ARM Security Solutions and Intel Authenticated Flash -- How to integrate Intel Authenticated Flash with ARM TrustZone for maximum system protection
John Rudelic, Principal Engineer, Intel
Introduction
Through a combination of integrated hardware and software components, ARM TrustZone technology provides the basis for a highly-protected system architecture targeted specifically at securing consumer products such as mobile phones, PDAs, set-top boxes or other systems running open Operating Systems (OS), such as Symbian OS, Linux and Windows CE.
By integrating security logic internal to the flash memory, the Intel® Authenticated Flash memory provides a basis for strong integrity protection by preventing unauthorized modifications to the flash memory. The Intel Authenticated Flash memory also provides authenticated memory access control and protected key storage features. The Intel Authenticated Flash memory is also targeted at consumer products.
The combination of ARM's Security Solutions, including TrustZone, with Intel Authenticated Memory provides a more secure platform than either technology can provide independently.
Why is Security So Important?
There are many examples of the very significant costs associated with the failure of embedded systems to resist malicious attacks. These span multiple applications and industry segments, and include both direct costs and lost revenue opportunities. The need to improve security has been particularly driven by the ever-increasing spread of wireless systems that encompass data services and payment applications.
The top threats are being driven by several factors, such as an exponential growth in the connectivity options for devices, a transition to open operating systems, an increase in the amount and type of valuable data maintained by the system, and the increased utilization of mobile devices as enterprise mobile information appliances.
The top threats within the mobile device are: 1) protection of system boot integrity; 2) protection of the operating system integrity 3) protection and isolation of security critical applications (e.g., payment application) 4) protection of access control information such as IMEI numbers or SIMLock configuration 5) resistance to virus attacks; 6) resistance to code vulnerability exploits, and 7) digital rights concerns.
ARM Approach - The TrustZone Solution
ARM's approach to enabling trusted computing within the embedded world is based on the concept of trusted execution of code and hardware isolation. TrustZone consists of a hardware-enforced security environment providing code isolation, together with secure software that provides both the fundamental security services and interfaces to other elements in the trusted chain, including smartcards, operating systems and general applications.
TrustZone separates two parallel execution worlds: the non-secure 'normal' execution environment, and a trusted, certifiable secure world. (Figure 1) This is achieved through architectural modifications inside the CPU rather than by the addition of complex and frequently expensive logic outside the CPU. There are also significant performance advantages in this approach, such as faster transition times between secure and non-secure worlds due to cache memory awareness of the new state. A common foundation approach from within the CPU architecture also ensures that the basic infrastructure for security, as well as interoperability and software compatibility, are in place.
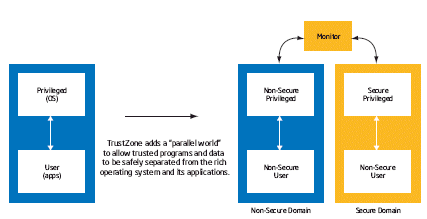
Figure 1
Key Benefits of TrustZone
TrustZone offers a number of key technical and commercial benefits to developers and end-users. These include:
-
Primarily, TrustZone provides a safe environment for secure data and code on the chip. This enables a complete approach to security. For example, processing secure keys from a secure SIM card using the SoC CPU and enabling the code handling sensitive material to run securely can typically, only be performed safely if there is a safe area within the SoC. In the case of the Intel Authenticated Memory, extra integrity protections are provided. A traditionally open and rich OS is part of the solution but probably insufficient to enable this.
-
Performance is an issue in some secure systems, especially in configurations where traffic must be encrypted between the core processor and an external store. With TrustZone, full bus-bandwidth access is provided to all storage areas to provide fast memory access speeds. In addition, safe local cache data is stored securely in decrypted form providing even faster access. The encrypted data can access the same Flash memory as the non-secure world, ensuring cheap, large and flexible storage is utilized.
-
Because the TrustZone solution consists of software and hardware elements, it provides flexibility to allow customization and upgrades to the secure system even after the SoC is finalized.
-
TrustZone defines a secure world within the embedded system. This can include direct peripheral channels, the user interface, SIM and smart cards as well as audio output. For the non-secure world, TrustZone can enable security through integrity checking for all the features within a SoC device. For example, decoded DRM audio can be protected as it is passed to non-secure audio drivers by integrity checking the relevant part of the OS infrastructure.
