HMAC IP
Filter
Compare
49
IP
from
16
vendors
(1
-
10)
-
Security Hash, SM3 Hash and HMAC Engine
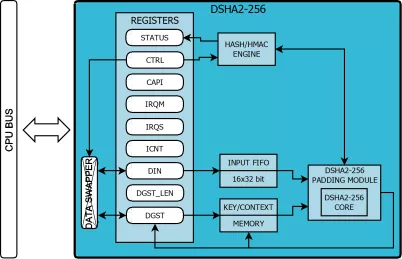
- The hash processor is a fully compliant implementation of the secure hash algorithm (SHA-1, SHA-224, SHA-256, SHA-384, SHA-512), the MD5 (message-digest algorithm 5) and SM3 hash algorithm and the HMAC (keyed-hash message authentication code) algorithm suitable for a variety of applications. HMAC is suitable for applications requiring message authentication.
-
Hash and HMAC Functions Accelerator
- FIPS PUB 180-4 compliant SHA2-256 function
- RFC 2104 compliant HMAC mode native support
- SHA2 224 and 256 bit modes support
- Secure storage for precomputed HMAC keys
-
HMAC-SHA256 Secure Core - Hardware Accelerator for SHA-2 and HMAC with Low Latency SCA/FI Protection
-
Hardware Accelerator for SHA-2 and HMAC with Low Latency SCA/FI Protection
-
-
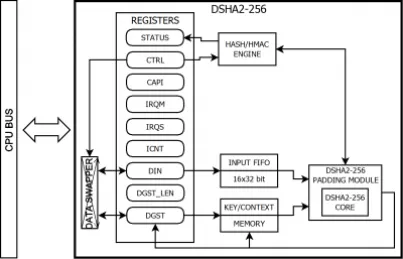
SHA IP Core with native SHA2-256 HMAC support
- FIPS PUB 180-4 compliant SHA2-256 function
- RFC 2104 compliant HMAC mode native support
- SHA2 224 and 256 bit modes support
-
SHA-1, SHA-2, SHA-3 Hash based HMAC, accelerators
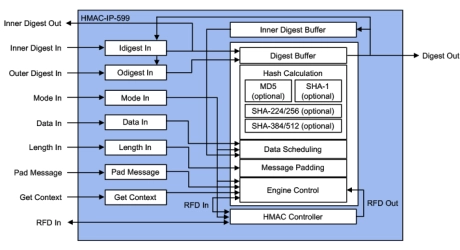
- HMAC-IP-59 (EIP-59) is IP for accelerating the various single pass HMAC (FIPS-198-1) algorithms using secure hash integrity algorithms like MD5 (RFC1231), SHA-1 (FIPS-180-2), SHA-2 (FIPS-180-3/4) and SHA-3 (FIPS-202), up to 8 Gbps.
- Designed for fast integration, low gate count and full transforms, the HMAC-IP-59 accelerators provide a reliable and cost-effective embedded IP solution that is easy to integrate into high-speed crypto pipelines.
-
HMAC-SHA256 cryptographic accelerator
- Hardware Root of Trust
- Widely used password hash algorithm
- Security Critical HTTP, SSL, TLS
- Key storage in Private memory

-
Zero Leakage HMAC-SHA256/512 Secure Core - High-Security SHA-2/HMAC Core with Zero Side-Channel Leakage Guarantee
-
Zero Leakage HMAC-SHA256 Secure Core - High-Security SHA-2/HMAC Core with Zero Side-Channel Leakage (SHA-224/256 Only)
- High-Security SHA-2/HMAC Core with Zero Side-Channel Leakage (SHA-224/256 Only)
-
HMAC-SHA256/512 Secure Core - High-Performance SHA-2/HMAC Accelerator with Full SHA-2 Family Support and Low Latency SCA/FI Protection
-
High-Performance SHA-2/HMAC Accelerator with Full SHA-2 Family Support and Low Latency SCA/FI Protection
-
-
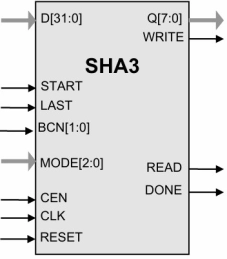
SHA3 Cryptographic Hash Cores
- Completely self-contained; does not require external memory
- SHA3-224, SHA3-256, SHA3-384, and SHA3-512 support SHA-3 algorithms per FIPS 202.
- SHAKE128 / SHAKE256 XOF support is included.
- Flow-through design; flexible data bus width