Root of Trust Engine IP
Filter
Compare
14
IP
from
8
vendors
(1
-
10)
-
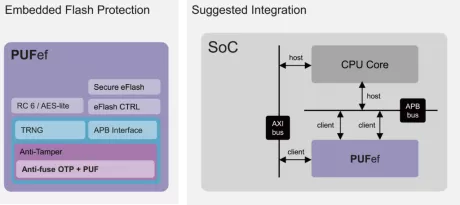
Embedded Flash Protection with Hardware Root of Trust and Lite Crypto Engine
- PUFef is designed to protect embedded Flash with a Hardware Root of Trust and a lite crypto engine of RC6.
- The RC6 provides a comprehensive level of security while also minimizing overall size.
- Before attempting to hack the crypto engine, attackers would first have to destroy the embedded Flash.
-
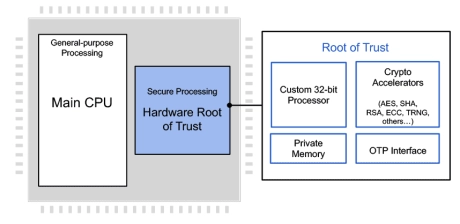
Programmable Root of Trust With DPA and FIA for US Defense
- Custom-designed 32-bit secure RISC-V processor
- Multi-layered security model protects all core components against a wide range of attacks
- Security model includes hierarchical privilege model, secure key management policy, hardware-enforced isolation/access control/protection, error management policy
- State-of-the-art DPA resistance, FIA protection and anti-tamper techniques
-
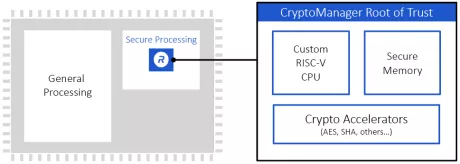
Programmable Root of Trust Family With DPA & Quantum Safe Cryptography
- Hardware Root of Trust employing a custom 32-bit RISC-V processor
- Multi-layered security model provides protection of all components in the core
- NIST CAVP and CMVP compliant for FIPS 140-3 validation
- State-of-the-art anti tamper techniques
- DPA-resistant cryptographic accelerators
- Caliptra Root of Trust for Measurement with DICE and X.509 support
-
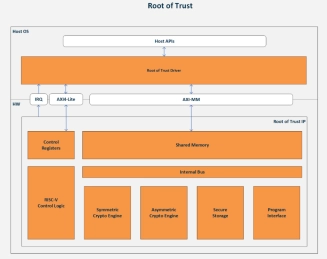
Root of Trust
- Root of Trust IP is a Hardware Secure Module (HSM) solution that provides the security foundation for processors and System on Chips (SoCs).
- It protects critical systems especially devices used in automotive, industrial, cloud, data center, and wireless applications.
-
Via-PUF Security Chip for Root of Trust
-
The vPUF® IP, powered by Via PUF (Physically Unclonable Function) technology, provides a unique silicon fingerprint for inborn identity function, essential for the Root of Trust in security applications
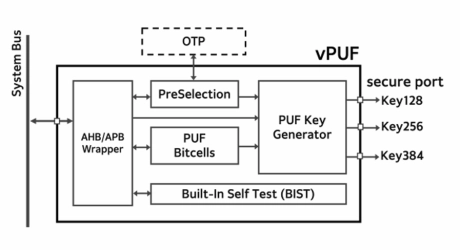
-
-
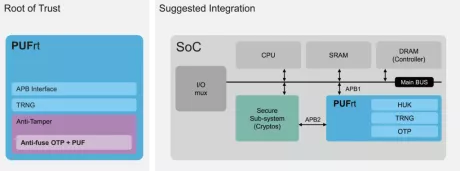
Hardware Root of Trust IP
- Built-in standard APB controller with privilege control to create secure/non-secure separation. Additionally, interface customization is available for different design requirements.
- Four 256-bit hardware PUF chip fingerprints, include a self-health check that can be used as a unique identification(UID) or a root key(seed).
- High-quality true random number generator (TRNG)
- 8k-bit mass production OTP with built-in instant hardware encryption (customization available)
-
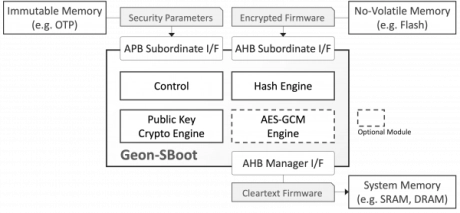
GEON™ Secure Boot Hardware Engine
- GEON-SBoot is an area-efficient, processor-agnostic hardware engine that protects SoC designs from booting with malicious or otherwise insecure code.
- The security platform employs public-key cryptography (which stores no secret on-chip) to ensure that only unmodified firmware from a trusted source is used by the system.
-
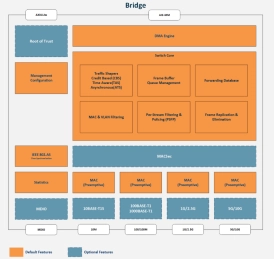
Bridge
- A complete integrated hardware and software solution that includes a TSN-capable Ethernet switch, a DMA engine, an IEEE 802.1 AS Time Synchronization system, and a Root of Trust security module.
-
Zonal Controller
- Complete solution that integrates both hardware and software components including a TSN-capable Ethernet switch, a Root of Trust security module, and a transport protocol encapsulation system based on IEEE 1722
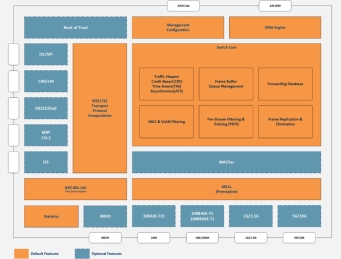
-
Secure RoT Core for Data Centers
- Efficient Performance
- SCA/FIA Protections
- Flexible Interfaces
- Security Certification Readiness