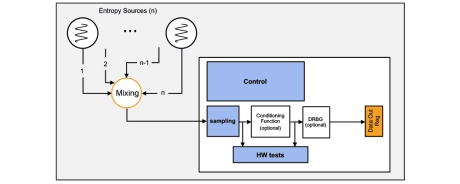
TRNG IP
Filter
Compare
57
IP
from
14
vendors
(1
-
10)
-
-
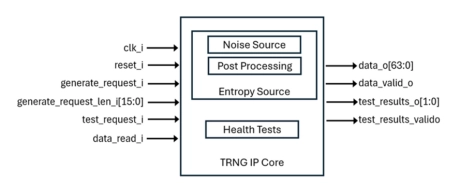
True Random Number Generator (TRNG) IP
- The TRNG IP delivers NIST- and BSI-compliant entropy for secure embedded and SoC designs.
- With robust health testing and digital or analog implementation options, our TRNGs provide the foundation for trusted key generation, encryption, and authentication in mission-critical applications.
-
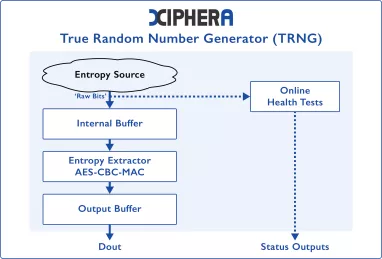
-
True Random Number Generator (TRNG)
- Fully Digital and based on standard cells
- Compliant with: AIS-31 (PTG.1 to PTG.3), NIST FIPS 140-3, NIST SP 800-90, GM/T 0005-2015
- Robust against process, temperature and voltage variations
- Post-silicon fine tuning to ensure high-level functional safety
-
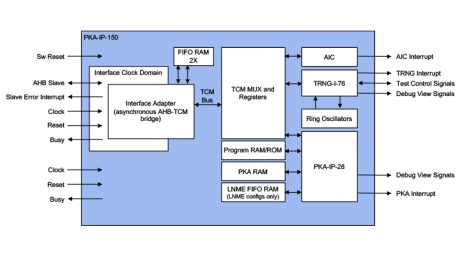
RSA/ECC Public Key Accelerators with TRNG and AHB
- Up to 4160-bit modulus size for RSA & 768-bit modulus for prime field ECC operations
- Public key signature generation, verification and key negotiation with little involvement of host
- NIST CAVP compliant for FIPS 140-3
-
RSA/ECC Public Key Accelerator Farm with TRNG and AHB
- High-performance accelerator for Public Key operations, up to 4160-bit modulus size for modular exponentiations and 768-bit modulus for ECC operations
- Performs high-level key negotiate & sign/verify operations
- Synthesizable over 550 MHz in 40nm technologies and over 650 MHz in 28nm technologies
- Up to sixteen independent command/result queues
-
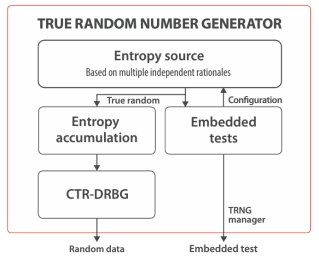
TRNG fully compliant with NIST 800-22
- ASIC or FPGA target
- Generates 256 random bits at a time
- Multiple ring oscillators with post processing for true random bit generation
- Fully compliant with latest NIST 800-22 800-22 and Diehard Random test suite
-
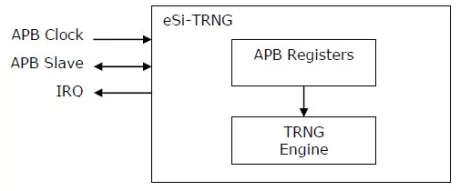
Fast NIST ESV certified, FIPS (SP800-90A/B/C) True Random Number Generator
- The TRNG-IP-77 is a FIPS-compliant and certified IP core for True Random Number Generation (TRNG) with an optional post-processor and several internal self-tests.
- Designed for easy integration into ASICs and SOCs, the 100% digital standard cell based TRNG-IP-77 provides a reliable and cost-effective embedded IP solution for our customer’s SoCs.
-
NIST ESV certified, AIS-31, FIPS (SP800-90A/B/C) True Random Number Generator
- Non-deterministic Random Number Generator, FIPS-140 SP800-90A/B compliant, ESV certified for NRBGs and DRBGs (#E167).
- High performance, low power, fully digital, standard cell only, supports all CMOS nodes.
- Available as standalone RBG or embedded in the Rambus RT-130, RT-630, RT-660 Root of Trusts