-stage dual issue, in-order, superscalar design with wide vector processing (512 bit VLEN/256-bit DLEN).
- It supports RISC-V Vectors v1.0 (RVV 1.0) and SiFive Intelligence Extensions to accelerate critical AI/ML operations.
-
Embedded Hardware Security Module (Root of Trust) - Automotive Grade ISO 26262 ASIL-B
- The RT-64x Embedded Hardware Security Module (Root of Trust) family are fully programmable, ISO 26262 ASIL-B hardware security cores offering security by design for automotive applications.
- They protect against a wide range of failures such as permanent, transient and latent faults and hardware and software attacks with state-of-the-art anti-tamper and security techniques.
-
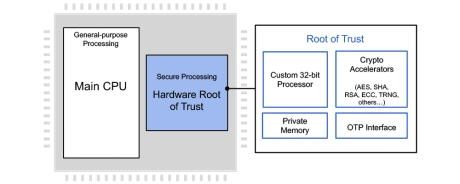
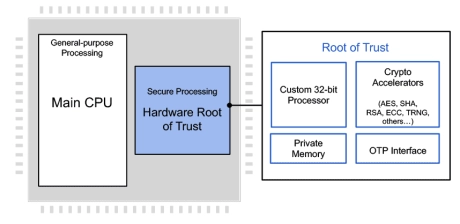
Programmable Root of Trust With DPA and FIA for US Defense
- Custom-designed 32-bit secure RISC-V processor
- Multi-layered security model protects all core components against a wide range of attacks
- Security model includes hierarchical privilege model, secure key management policy, hardware-enforced isolation/access control/protection, error management policy
- State-of-the-art DPA resistance, FIA protection and anti-tamper techniques
-
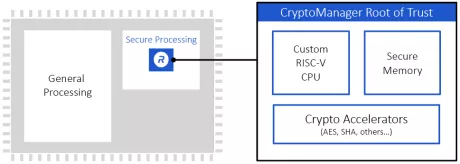
Programmable Root of Trust Family With DPA & Quantum Safe Cryptography
- Hardware Root of Trust employing a custom 32-bit RISC-V processor
- Multi-layered security model provides protection of all components in the core
- NIST CAVP and CMVP compliant for FIPS 140-3 validation
- State-of-the-art anti tamper techniques
- DPA-resistant cryptographic accelerators
- Caliptra Root of Trust for Measurement with DICE and X.509 support
-
8-stage dual issue, in-order, superscalar processor with dual vector processing units (1024-bit VLEN/512-bit DLEN)
- New RVA23 support
- New RVV1.0 512-bit vector engine
- New SSCI interface added alongside VCIX
- New instructions and extensions
- New improved memory subsystem