How to Design Secure SoCs: Essential Security Features for Digital Designers
By Kivicore
Intro
In today’s rapidly advancing technological landscape, System-on-Chip (SoC) designs have become the backbone of numerous industries, powering everything from medical devices to aerospace systems, telecommunications, and automotive solutions. As these chips integrate more functions and performance into a single unit, the need for robust security has never been more critical. For ASIC and SoC design companies, ensuring that chips are secure from the outset is not just a technical challenge; it is an imperative to safeguard intellectual property, user data, and system integrity. As these devices become more interconnected, the risks associated with vulnerabilities in SoC designs have grown exponentially.
In this comprehensive guide, we will explore the essential components of secure SoC design and explain how a robust security subsystem can protect sensitive assets throughout the chip’s lifecycle. Additionally, we will dive into how KiviCore’s specialized consultancy services can help ASIC and SoC design companies navigate the complex security landscape, ensuring the creation of secure and reliable chips that meet the rigorous demands of industries like IoT, data processing, consumer, telecommunication and beyond.
Why Security in SoC Design is Critical for ASIC/SoC Designers
SoC designs have become the heart of most modern electronic devices, integrating processors, graphical and AI accelerators, memory, data communication peripherals, and other hardware into a single chip. However, this integration, while offering tremendous efficiency and cost savings, also introduces security vulnerabilities. A compromised SoC could lead to catastrophic consequences, such as data breaches, theft of intellectual property, or even physical damage to the hardware.
For ASIC and SoC designers, ensuring the security of the entire design process—from conception through to post-deployment—is paramount. A single weak link in the design chain could leave the system open to attack, rendering it vulnerable to exploitation. Therefore, integrating security at every phase of the SoC lifecycle is critical for protecting the chip's integrity and the systems that rely on it. This is especially important in highly regulated industries, where failure to meet security standards can result in non-compliance and legal ramifications.
Furthermore, with the increasing sophistication of cyberattacks, the risk of malicious actors exploiting vulnerabilities in SoC designs is rising. Attack vectors such as side-channel attacks, firmware vulnerabilities, and unauthorized access to cryptographic keys have become more prevalent, making it essential to build robust defense mechanisms into the chip’s architecture from the very start.
Key Components of a Secure SoC Design
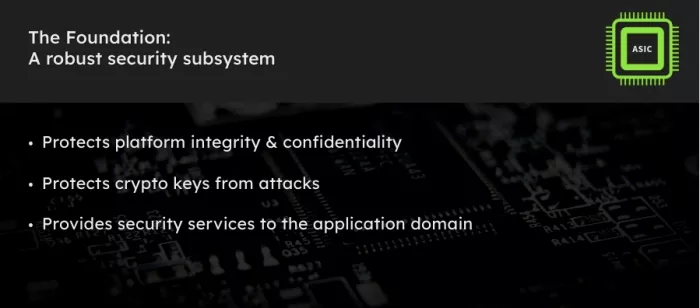
1. Security Subsystem Architecture: The Foundation of SoC Security
The security subsystem is the central component of any secure SoC design. Its primary purpose is to protect the confidentiality, integrity, and availability of critical assets such as cryptographic keys, software, firmware, and data. By isolating these sensitive assets from the rest of the chip's operations, the security subsystem creates a secure environment that prevents unauthorized access.
The architecture is typically divided into two main parts:
- Application: This part of the SoC comprises the main application logic, user data, and peripherals. It is where most of the chip’s computational tasks occur.
- Security Subsystem: This part is isolated from the application part and comprises sensitive elements such as cryptographic keys, trusted execution environments (TEEs), and security configurations. By keeping critical assets separate, the security subsystem ensures that even if the application part is compromised, the sensitive data remains secure.
This separation is essential for preventing unauthorized access to critical security components, ensuring that even if an attacker gains control over the application domain, the security subsystem is still protected.
2. Cryptographic Key Management: Securing the Core of Confidentiality
Cryptographic key management is fundamental to securing SoC designs. Keys are used in many functions, from encrypting communication to authenticating firmware. The key management system should ensure that keys are securely generated, stored, and managed throughout the chip’s lifecycle. Importantly, keys should never leave the secure boundaries of the security subsystem.
