Why Hardware Security Is Just as Critical as Software Security in Modern Systems
Software tends to dominate security discussions, but it is only half of the equation. The other half is hardware security, which is often overlooked but equally important.
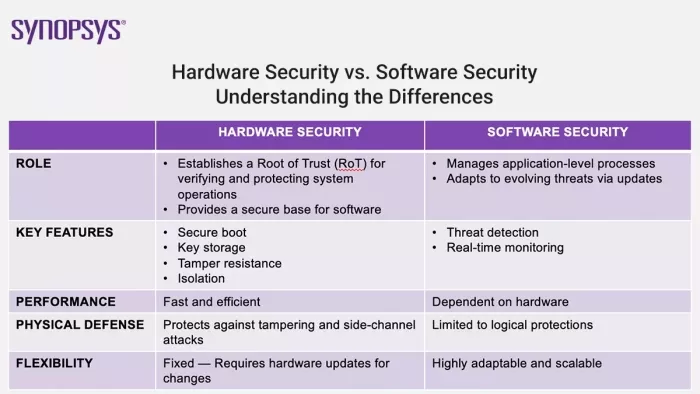
Hardware security — implemented at the silicon level across processors, storage components, input/output devices, and power supplies — and software security play distinct roles and have unique strengths.
And both must work in concert to fully protect modern computing systems.
The role of hardware security
Hardware security is the bedrock of any secure system. It provides the foundational trust, physical protection, and performance enhancements necessary to support software security. Without secure hardware, systems are like barrels with a hole at the bottom — even with the most advanced software security, sensitive data and cryptographic keys will inevitably "leak" out.
Core features of hardware security include tamper resistance, secure boot, hardware-based key storage, and trusted execution environments (TEEs). These features ensure systems:
- Start in a known good state
- Protect sensitive data
- Isolate critical operations from potential threats
Systems lacking these critical hardware features are inherently vulnerable.
Without hardware support for secure boot, for example, malicious code can be introduced during the boot process, compromising the system before the software even begins to operate. Similarly, cryptographic keys that are not protected by hardware are susceptible to extraction.
Hardware security benefits
Hardware security enhances the overall protection and performance of modern computing systems. And it provides layers of defense that are difficult or impossible to replicate with software alone.
- Root of Trust (RoT): Hardware helps establish a Root of Trust (RoT), which is essential for verifying and protecting the integrity and authenticity of a system’s operations. Secure boot functionality, for example, ensures the system starts in a known good state and prevents malicious code from compromising the system during the boot process. Hardware-based key storage protects cryptographic keys and makes them far less vulnerable to extraction through memory dumps or other software-based attacks.
- Physical protection: Software cannot defend against physical attacks, but hardware security peripherals offer a number of physical protections.
- Tamper-resistant features, such as Physical Unclonable Functions (PUFs), stop attackers from physically probing or altering the system to bypass security controls.
- Secure hardware makes it significantly more difficult to reverse engineer a system, uncover vulnerabilities, and extract sensitive information.
- Countermeasures against side-channel attacks — which are often impractical to implement in software without significant tradeoffs in performance and size — can be established using hardware-based cryptographic processors.
- Secure access to debugging ports using keys (stored in hardware or fuses) provides Joint Test Action Group (JTAG) and debugging channel protection. Keys provide flexibility but must be unique for each device, while fuses offer an irreversible, one-time solution to permanently disable access.
- Isolation: Hardware supports TEEs and hardware-enforced access controls to ensure sensitive operations and data are securely isolated. The goal is to prevent malware or compromised software from accessing critical data. Additionally, hardware security features can prevent attackers from exploiting shared resources (e.g., memory, CPUs) to gather and exfiltrate sensitive data.
- Performance: Dedicated hardware security is faster and more energy efficient than software implementations, especially for high-bandwidth solutions. For example, hardware-based cryptographic processors can handle x8 and x16 PCIe solutions, which software alone cannot support due to the high speeds required.
The role of software security
Software security has its own strengths. It supports complex, widely deployed security policies. It can be updated and patched over time, helping ensure systems remain resilient in the face of new vulnerabilities. And it enables rapid response to emerging attack vectors. All of these attributes make software security an essential component of any comprehensive security strategy.
- Flexibility: Software can be updated and reconfigured to address new threats without requiring changes to the underlying hardware.
- Scalability: Software-based solutions can be deployed across a wide range of devices and systems, making them highly versatile.
- Application-level functionality: Software security plays a critical role in enabling advanced application-level features, such as threat detection and response. Software tools can provide real-time monitoring and mitigation of risks, ensuring systems can quickly adapt to emerging attack vectors.
While software security is highly adaptable, its effectiveness is amplified when built on a foundation of secure hardware. Together, they create a robust defense against both known and emerging threats.
Establishing a unified security strategy
Hardware and software security are not separate entities but complementary components of a unified security strategy. Hardware provides the trust, physical protection, and performance enhancements on which software relies, while software delivers the flexibility and adaptability needed to respond to evolving threats. By working together, they create a resilient security posture that is greater than the sum of its parts.
For example, hardware-based key storage ensures cryptographic keys are protected, while software manages the use of those keys in application-level authentication processes. Similarly, hardware-based TEEs isolate sensitive operations, while software monitors for potential breaches.
In the battle against ever-evolving security threats, neither hardware nor software security can stand alone. Together, they form a unified defense that helps ensure systems are not only secure but also resilient and adaptable. By investing in both robust hardware and software security, organizations can build a fortress that stands the test of time.
Related Semiconductor IP
- tRoot V023 FS Hardware Secure Module, ASIL-B compliant (w/ ARC EM22FS)
- PCIe 5.0 Integrity and Data Encryption Security Module
- 1-port Receiver or Transmitter HDCP 2.3 on HDMI 2.1 ESM
- tRoot Vx Hardware Secure Modules
- tRoot V500 Hardware Secure Module
Related Blogs
- Why thinking about software and security is so important right at the start of an ASIC design
- Cryptographic Modules Provide Critical Security in a Unified and Isolated Hardware Solution
- Why SRAM PUF Technology Is the Bedrock of Dependable Security in Any Chip
- Business Models: EDA Is Software But It Used To Be Sold As Hardware
Latest Blogs
- Silicon Insurance: Why eFPGA is Cheaper Than a Respin
- One Bit Error is Not Like Another: Understanding Failure Mechanisms in NVM
- Introducing CoreCollective for the next era of open collaboration for the Arm software ecosystem
- Integrating eFPGA for Hybrid Signal Processing Architectures
- eUSB2V2: Trends and Innovations Shaping the Future of Embedded Connectivity