Security IP for TSMC
Welcome to the ultimate
Security IP
for
TSMC
hub! Explore our vast directory of
Security IP
for
TSMC
All offers in
Security IP
for
TSMC
Filter
Compare
42
Security IP
for
TSMC
from
7
vendors
(1
-
10)
-
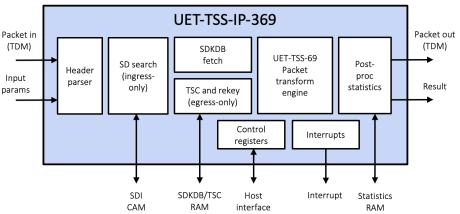
Multi-channel Ultra Ethernet TSS Complete Layer
- The UET-TSS-IP-369 (EIP-369) is an inline, high-performance, multi-channel packet engine that provides the complete TSS layer, bypass/drop and basic crypto processing at rates up to 1.6Tbps.
- The engine is designed for integration into the systems that require TSS processing for one or more ports. The engine is provided as separate ingress and egress data paths.
- The EIP-369 embeds the UET-TSS-IP-69 for the packet transformation.
-
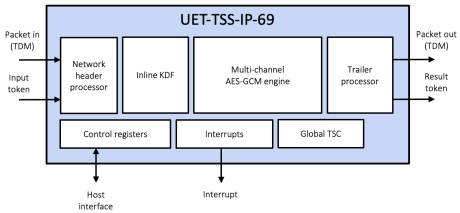
Multi-channel Ultra Ethernet TSS Transform Engine
- The UET-TSS-IP-69 (EIP-69) is a high-performance, multi-channel transform engine that provides the complete TSS packet transformation (including KDF and IP/UDP updates), bypass/drop and basic crypto processing at rates up to 1.6Tbps.
- The engine is designed for integration into the systems that require TSS processing for one or more ports. The engine is provided as separate ingress and egress data paths.
-
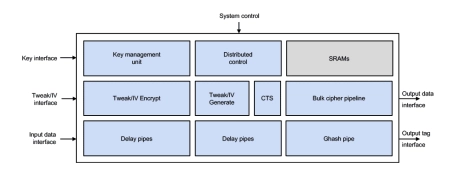
Fast Inline Cipher Engine, AES-XTS/GCM, SM4-XTS/GCM, DPA
- One input word per clock without any backpressure
- Design can switch stream, algorithm, mode, key and/or direction every clock cycle
- GCM: throughput is solely determined by the data width, data alignment and clock frequency
- XTS: block processing rate may be limited by the number of configured tweak encryption & CTS cores; a configuration allowing 1 block/clock is available
-
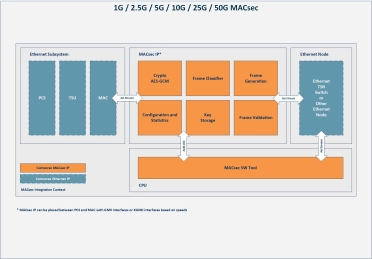
1G/2.5G/5G/10G/25G/50G MACsec
- The MACsec IP provides Ethernet Layer 2 Security for port authentication, data confidentiality and data integrity as standardized in IEEE 802.1AE.
- It protects components in Ethernet networks especially high-speed Ethernet used in automotive, industrial, cloud, data center, and wireless infrastructure.
- The MACsec IP is a fully compliant solution that provides line-rate encryption and supports VLAN-in-Clear.
-
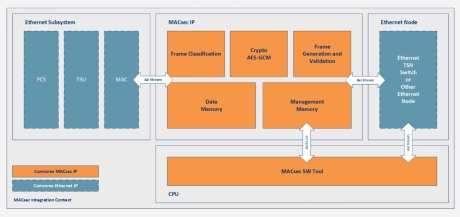
10M MACsec
- The MACsec IP provides Ethernet Layer 2 Security for port authentication, data confidentiality and data integrity as standardized in IEEE 802.1AE.
- It protects components in Ethernet networks especially very low-speed Ethernet used in automotive, industrial, and consumer applications.
- The MACsec IP is a fully compliant solution that provides line-rate encryption and is optimized for the smallest area size.
-
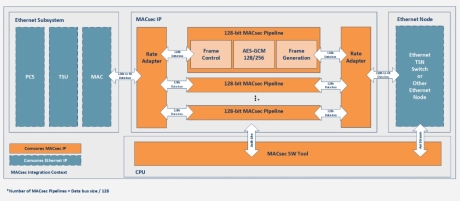
100G / 200G / 400G / 800G / 1.6T MACsec
- The MACsec IP provides Ethernet Layer 2 Security for port authentication, data confidentiality and data integrity as standardized in IEEE 802.1AE.
- It protects components in Ethernet networks especially very high-speed Ethernet used in cloud, data center, and backhaul networks.
- The MACsec IP is a fully compliant solution that provides line-rate encryption and supports VLAN-in-Clear.
-
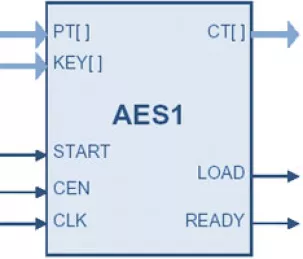
Ultra-Compact Advanced Encryption Standard (AES, FIPS-197) Core
- Encrypts using the AES Rijndael Block Cipher Algorithm.
- Satisfies Federal Information Processing Standard (FIPS) Publication 197 from the US National Institute of Standards and Technology (NIST). FIPS-197 validated (AESAVS).
- Processes 128-bit data blocks with 8, 16 or 32-bit data interface
- Employs key sizes of 128 bits (AES128), 192, or 256 bits (AES256)
-
802.15.3 CCM AES Core
- Small size: From 9,500 ASIC gates at 802.15.3 data Speeds.
- High data rate: up to 8 Gbps for IEEE 802.15.3c / ECMA-387 (TC 48) / IEEE 802.11ad 60 GHz PHY
- Completely self-contained: does not require external memory
- Includes encryption, decryption, key expansion and data interface
-
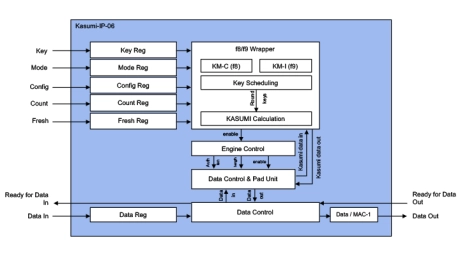
3GPP Kasumi Accelerators
- Wide bus interface (64-bit data, 128-bit keys) or 32-bit register interface.
- Includes key scheduling hardware.
- Modes Kasumi
- Algorithms f8 and f9.
- Fully synchronous design.
- Low Speed, High Speed versions.
-
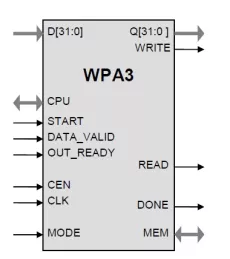
802.11i CCMP/TKIP IP Core
- Implementation of the WLAN security standard (802.11i) requires the NIST standard AES cipher in CTR and CBC modes (a.k.a. CCM) for encryption and message authentication with the CCMP protocol and RC4/”Michael” cipher for the TKIP.
- The WPA3 core is tuned for high data rate 802.11i applications (up to 2 Gbps for the CCMP protocol for 802.11n/802.11ac).