RSA IP
Filter
Compare
66
IP
from
20
vendors
(1
-
10)
-
RSA Signature Verification Accelerator - Compact RSA Signature Verification Accelerator for Constrained Devices
- Compact RSA Signature Verification Accelerator for Constrained Devices
-
RSA Keygen IP Core
- RSA Keygen IP Cores perform key generation in compliance with the RSA Key Pair Generation specifications defined in 'FIPS 186'.
- This standard specifies methods for generating RSA key pairs.
- RSA Keygen IP Cores support key pair generation up to 4096 bits.
-
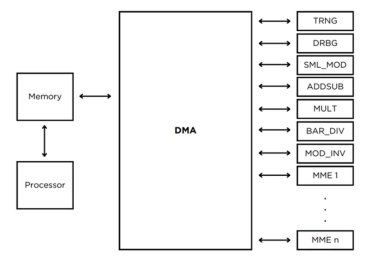
RSA IP Core
- RSA IP Cores perform digital signature generation and verification in compliance with the RSA (Rivest-Shamir-Adleman) Digital Signature Algorithm specifications defined in 'FIPS 186'.
- This standard specifies methods for digital signature generation and verification using the RSA Digital Signature Algorithm.
- RSA IP cores support bit lengths from 256 to 4096.
-
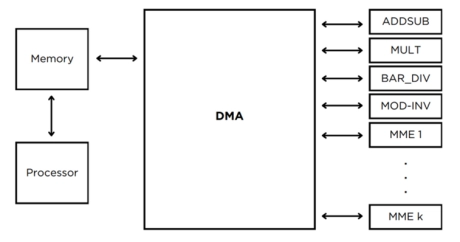
RSA Signature Verification IP Core
- Minimal Resource Requirements: The entire XIP5012C requires less than 280 LUTs (lookup tables) and 2 internal memory blocks (Xilinx® Zynq®-7000).
- Performance: Despite its small size, XIP5012C can support more than 10 digital signature verification operations per second.
- Standard Compliance: XIP5012C is compliant with FIPS 186-4.
-
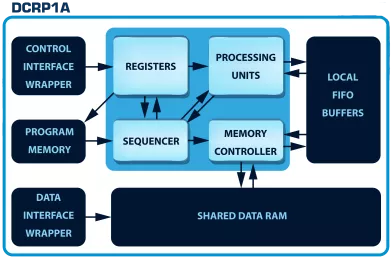
100% Secure Cryptographic System for RSA, Diffie-Hellman and ECC with AMBA AHB, AXI4 and APB
- The DCRP1A - CryptOne IP is a 100% secure cryptographic system
- CryptOne is a fully scalable, hardware-accelerated cryptographic system
- Designed for next-generation SoCs, FPGAs, and secure embedded systems, it delivers 100% secure asymmetric cryptography acceleration for demanding applications.
-
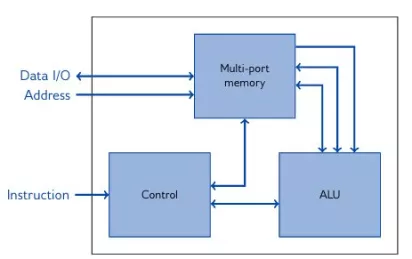
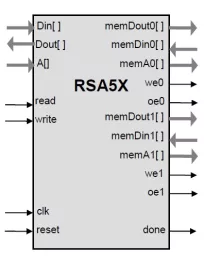
Scalable RSA and Elliptic Curve Accelerator
- The core implements the exponentiation operation of the RSA cryptography Q = Pk.
- The operands for the exponentiation: k and P as well as the modulus are programmed into the memory and the calculation is started.
- Once the operation is complete, the result Q can be read through the interface.
-
RSA public key cryptography with APB interface
- For a typical 1024-bit keysize the modular exponentiation can be performed 25 times faster than a pure software implementation. A 1024-bit message can be encrypted (public key of 65537) in 50,000 clock cycles and decrypted in 3,600,000 clock cycles. The peripheral can also be used with software support for CRT based decryption and for generating keys. Using CRT can reduce the cycle count by 1/4.
- The core is very small; when targeting TSMC90LP at 200MHz it comprises only 17k gates for the logic and an equivalent 32k gates including all memories.
-
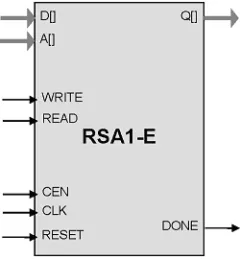
RSA Public Key Exponentiation Accelerator
- Small size: RSA1-E starts from less than 10K ASIC gates (intermediate result storage memory required; size depends on the core configuration)
- Implements the computationally demanding parts of RSA public key cryptography for long life battery powered applications
- Support for RSA binary fields of configurable bit sizes up to 2048
- Microprocessor-friendly interface
-
RSA Public Key Cryptography Exponentiation Accelerator
- Low footprint
- High throughput
- 2048-bit length inputs
- Short exponent lengths