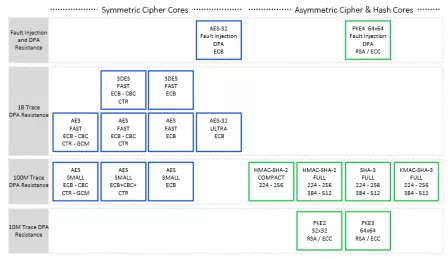
DPA IP
Filter
Compare
52
IP
from
13
vendors
(1
-
10)
-
Advanced DPA- and FIA-Resistant Software Library
- Ultra-strong side-channel and SIFA protection at high performance
- NIST FIPS-197 compliant
- AES-128/192/256 encryption and decryption
- Tunable protection level
-
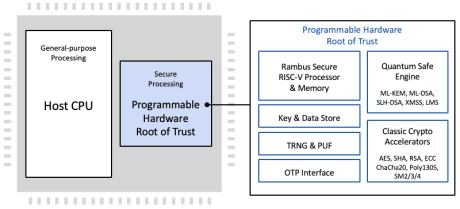
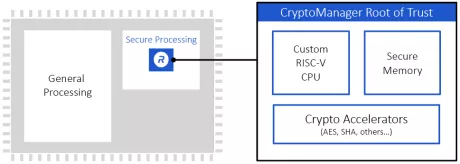
Programmable Root of Trust With DPA and FIA for US Defense
- Custom-designed 32-bit secure RISC-V processor
- Multi-layered security model protects all core components against a wide range of attacks
- Security model includes hierarchical privilege model, secure key management policy, hardware-enforced isolation/access control/protection, error management policy
- State-of-the-art DPA resistance, FIA protection and anti-tamper techniques
-
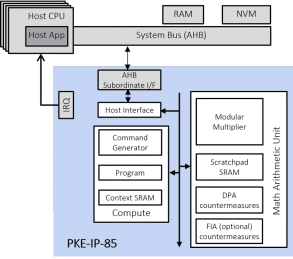
Fast Public Key Engine with DPA or with DPA and FIA
- The SCA-resistant PKE-IP-85 family of Public Key Engine cores provide semiconductor manufacturers with superior public key cryptography acceleration.
- The cores are easily integrated into ASIC/SoC and FPGA devices, offer a high-level of resistance to Differential Power Analysis (DPA), and, optionally, offer detection of Fault Injection Attacks (FIA).
-
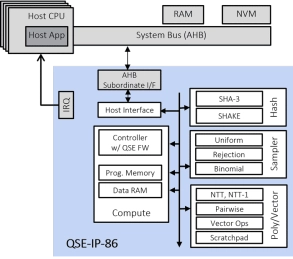
Fast Quantum Safe Engine for ML-KEM (CRYSTALS-Kyber) and ML-DSA (CRYSTALS-Dilithium) with DPA
- Compliant with FIPS 203 ML-KEM and FIPS 204 ML-DSA standards
- Uses CRYSTALS-Kyber, CRYSTALS-Dilithium quantum-resistant algorithms
- Includes SHA-3, SHAKE-128 and SHAKE-256 acceleration
- The embedded QSE CPU combined with Rambus-supplied firmware implements the full FIPS 203/204 protocols
-
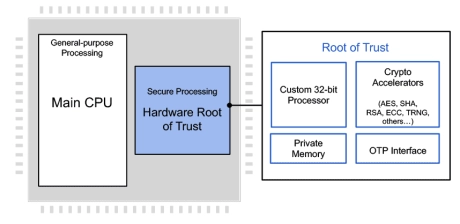
Programmable Root of Trust Family With DPA & Quantum Safe Cryptography
- Hardware Root of Trust employing a custom 32-bit RISC-V processor
- Multi-layered security model provides protection of all components in the core
- NIST CAVP and CMVP compliant for FIPS 140-3 validation
- State-of-the-art anti tamper techniques
- DPA-resistant cryptographic accelerators
- Caliptra Root of Trust for Measurement with DICE and X.509 support
-
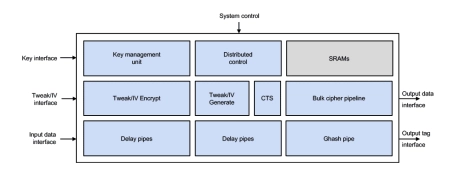
Fast Inline Cipher Engine, AES-XTS/GCM, SM4-XTS/GCM, DPA
- One input word per clock without any backpressure
- Design can switch stream, algorithm, mode, key and/or direction every clock cycle
- GCM: throughput is solely determined by the data width, data alignment and clock frequency
- XTS: block processing rate may be limited by the number of configured tweak encryption & CTS cores; a configuration allowing 1 block/clock is available
-
ChaCha20 DPA Resistant Crypto Accelerator
- Quicken time-to-market using precertified DPA Countermeasures
- Highly secure cryptographic engine primitives
- Extensive validation using the Test Vector Leakage Assessment (TVLA) methodology (revealing no leakage beyond 100 million traces)
- Cores protected against univariate first- and second-order side-channel attacks beyond 1 billion operations
-
AES Authenticated Encryption Accelerator with DPA or with DPA and FIA
- The SCA-resistant AES-IP-3X family of crypto accelerator cores provide semiconductor manufacturers with superior AES cipher acceleration.
- The cores are easily integrated into ASIC/SoC and FPGA devices and offer a high-level of resistance to various Side Channel Attacks like Differential Power Analysis (DPA), and optionally offer detection of Fault Injection Attacks (FIA).
-
DPA Resistant Software Library
- Library implements a very high-security primitives for AES, ECC, RSA, and SHA
- Supported platforms: ARM Cortex-A9, ARM7TDMI, and others
- AES supports 128/192/256-bit encrypt and decrypt
- ECC supports ECDSA/ECDH for NIST prime fields (192/256/384/521)
-
Programmable Root of Trust with Quantum Safe Cryptography acceleration, DPA-resistant & FIA-protected cryptographic accelerators and Caliptra RoTM
- The CryptoManager RT-6xx v3 Root of Trust family from Rambus is the latest generation of fully programmable FIPS 140-3 compliant hardware security cores offering Quantum Safe security by design for data center and other highly secure applications.
- Device and system architects face a growing array of security threats, including the threat of quantum computers. Across applications, one constant is the need for a hardware Root of Trust-based security implementation.