crypto IP
Filter
Compare
381
IP
from
63
vendors
(1
-
10)
-
Crypto Box Toolset Secure Accelerator
- The High-Performance Hybrid Crypto Box IP core delivers maximum cryptographic throughput by combining classical asymmetric (RSA, ECC), symmetric (AES), and hashing (SHA-2/HMAC) engines with a dedicated post-quantum accelerator supporting ML-KEM (Kyber) and ML-DSA (Dilithium).
- Designed for performance-critical systems without tight area or power limitations, this IP enables ultra-fast key exchange, digital signatures, and secure data processing.
-
Crypto Box Toolset Secure Accelerator
- The Hybrid Crypto Box IP core is a comprehensive, high-efficiency cryptographic solution that combines RSA, ECC, AES, and SHA-2/HMAC with a built-in accelerator for post-quantum algorithms such as ML-KEM (Kyber) and ML-DSA (Dilithium). Designed for embedded systems with balanced resource constraints, it enables secure key exchange, digital signatures, authenticated encryption, and hashing, future-proofed for the quantum era.
-
Crypto Box Toolset Secure Accelerator
- The Crypto Box IP core is a high-efficiency cryptographic solution that combines RSA, ECC, AES, and a SHA-2/HMAC engine, all with advanced protections against side-channel and fault injection attacks.
- Designed for devices with balanced budgets for performance, area, and power, it enables secure key exchange, digital signatures, data encryption, and message authentication in a unified, compact architecture.
-
Crypto Box Toolset Secure Accelerator
- The Crypto Box IP core is a compact, power-efficient cryptographic engine that combines essential asymmetric algorithms (RSA, ECC) with high-speed AES encryption in a single integrated block.
- Designed for resource-constrained embedded systems, it enables secure key exchange, digital signatures, and fast data encryption with minimal area and power overhead.The
-
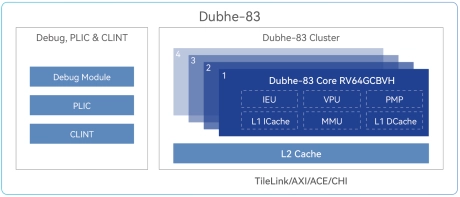
CPU IP Following the RVA23 Profile, supporting RVV1.0 and all extensions of Vector Crypto
- Dubhe-83 CPU IP features a 10+ stage pipeline, 3-issue, and out-of-order pipeline, follows the RVA23 Profile, supports RV64GCBVH, supports RVV1.0 and supports all extensions of Vector Crypto.
- With a score of 8.5 SPECInt2006/GHz, Dubhe-83 targets applications that require highly energy-efficient computation, including mobile, desktop, AI, and automotive.
-
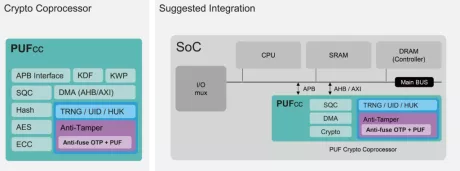
Digital PUF IP
- Generate unclonable 128 or 256-bit seeds with a compact, logic-based PUF that drops into any SoC.
- Digital PUF IP adds true hardware identity for secure boot, key generation, and device authentication with minimal silicon overhead.
-
NIST’s ASCON Lightweight Crypto Algorithm Accelerator
- The ASCON-IP-41 is an efficient implementation of NIST’s lightweight crypto algorithm family ASCON. ASCON is a single algorithm defined in different modes to support AEAD and HASH operations.
- As a multi-purpose algorithm with minimal area requirements ASCON is extremely suitable for low-cost and low-power applications.
-
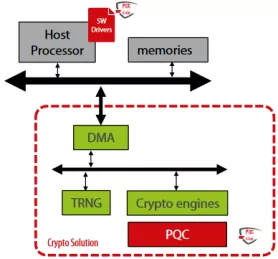
Crypto Coprocessor with integrated Post-Quantum Cryptography IPs
- The Crypto Coprocessors are a hardware IP core platform that accelerates cryptographic operations in System-on-Chip (SoC) environment on FPGA or ASIC.
- Symmetric operations are offloaded very efficiently as it has a built-in scatter/gather DMA. The coprocessors can be used to accelerate/offload IPsec, VPN, TLS/SSL, disk encryption, or any custom application requiring cryptography algorithms.
-
Post Quantum ready Public Key Crypto HW acceleration library optimized for networking applications
- ML-KEM KeyGen, Encaps, Decaps operations for all security modes in FIPS 203;
- ML-DSA Keygen, Sign, Verify operations for all security modes in FIPS 204;
- ECDSA Sign/Verify operations for all NIST prime field curves;
- ECC public key generation for all NIST prime field standardized curves;
- SHA3/SHAKE operations specified in FIPS 202;
-
TLS 1.3 Compliant Crypto Coprocessor
- NIST CAVP certified and OSCCA standard compliant crypto engine suite
- Includes private/public key ciphers, message authentication code, hashes, and key derivation
- Key wrapping function for the secure export of keys
- Public-key coprocessor for digital signatures and key agreements over elliptic/Edward curves