- Key Generation: Cryptographic keys should be generated within the security subsystem to minimize the risk of exposure during key creation. The process must involve strong random number generation techniques to ensure key unpredictability and security.
- Key Derivation: To prevent key exposure during transmission, key derivation processes should be employed. This allows the system to generate temporary keys based on master keys without exposing the master key itself.
- Key Import/Export: In many use cases, keys are imported from trusted sources or exported for secure storage. To ensure security, key import and export operations should be cryptographically protected, and only authorized processes should have access to these operations.
By implementing a robust key management system within the security subsystem, SoC designers can ensure that cryptographic keys are handled securely and are not exposed to potential attackers at any point in the device’s lifecycle.
3. Secure Boot: Protecting the SoC from the First Moment
Secure boot is one of the most critical security features in modern SoCs. It ensures that the chip boots only trusted and authenticated code by verifying the integrity and authenticity of the firmware before it is executed. Without secure boot, a malicious actor could exploit the boot process, loading their own firmware or modifying legitimate code to compromise the system.
- Firmware Verification: During secure boot, the bootloader verifies the integrity of the firmware using cryptographic techniques like digital signatures or hashes. If the firmware does not match the expected signature, the system either prevents booting or takes corrective actions, such as resetting the device or switching to a safe mode.
- Chain of Trust: Secure boot creates a "chain of trust," where each component in the boot process is verified before execution. Starting with the hardware root of trust, each stage of the boot process verifies the next stage’s integrity, ensuring that only verified and trusted code can be executed.
By employing secure boot, SoC designers can prevent unauthorized code from running on the device, which is crucial for protecting against rootkits and other malicious attacks.
4. Runtime Integrity Protection: Securing the Application in Operation
After the SoC has been booted, it must remain secure during its operational lifecycle. Runtime integrity protection ensures that the SoC remains in a secure state while executing its functions, preventing unauthorized modifications or tampering during normal operation.
- Memory Protection: Memory protection mechanisms ensure that critical data, such as firmware and configuration settings, are protected against unauthorized access and modification. This is especially important for preventing attacks like buffer overflow exploits, where an attacker attempts to overwrite memory to execute malicious code.
Security Sensors: Security sensors within the SoC monitor the chip for signs of physical attacks, such as voltage manipulation or electromagnetic interference (EMI) attacks. If any such anomalies are detected, the security subsystem can trigger countermeasures like resetting the device or shutting down certain components to prevent further exploitation.
These runtime protection mechanisms help to ensure that the SoC remains secure throughout its entire operational lifecycle, minimizing the risks of real-time attacks.
5. Data Protection and Encryption: Ensuring Confidentiality
One of the primary functions of a secure SoC is to protect sensitive data from unauthorized access. This is achieved through encryption, which ensures that data remains confidential whether it is being stored or transmitted. SoCs should support both symmetric and asymmetric encryption techniques, depending on the use case.
- On-the-Fly Encryption: On-the-fly encryption automatically encrypts or decrypts data as it is read from or written to memory, with these operations transparently handled by dedicated hardware components. This transparent process ensures that the application does not need to explicitly call for encryption, simplifying development and enhancing security.
Data Authentication: In addition to encryption, data authentication mechanisms like message authentication codes (MACs) or digital signatures can be used to verify the integrity and authenticity of data. This ensures that data has not been tampered with while in transit or while stored.
By employing both encryption and data authentication, SoCs can safeguard sensitive information from unauthorized access or alteration.

Designing for Platform Integrity
Platform integrity ensures that the SoC remains trustworthy not just in terms of data confidentiality but also in terms of maintaining the security of the system as a whole.
- System Configuration and Policies: The security subsystem defines and enforces policies for how system resources can be accessed and used. These policies can specify which components of the system can be accessed, which firmware versions are allowed to run, and whether certain operations (like debug access) are permitted.
