cryptography accelerator IP
Filter
Compare
47
IP
from
16
vendors
(1
-
10)
-
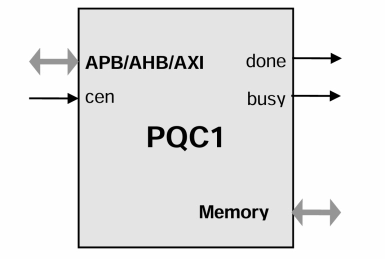
APB Post-Quantum Cryptography Accelerator IP Core
- Implements ML-KEM and ML-DSA post-quantum cryptography digital signature standards. The system interface is an microprocessor slave bus (APB, AHB, AXI options are available).
- The design is fully synchronous and requires only minimal CPU intervention due to internal microprogramming sequencer.
-
High-Speed Elliptic Curve Cryptography Accelerator for ECDH and ECDSA
- Fully digital design
- Portable to any ASIC or FPGA technology
- Fully standard compliant
- Easy to integrate
-
RSA Public Key Cryptography Exponentiation Accelerator
- Low footprint
- High throughput
- 2048-bit length inputs
- Short exponent lengths
-
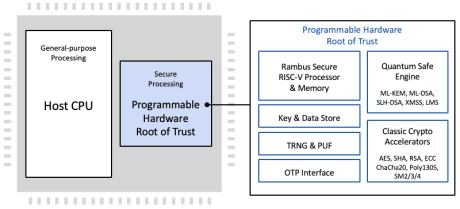
Programmable Root of Trust with Quantum Safe Cryptography acceleration, DPA-resistant & FIA-protected cryptographic accelerators and Caliptra RoTM
- The CryptoManager RT-6xx v3 Root of Trust family from Rambus is the latest generation of fully programmable FIPS 140-3 compliant hardware security cores offering Quantum Safe security by design for data center and other highly secure applications.
- Device and system architects face a growing array of security threats, including the threat of quantum computers. Across applications, one constant is the need for a hardware Root of Trust-based security implementation.
-
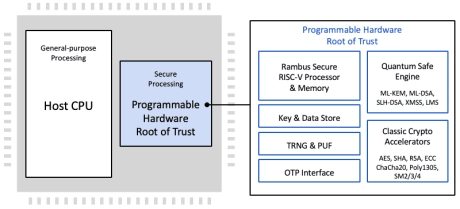
Programmable Root of Trust with Quantum Safe Cryptography acceleration and DPA-resistant & FIA-protected cryptographic accelerators
- The CryptoManager RT-6xx v3 Root of Trust family from Rambus is the latest generation of fully programmable FIPS 140-3 compliant hardware security cores offering Quantum Safe security by design for data center and other highly secure applications.
- Device and system architects face a growing array of security threats, including the threat of quantum computers. Across applications, one constant is the need for a hardware Root of Trust-based security implementation.
-
ECC Secure Accelerator - High-performance ECC IP with advanced physical security
High-performance ECC IP with advanced physical security
-
ECC Secure Accelerator - Compact and Secure ECC IP Core for Resource-Constrained Devices
- Compact and Secure ECC IP Core for Resource-Constrained Devices
-
Crypto Box Toolset Secure Accelerator
- The Hybrid Crypto Box IP core is a comprehensive, high-efficiency cryptographic solution that combines RSA, ECC, AES, and SHA-2/HMAC with a built-in accelerator for post-quantum algorithms such as ML-KEM (Kyber) and ML-DSA (Dilithium). Designed for embedded systems with balanced resource constraints, it enables secure key exchange, digital signatures, authenticated encryption, and hashing, future-proofed for the quantum era.
-
Post-Quantum Accelerator
- The Post-Quantum Cryptography IP core provides a high-efficiency hardware solution supporting ML-KEM (Kyber) and ML-DSA (Dilithium) as standardized in FIPS 203 and 204, along with additional hash-based signature schemes including SPHINCS+, XMSS, and LMS.