As well as providing full on-chip security for a SoC device, TrustZone can also be extended to enable security on systems that utilize offchip memory. While this architecture is inherently less safe from physical attack than a system that uses on-chip memory (for example, it can be removed and interfered with) TrustZone can nevertheless enhance the overall security of such systems. Although the architectural aspects of TrustZone are implemented within the latest ARM11 CPUs, the TrustZone Software introduces the concept of open APIs to enable a rich ecosystem that can indeed be extended to all the ARM CPUs.
TrustZone Operation
TrustZone operates by enforcing a level of trust at each stage of a transaction, including system boot. The trusted code will handle tasks such as the protected decryption of messages using the recipient's private key, and verification of the authenticity of the signature based on the sender's public key. TrustZone does this by executing secure commands within a parallel trusted execution environment.
TrustZone introduces a new secure state to the ARM architecture for both User and the existing Privileged modes. This determines whether the system is operating within the Secure or Non-Secure World. A new mode, Secure Monitor, controls switching between the Secure and Non-Secure World. The new instruction, SMI (Secure Monitor Interrupt) provides the main route to change Worlds.
A TrustZone-based SoC implementation will consist of both secure and non-secure elements. Key components include:
-
A TrustZone CPU that is used to run trusted applications isolated from normal applications, and to access the memory space reserved for trusted applications
-
Secure on-chip boot ROM to configure the system
-
On-chip non-volatile or one-time programmable memory for storing device or master keys
-
Secure on-chip RAM used to store and run trusted code such as DRM engines and payment agents, or to store sensitive data such as encryption keys
-
Other resources, such as peripherals, that can be configured to allow access by trusted applications only
TrustZone Software Elements
Software for a TrustZone-enabled device consists of both nonsecure elements, such as the normal OS and applications, and the protected software components. The TrustZone-optimized secure software components include the Monitor software, which enables the interface between the Secure and Non-Secure Worlds, the Secure Kernel, Secure Drivers and Boot Loader, and basic secure software services that will be provided by ARM as part of the software solution. (Figure 2)
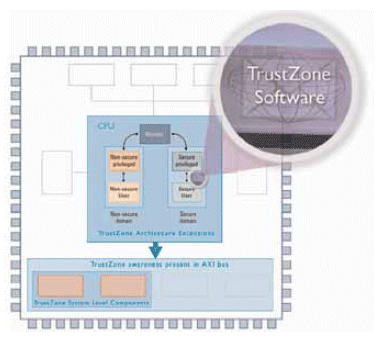
Figure 2
The TrustZone-optimized software operates as a secure kernel and implements the TrustZone Software APIs. This can be ported to any ARM CPU, and provides security roadmap compatibility for future TrustZone devices.
The TrustZone Software features an independent and certifiable secure framework. It has exclusive access to dedicated protected memory, dedicated persistent storage, crypto-accelerators and a possible trusted user Interface. By way of security services, it can provide services such as integrity checking (SIMLock, IMEI protection, secure boot), access control, secure storage and cryptography services. Services coming from the ecosystem community may include frameworks for DRM, remote authentication or e-banking.
Designing with TrustZone Technology
The design of protected systems must be approached in such a way that security issues are considered from the outset, including the implications for the control of protected code during the development process. (Figure 3)
Key questions must be addressed before undertaking the design, in order to specify the elements of the design chain, the components to enable the entire solution, and the potential architecture decisions and trade-offs.
- What level of security is required?
- Fully on-chip SoC
- On-chip SoC but signed code from off chip SoC
- On-chip SRAM with code executed from a protected memory such as the Intel Authenticated Memory.
- Software-only protection so can run fully off-chip SoC
- How do you control the development of protected code?
- Who holds the on-SoC Master Key?
- Who authors the on-chip SoC boot code?
- What other key management is required for trusted developers working behind the TrustZone security barrier?
Other industry intellectual property, or proprietary components, may be required to fulfill specific implementations. This may include DRM IP, on-chip ROM and other off-chip security resources such as cryptography accelerators
As with any complex SoC design, there are architectural parameters and hardware software tradeoffs to be made. These are determined by the security requirements,
For example:
- On-chip RAM is expensive
- If the main concern is software attacks then off-chip execution is acceptable given suitable memory partitioning.
