secure execution processor IP
Filter
Compare
34
IP
from
10
vendors
(1
-
10)
-
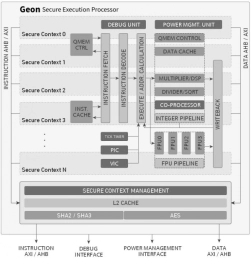
Secure Execution Processor
- The Geon™ Secure Execution Processor is a low-power, 32-bit processor IP core with built-in protection of sensitive code and data.
- It uses two or more cryptographically separated execution contexts for a high degree of security during code execution and for data storage and transfer to and from the processor.
-
Secure Execution Processor
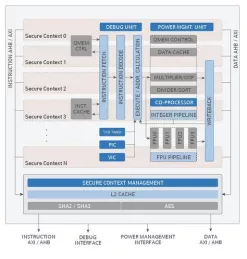
- Two cryptographically isolated secure execution contexts
- Cryptographic primitives agnostic
- Lowest overhead implementation with single Keccak (SHA3) core
-
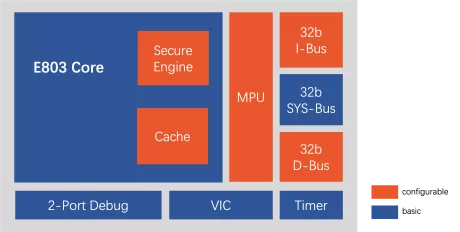
Low power 32-bit processor with secure execution capability
- Instruction set: T-Head ISA (32-bit/16-bit variable-length instruction set);
- Pipeline: 3-stage;
- General register: 16 32-bit GPRs;
- Bus interface: Tri-bus (instruction bus + data bus + system bus) ;
-
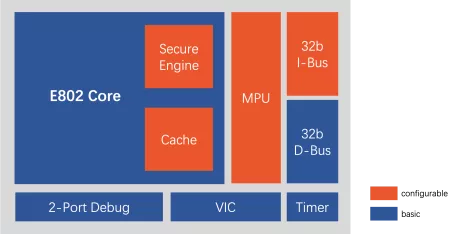
Ultra-low power 32-bit processor with secure execution capability
- Instruction set: T-Head ISA (32-bit/16-bit variable-length instruction set);
- Pipeline: 2-stage;
- General register: 16 32-bit GPRs;
- Bus interface: Dual bus (instruction bus + data bus);
-
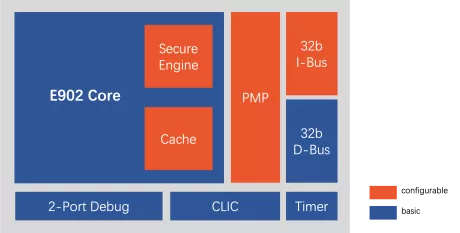
Ultra-low power processor with RISC-V architecture possessing secure execution capability
- Instruction set: T-Head ISA (compatible with RV32EMC/RV32EC/RV32IMC);
- Pipeline: 2-stage;
- Permission mode: Optional M state or M+U state;
- General register: 16 32-bit GPRs;
-
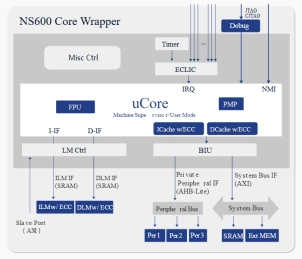
32-Bit Security processor
- Nuclei Security processor is a series of chips designed specifically for security application scenarios, including NS100, NS300, and NS600 products.
-
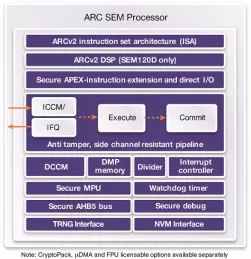
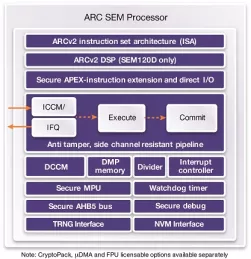
ARC SEM120D Security Processor with DSP for Low Power Embedded Applications
- Performance-, power- and area-efficient security processors for embedded applications
- Secure privilege mode orthogonal to kernel/user mode
- Enhanced secure MPU with context ID for secure or normal operation
- Up to 16 configurable protected regions and per region scrambling capability
-
ARC SEM110 Security Processor for Low Power Embedded Applications
- Performance-, power- and area-efficient security processors for embedded applications
- Secure privilege mode orthogonal to kernel/user mode
- Enhanced secure MPU with context ID for secure or normal operation
- Up to 16 configurable protected regions and per region scrambling capability
-
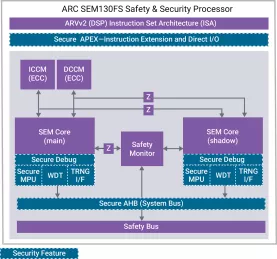
ARC SEM130FS Safety and Security Processor
- ASIL D compliant dual-core, lockstep safety processor supports ISO 26262 automotive safety standards and provides advanced security to protect against evolving threats
- Secure privilege mode orthogonal to kernel/user mode
- Integrated self-checking safety monitor capable of time diversity
- Uniform instruction timing and timing/ power randomization for side channel resistance
-
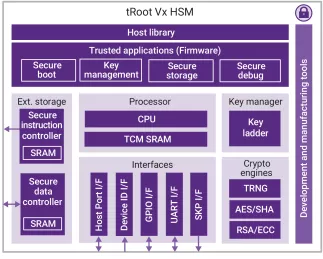
tRoot V500 Hardware Secure Module
- Complete hardware secure modules with Root of Trust give SoCs a unique, tamper-proof identity
- Enable secure services deployment
- Provide a Trusted Execution Environment to create, provision, store and manage keys
- Full hardware key protection