- Monotonic Counters: Monotonic counters provide a reliable way to ensure the freshness of data and prevent rollback attacks. Typically implemented in hardware or secure firmware, these counters increment with each significant system event, enabling the system to detect and reject outdated or replayed data, especially during firmware updates and secure transactions. These counters can be used to track system state changes and ensure that each event is counted only once.
By employing platform integrity techniques like these, SoC designers can ensure that the chip remains in a secure state throughout its lifecycle.
Secure System Lifecycle Management
An SoC's lifecycle spans from its initial design and manufacturing to its deployment and eventual decommissioning. Throughout each phase of this lifecycle, security measures must be enforced to ensure that the device remains secure.
- Initial Configuration: During the manufacturing process, SoC designers provision the device with cryptographic keys and firmware. The security subsystem ensures these assets are securely stored and protected against unauthorized modification.
- In-Field Lifecycle: Once the SoC is deployed, it enters the in-field lifecycle, where security measures continue to be enforced. This includes controlling access to firmware updates, managing key rotations, and ensuring secure communication with other devices in the system.
- Failure Analysis: In the event of a breach or hardware failure, the security subsystem can transition the device into a failure analysis mode, where sensitive data is wiped and the system is returned to a safe state.
By managing security throughout the SoC's entire lifecycle, from manufacturing to deployment and beyond, designers can ensure that the device remains secure against evolving threats.
How KiviCore Can Help ASIC/SoC Design Companies
At KiviCore, we specialize in providing services that help ASIC/SoC design companies build secure chips from the ground up. Our team of experts works closely with clients to integrate security into every phase of the design and development process, ensuring that chips meet the rigorous security standards required by industries like aerospace, medical devices, and telecommunications.
Our services include:
- Security Architecture Design: We help integrate robust security subsystems that protect critical assets and platform integrity throughout the SoC’s lifecycle.
- Cryptographic Key Management: We provide solutions to securely handle, generate, store, and manage cryptographic keys within your SoC design.
- Secure Boot and Runtime Integrity: We assist in implementing secure boot and runtime integrity features to protect the system from unauthorized code execution.
- Data Protection and Encryption Services: Our team ensures your SoCs meet modern encryption standards to secure data in storage and during transmission.
- Lifecycle Security Management: We provide end-to-end solutions to manage the secure lifecycle of your SoC, from initial design to deployment and beyond.
Learn more about ASIC/SoC Services
Conclusion
Designing secure SoCs is essential for protecting not only the devices themselves but also the sensitive data and intellectual property they handle. By incorporating robust security features such as secure boot, cryptographic key management, and runtime integrity protection, designers can safeguard against a growing range of cyber threats. KiviCore’s expertise in embedding security across all phases of SoC design ensures that chips meet the highest industry standards, delivering resilience against vulnerabilities and enhancing overall system integrity. As the demand for secure and efficient SoCs continues to rise, integrating comprehensive security solutions from the outset is no longer optional but a critical necessity. Through our specialized consultancy services, KiviCore is committed to helping ASIC and SoC design companies navigate the complexities of this evolving landscape, ensuring that their designs are not only cutting-edge but also secure and future-proof.
Related Semiconductor IP
- Post-Quantum Key Encapsulation IP Core
- Keccak Hash Engine
- SHA-3 Crypto IP Core
- NPU IP Core for Mobile
- NPU IP Core for Edge
Related White Papers
- How to design secure SoCs, Part II: Key Management
- How to design secure SoCs, Part III: Secure Boot
- How to reuse your IIoT technology investments - now
- It's Not My Fault! How to Run a Better Fault Campaign Using Formal
Latest White Papers
- Breaking the Memory Bandwidth Boundary. GDDR7 IP Design Challenges & Solutions
- Automating NoC Design to Tackle Rising SoC Complexity
- Memory Prefetching Evaluation of Scientific Applications on a Modern HPC Arm-Based Processor
- Nine Compelling Reasons Why Menta eFPGA Is Essential for Achieving True Crypto Agility in Your ASIC or SoC
- CSR Management: Life Beyond Spreadsheets