- On-chip ROM is inflexible
- The ability to load code into protected RAM needs to be considered
- Such code must be authorized and signed/checked in some manner
- Off-chip protected memory such as Intel Authenticated Flash memory (described in more detail later)
- Use of off-chip protected memory can reduce the size of SOC RAM by relying on the integrity protection provided by the Intel Authenticated Flash memory
- Off-chip protected memory can also be used to reduce the size of SOC ROM while providing flexibility to update the code in a secure fashion
- Off-chip protected memory can also extend the code integrity protection beyond the secure applications to provide integrity protection for the operating system and applications
Intel Approach - The Authenticated Flash Advantage
Intel's approach to supporting trusted computing is based on the concept of protected memory. Intel Authenticated Flash consists of a standard flash memory that has integrated an RSA engine, a SHA- 1 engine and a hardware RMG (random number generator). By integrating the security logic with the flash memory, Intel can deliver a memory technology that can prevent unauthorized modifications, provide hardware access control and support protected key storage. (Figure 4)
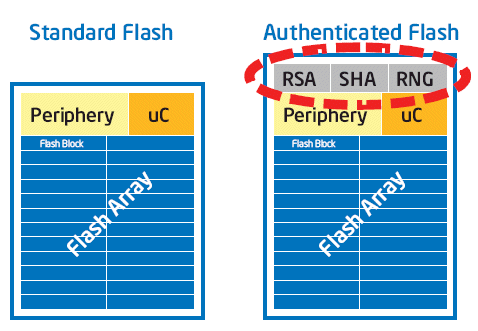
Figure 4
Key Benefits of Authenticated Flash
Intel Authenticated Flash offers a series of benefits to carriers, OEMs and end users. They include:
- Intel Authenticated Flash provides integrated, hardware memory protection, based on the commonly available protocols RSA and HMAC signature verify. With the memory protection feature of the Authenticated Flash, the flash can independently prevent unwanted or unintentional modifications to the flash memory contents. This capability effectively guarantees the integrity of the contents of the flash memory.
- By utilizing the integrated memory authentication, Intel Authenticated Flash provides a significant improvement over the typical approach of measurement/attestation and run-time integrity checking. There are two issues with the typical approach. The first is that an active run-time integrity checking or measurement process costs processor time and battery power. The second is that measurement can only confirm the integrity at an instant of time. The integrity between measurement points is actually unknown.
- Another key benefit of Intel Authenticated Flash is the flexibility and SoC cost savings the technology can drive. With Intel Authenticated Flash the amount of secure SoC resources can be reduced because the integrity of the contents in the external authenticated flash can be guaranteed. Looking at the system boot code, as an example, the system designer can save cost while gaining flexibility by utilizing Intel Authenticated Flash. SoC cost savings can be realized by reducing the SoC boot code and utilizing a secondary boot loader protected by the Intel Authenticated Flash. Flexibility is achieved by moving the majority of the system boot code from the SoC ROM to the external Intel Authenticated Flash. The system boot code has been moved from a memory technology that is expensive and difficult to update, to a memory technology that is cheap and simple to update and can enforce integrity. In a similar fashion, the Intel Authenticated flash can also save on SoC RAM and SoC key storage.
- The Intel Authenticated Flash memory can also extend the benefit of integrity protection to the entire system. Most systems only protect the integrity of specific secure applications. This typically leaves the operating system unprotected. The reason for this choice is that operating systems are not secure and typically contain security holes. With Intel Authenticated Flash, the integrity of the system can be extended to all system code, including the operating system. Intel Authenticated Flash can provide this protection because the flash memory independently authenticates requests from the host system. Even if the operating system were compromised, it would not be able to correctly generate a signed request to the Intel Authenticated Flash memory.
In summary, the key benefits for Intel Authenticated Flash memory are integrity protection for the flash memory contents, independent of the host system. The Intel Authenticated Flash memory can help reduce system cost and improve system flexibility. Intel Authenticated Flash memory also addresses issues related to removing flash memory in addition to the integrity protection outlined above. For systems that have security built into the hardware or SoC, Intel Authenticated Flash memory can improve the overall security of the system, reduce implementation costs and improve flexibility. For systems without security built into the hardware or SoC, Intel Authenticated Flash Memory can provide a basis to add security is a simple, cost effective and flexible fashion.
