ioPUF+: A PUF Based on I/O Pull-Up/Down Resistors for Secret Key Generation in IoT Nodes
By Dilli Babu Porlapothula ∗, Pralay Chakrabarty ∗, Ananya Lakshmi Ravi †, and Kurian Polachan ∗
∗ International Institute of Information Technology, India
† Indian Institute of Information Technology, India
Abstract
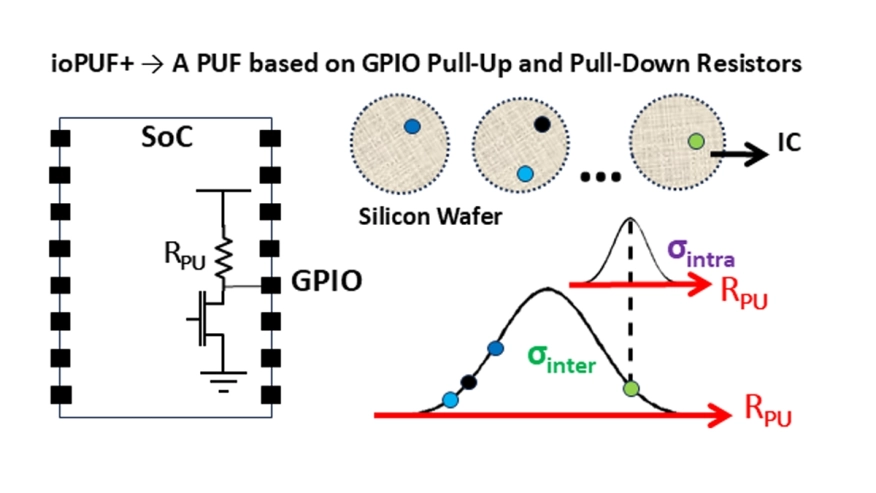
 In this work, we present ioPUF+, which incorporates a novel Physical Unclonable Function (PUF) that generates unique fingerprints for Integrated Circuits (ICs) and the IoT nodes encompassing them. The proposed PUF generates device specific responses by measuring the pull-up and pull-down resistor values on the I/O pins of the ICs, which naturally vary across chips due to manufacturing-induced process variations. Since these resistors are already integrated into the I/O structures of most ICs, ioPUF+ requires no custom circuitry and no new IC fabrication. This makes ioPUF+ suitable for cost-sensitive embedded systems built from Commercial Off-The-Shelf (COTS) components. Beyond introducing a new PUF, ioPUF+ includes a complete datapath for converting raw PUF responses into cryptographically usable secret keys using BCH error correction and SHA-256 hashing. Furthermore, ioPUF+ demonstrates a practical use case of PUF-derived secret keys in securing device to-device communication using AES encryption.
In this work, we present ioPUF+, which incorporates a novel Physical Unclonable Function (PUF) that generates unique fingerprints for Integrated Circuits (ICs) and the IoT nodes encompassing them. The proposed PUF generates device specific responses by measuring the pull-up and pull-down resistor values on the I/O pins of the ICs, which naturally vary across chips due to manufacturing-induced process variations. Since these resistors are already integrated into the I/O structures of most ICs, ioPUF+ requires no custom circuitry and no new IC fabrication. This makes ioPUF+ suitable for cost-sensitive embedded systems built from Commercial Off-The-Shelf (COTS) components. Beyond introducing a new PUF, ioPUF+ includes a complete datapath for converting raw PUF responses into cryptographically usable secret keys using BCH error correction and SHA-256 hashing. Furthermore, ioPUF+ demonstrates a practical use case of PUF-derived secret keys in securing device to-device communication using AES encryption.
We implemented ioPUF+ on the Infineon PSoC-5 microcon troller and evaluated its performance across 32 devices using standard PUF metrics. The results show excellent reliability of 100% (zero intra-device Hamming distance), strong uniqueness (inter-device Hamming distance of 50.33%), near-ideal unifor mity (50.54%), and negligible bit aliasing. Stability tests under temperature and supply-voltage variations show worst-case bit error rates of only 2.63% and 2.10%, respectively. We also profiled the resource and energy usage of the complete ioPUF+ system, including the PUF primitive, BCH decoding, SHA-256 hashing, and AES encryption. The full implementation requires only 19.8 KB of Flash, exhibits a latency of 600 ms, and consumes 79 mW of power, demonstrating the suitability of ioPUF+ for resource-constrained IoT nodes.
Index Terms—Physical Unclonable Functions (PUFs), Internet of Things (IoT), hardware security
To read the full article, click here
Related Semiconductor IP
- Digital PUF IP
- PUF IP
- PUF FPGA-Xilinx Premium with key wrap
- PUF FPGA-Xilinx Base
- ASIL-B Ready PUF Hardware Premium with key wrap and certification support
Related Articles
- PUF based Root of Trust PUFrt for High-Security AI Application
- A Comprehensive Post-Quantum Cryptography (PQC) Solution based on Physical Unclonable Function (PUF)
- Context Based Clock Gating Technique For Low Power Designs of IoT Applications - A DesignWare IP Case Study
- PUF: A Crucial Technology for AI and IoT
Latest Articles
- GenAI for Systems: Recurring Challenges and Design Principles from Software to Silicon
- Creating a Frequency Plan for a System using a PLL
- RISCover: Automatic Discovery of User-exploitable Architectural Security Vulnerabilities in Closed-Source RISC-V CPUs
- MING: An Automated CNN-to-Edge MLIR HLS framework
- Fault Tolerant Design of IGZO-based Binary Search ADCs