Uniquify IP
Filter
Compare
15
IP
from
5
vendors
(1
-
10)
-
Safety Enhanced GPNPU Processor IP
- A True SDV Solution
- Fully programmable – ideal for long product life cycles
- Scalable multicore solutions up to 864 TOPS
- Solutions for ADAS, IVI and ECU products
-
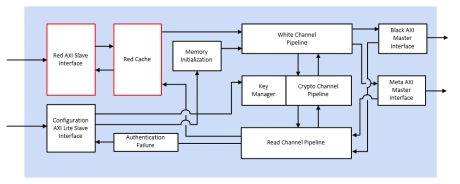
Inline memory encryption engine, for FPGA
- Performs encryption, decryption and/or authentication using AES Counter Mode (CTR) or Galois Counter Mode (GCM)
- Supports AES key sizes 128 or 256
- Internal key management with NIST-compliant key generation
- Encrypt memory space into user-defined vaults, each with a unique key
- Compatible with AMBA AXI4 interface
- Supports hard or soft memory controllers in Xilinx FPGA and SoC devices
- Supports multiprocessor systems
-
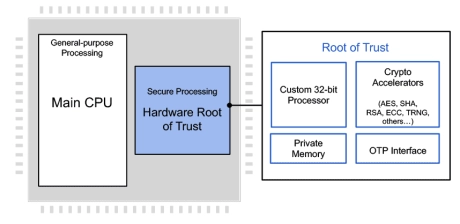
Programmable Root of Trust With DPA and FIA for US Defense
- Custom-designed 32-bit secure RISC-V processor
- Multi-layered security model protects all core components against a wide range of attacks
- Security model includes hierarchical privilege model, secure key management policy, hardware-enforced isolation/access control/protection, error management policy
- State-of-the-art DPA resistance, FIA protection and anti-tamper techniques
-
tRoot V500 Hardware Secure Module
- Complete hardware secure modules with Root of Trust give SoCs a unique, tamper-proof identity
- Enable secure services deployment
- Provide a Trusted Execution Environment to create, provision, store and manage keys
- Full hardware key protection
-
tRoot F120 Hardware Secure Module (w/ARC SEM120)
- Choice of energy-efficient ARC SEM110, SEM120D, EM4 + ESP, or EM5D + ESP processors
- Extensive collection of hardware accelerated cryptography options
- Secure instruction and data memory controllers
- Host and peripheral interfaces (UART, NVM, GPIO, TRNG, Device ID)
-
tRoot F110 Hardware Secure Module (w/ARC SEM110)
- Choice of energy-efficient ARC SEM110, SEM120D, EM4 + ESP, or EM5D + ESP processors
- Extensive collection of hardware accelerated cryptography options
- Secure instruction and data memory controllers
- Host and peripheral interfaces (UART, NVM, GPIO, TRNG, Device ID)
-
tRoot F005 Hardware Secure Module (w/ ARC EMD5D)
- Choice of energy-efficient ARC SEM110, SEM120D, EM4 + ESP, or EM5D + ESP processors
- Extensive collection of hardware accelerated cryptography options
- Secure instruction and data memory controllers
- Host and peripheral interfaces (UART, NVM, GPIO, TRNG, Device ID)
-
tRoot F004 Hardware Secure Module (w/ ARC EM4)
- Choice of energy-efficient ARC SEM110, SEM120D, EM4 + ESP, or EM5D + ESP processors
- Extensive collection of hardware accelerated cryptography options
- Secure instruction and data memory controllers
- Host and peripheral interfaces (UART, NVM, GPIO, TRNG, Device ID)
-
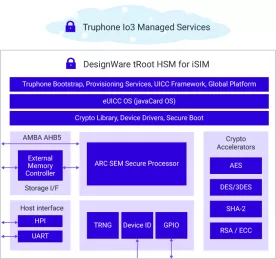
tRoot Hardware Secure Modules for iSIM
- Migrating from discrete SIM cards to an embedded iSIM solution reduces area, power, and cost
- Out-of-the-box connectivity using integrated bootstrap code within the HSM
- Leverages Truphone’s global network by bundling default connectivity profile on each chipset
- Factory-loaded bootstrap profile enables global connectivity, but not locked to Truphone
-
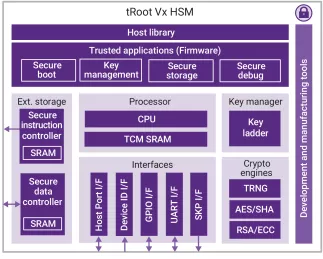
tRoot Vx Hardware Secure Modules
- The Synopsys tRoot Vx HSMs include a highly secure hardware Root of Trust that enables devices to boot securely and permits encryption and decryption of sensitive data allowing it to be stored in non-secure devices or memory. It provides a completely secure environment in a non-secure system from which applications can execute secure cryptographic services.
- The tRoot Vx HSMs secure SoCs by using unique code protection mechanisms that provide run-time tamper detection and response. Code privacy protection is achieved without the added cost of dedicated secure memory. This unique feature reduces system complexity and cost by allowing the tRoot Vx HSM’s firmware to reside in any non-secure memory space.
- Commonly, tRoot Vx programs reside in shared system DDR memory. Due to the confidentiality and integrity provisions of the secure instruction controller, this memory is effectively private to the HSM and impervious to attempts to modify it originating in other subsystems in the chip, or from outside. The tRoot Vx HSM’s ROM-less architecture can support system design changes at any time without risk of exposing the system memory to threats and without additional engineering development cost. To minimize the number of attack vectors, tRoot Vx HSMs use a simple interface with a limited set of interactions with the host processor.