Authenticated Flash Operations
Intel Authenticated Flash memory operates by authenticating command requests to the flash memory. The system designer can specify authenticated and legacy ranges. Each authenticated range will have a public RSA key installed and associated with the range. Once the authenticated range is specified and an RSA key associated, all operations to that range will require a signature to be presented to the flash memory. The flash memory will independently validate the signature presented with the command. If the signature is correct, the command proceeds. If the signature is incorrect, the operation is terminated and not allowed to proceed. (Figure 5)
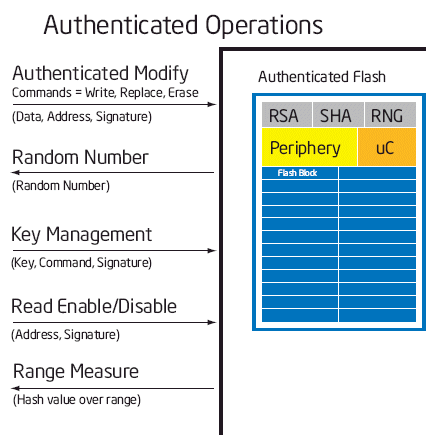
Figure 5
Command descriptions:
-
Authentication range - the authentication range command is used to configure the start address and stop address of individual authentication ranges. The authentication range command is an authenticated command.
-
Key management - the key management commands are used to install keys and associate keys to specific authentication ranges. Key management commands are authenticated.
-
Authenticated write - the authenticated write command takes program data, program address and a signature as parameters. If the signature is correct, the flash is programmed with the program data.
-
Authenticated erase - the authenticated erase command takes the erase address and a signature as parameters. If the signature is correct, the flash block is erased.
-
Authenticated replace - the authenticated replace command takes program data, program address and a signature as parameters. If the signature is correct, the flash location is updated with the new data.
-
Authenticated read - the authenticated read command is used to open or close flash ranges. A flash range can be configured for read disable (closed) or read enable (open). In the read disable state the contents of the flash memory are not available to be read by the host processor. Only with the flash range is configured for read enable can the memory contents be read by the host processor. Read authentication is a method for controlling read access to flash memory contents. The authenticated read command is used to toggle the state of the read state from enable to disable and back.
-
Authenticated measure - the authenticated measure command takes a start address and end address as parameters. The authenticated measure command will provide SHA calculations across the specified range.
The Intel Authenticated Flash memory is extremely flexible and configurable. The system designer can specify: the number of authentication ranges, the key associated with each range, the key hierarchy, and the authenticated commands allowed for each authentication range. Memory ranges not configured for authentication default to legacy mode.
The initial configuration for Intel Authenticated Flash is authentication disabled, an empty key list and an empty range list. With the authentication disabled, keys can be installed into the flash memory, authentication ranges can be specified and keys can be associated with authentication ranges. The flash memory can be freely programmed and erased. Only once the flash authentication is enabled will the specified flash protection(s) be enforced.
Authenticated Flash Signature Options
The Intel Authenticated Flash supports RSA and HMAC based signature options. The signature option choice is based on the availability of a local secure signature generation capability and the level of protection required. With the HMAC signature option, a key value is shared between the SoC and the authenticated flash. With the RSA signature option, RSA public key is installed into the flash memory. The RSA private key can be available locally or be maintained external to the specific device. (Figure 6)
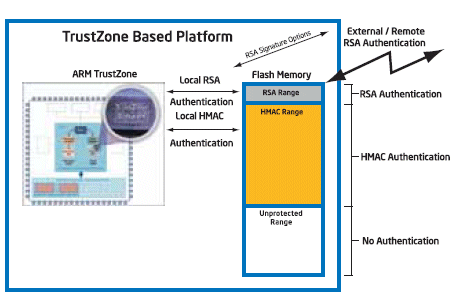
Figure 6
-
If the SoC has the ability to generate signatures in a secure fashion (such as a signature generation application within an ARM TrustZone) then Intel recommends using the HMAC signature protocol with a single protection range. This is because the HMAC signature performance is better than RSA and a single range simplifies configuration. This configuration relies on the security of the local signing authority.
-
If the SoC does not have local signature capability then Intel recommends using the RSA signature protocol with a multiple protection ranges, as required. This configuration allows an external authority to generate signatures that are independently authenticated by the flash memory. In this configuration, system critical code can be controlled by the external authority. Without a local copy of the RSA private key, it is unlikely that a correct signature can be generated.
-
A combination of the key options can also be used to increase the level of security for the system. In this configuration, flash contents that must be strictly controlled (such as SIMLock, IMEI numbers or boot code) can be protected with the RSA protocol. While the remaining flash contents can be protected with the HMAC protocol. In this example, even if the system is compromised, the data protected with an RSA key cannot be modified because the RSA private key is not available locally. The remaining flash contents protected by the HMAC protocol are as secure as the local signing authority.
Designing with Authenticated Flash
Several system architecture questions must be answered to fully leverage the capabilities of the Intel Authenticated Flash memory. The primary question to consider is the trade-off between what to place in the SoC and what to place in the authenticated memory. The availability of authenticated memory expands the options and flexibility available to the system designer.
-
The SoC resources can be reduced due to the availability of authenticated memory. This results in cost savings while providing an equivalent level of protection.
-
SoC ROM can be reduced by leveraging the integrity protection of authenticated memory to provide equivalent protection for ROM'd code and critical data parameters. Code that would typically reside in SoC ROM can be moved to the authenticated flash. In addition, protected code can be directly executed from the flash memory.
-
SoC RAM can also be reduced by leveraging the integrity protection and direct execution capability of authenticated memory. Applications that reside in external flash, but are integrity checked before being loaded into SoC RAM to securely execute, can instead remain in external authenticated flash and be directly executed. With this alternative, the code does not need to be loaded into the secure RAM to execute, thereby reducing the amount of secure RAM needed. The code is protected by the authenticated flash and executed from authenticated flash. The need for secure RAM is then limited to the needs such as stack, heap and dynamic data.
-
Key fuses can also be reduced, saving on SoC cost. Only a single key is required to be stored on the SoC. This key can be used to bind the flash to the host processor. All other keys needed by the system can be safely protected by the authenticated memory.
Once the SoC trade-offs have been considered, then the system designer must consider the configurability of the authenticated flash memory. The number of keys, protection ranges, read protection, write protection, and signature options must be defined. The specific configuration will be driven by the needs of the specific platform.
Intel Authenticated Flash with ARM TrustZone
ARM TrustZone has been designed to address platform security needs independent of the flash technology selected. Likewise, Intel Authenticated Flash has also been designed to address platform security needs independent of the platform security approach. However, the two technologies are complementary. When combined, they provide a solution that is stronger than either technology can provide independently and the combination of technologies can help reduce SOC cost. While there are many variations for integrating the two complementary technologies, in practice integration is simple and straightforward and some of the main design variables were introduced here.
While the ARM TrustZone and Intel Authenticated Flash are commercialized independently, the goal of this white paper was to highlight some of the main benefits in coupling these two technologies. In addition, this white paper offers certain design aspects that would need to be taken into consideration to couple the two technologies. Aspects of this coupling process include security, flexibility and processing requirements for volatile and non-volatile memories on-chip and off-chip. Finally, this white paper describes how the Intel Authenticated Flash could be molded to address your requirements.
The ARM TrustZone architecture extensions were first introduced in the ARM1176JZ-S processor and are present in all subsequent applications CPU from ARM. The TrustZone framework can also be extended for ARM7 and ARM9 processors through a combination of custom hardware and a customized TrustZone Software. Intel Authenticated Memory can also be used in such platforms and is an effective solution to adding hardware integrity protection in such platforms.
In summary, the combination of technologies can result in reduced SoC cost by: reducing the complexity of custom hardware security outside the CPU; reducing SoC ROM, SoC RAM, and SoC key storage; increasing flexibility by reducing the amount of information in SoC ROM; expanding security protection to the operating system; peripherals and platform code; and, improving performance by adding the TrustZone capabilities. Performance benefits are also achieved by eliminating or reducing the need or frequency of run-time integrity checking by leveraging the integrity protection capabilities of Intel Authenticated Flash memory.
Related Semiconductor IP
- HBM4 PHY IP
- Ultra-Low-Power LPDDR3/LPDDR2/DDR3L Combo Subsystem
- HBM4 Controller IP
- IPSEC AES-256-GCM (Standalone IPsec)
- Parameterizable compact BCH codec
Related Articles
- A comprehensive approach to enhancing IoT Security with Artificial Intelligence
- Using ARM Processor-based Flash MCUs as a Platform for Custom Systems-on-Chip
- Introducing ARM Cortex-M23 and Cortex-M33 Processors with TrustZone for ARMv8-M
- Expanding the Horizon of System Monitoring with the Arm SMCF
Latest Articles
- Pipeline Stage Resolved Timing Characterization of FPGA and ASIC Implementations of a RISC V Processor
- Lyra: A Hardware-Accelerated RISC-V Verification Framework with Generative Model-Based Processor Fuzzing
- Leveraging FPGAs for Homomorphic Matrix-Vector Multiplication in Oblivious Message Retrieval
- Extending and Accelerating Inner Product Masking with Fault Detection via Instruction Set Extension
- ioPUF+: A PUF Based on I/O Pull-Up/Down Resistors for Secret Key Generation in IoT Nodes