Rambus IP
Filter
Compare
114
IP
from
2
vendors
(1
-
10)
-
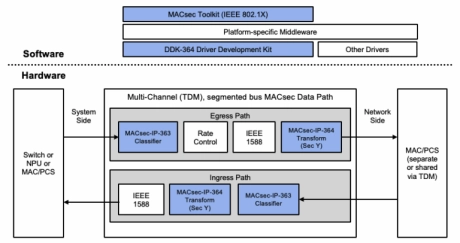
1.6T/3.2T Multi-Channel MACsec Engine with TDM Interface (MACsec-IP-364)
- The MACsec-IP-364 is a MACsec/IPsec engine developed specifically for high-speed, multi-rate and multi-port Ethernet devices.
- Its architecture provides an optimal multi-protocol solution for aggregate throughput for 1.6T and 3.2T.
- The MACsec-IP-364 is ideal for deployment in data center, enterprise and carrier network applications, as well as network-attached high-performance computing.
-
Quantum Safe, ISO 21434 Automotive-grade Programmable Hardware Security Module
- The automotive-grade CryptoManager RT-7xx v3 Root of Trust family is the next generation of fully programmable ISO 26262 and ISO 21434 compliant hardware security modules offering Quantum Safe security by design for secure automotive applications.
- The CryptoManager RT-7xx family protects against a wide range of hardware and software attacks through state-of-the-art side channel attack countermeasures and anti-tamper and security techniques.
-
Embedded Hardware Security Module (Root of Trust) - Automotive Grade ISO 26262 ASIL-B
- The RT-64x Embedded Hardware Security Module (Root of Trust) family are fully programmable, ISO 26262 ASIL-B hardware security cores offering security by design for automotive applications.
- They protect against a wide range of failures such as permanent, transient and latent faults and hardware and software attacks with state-of-the-art anti-tamper and security techniques.
-
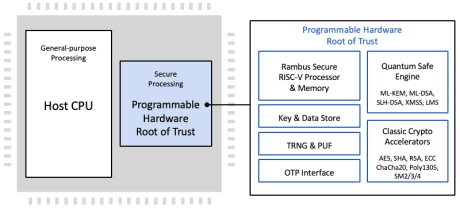
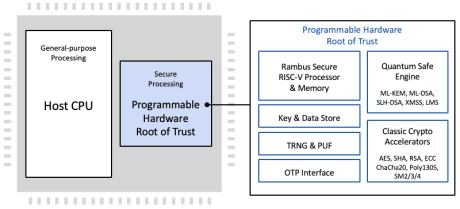
Programmable Root of Trust with Quantum Safe Cryptography acceleration, DPA-resistant & FIA-protected cryptographic accelerators and Caliptra RoTM
- The CryptoManager RT-6xx v3 Root of Trust family from Rambus is the latest generation of fully programmable FIPS 140-3 compliant hardware security cores offering Quantum Safe security by design for data center and other highly secure applications.
- Device and system architects face a growing array of security threats, including the threat of quantum computers. Across applications, one constant is the need for a hardware Root of Trust-based security implementation.
-
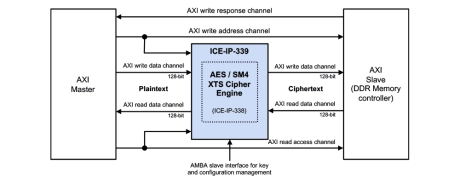
Inline cipher engine with AXI, for memory encryption
- Throughput: 128 bit (16 Byte) wide encryption/decryption per cycle
- Throughput: 1 tweak computation per 4 clock cycles
- Bidirectional design including arbitration between read and write requests
- Zero clock overhead for switching between encryption (write) and decryption (read)
- 30-40 cycle data channel latency
-
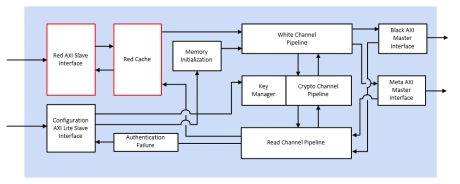
Inline memory encryption engine, for FPGA
- Performs encryption, decryption and/or authentication using AES Counter Mode (CTR) or Galois Counter Mode (GCM)
- Supports AES key sizes 128 or 256
- Internal key management with NIST-compliant key generation
- Encrypt memory space into user-defined vaults, each with a unique key
- Compatible with AMBA AXI4 interface
- Supports hard or soft memory controllers in Xilinx FPGA and SoC devices
- Supports multiprocessor systems
-
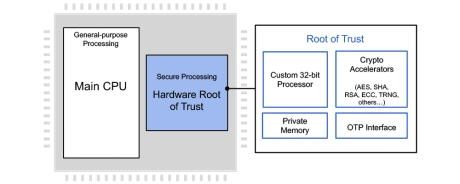
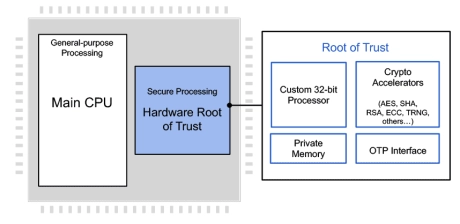
Programmable Root of Trust With DPA and FIA for US Defense
- Custom-designed 32-bit secure RISC-V processor
- Multi-layered security model protects all core components against a wide range of attacks
- Security model includes hierarchical privilege model, secure key management policy, hardware-enforced isolation/access control/protection, error management policy
- State-of-the-art DPA resistance, FIA protection and anti-tamper techniques
-
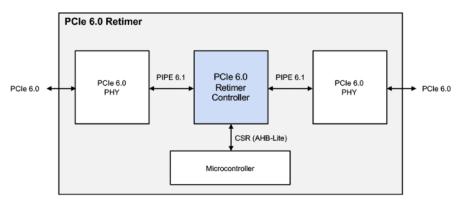
PCIe 6.0 Retimer Controller with CXL Support
- Designed to the latest PCI Express 6.0 (64 GT/s), and capable of supporting 32.0, 16.0, 8.0, 5.0 and 2.5 GT/s link rates
- Supports x1, x2, x4, x8 and x16 link widths
- CXL aware and supports sync header bypass
- Supports PIPE 5.2/6.1 compatible PHYs
- Optimized data-path for low latency insertion
-
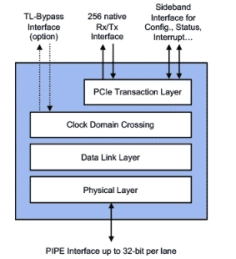
PCIe 3.1 Controller
- Dynamically adjustable application layer frequency down to 8Mhz for increased power savings
- Optional MSI/MSI-X register remapping to memory for reduced gate count when SR-IOV is implemented
- Configurable pipelining enables full speed operation on Intel and Xilinx FPGA, full support for production FPGA designs up to Gen3 x16 with same RTL code
- Ultra-low Transmit and Receive latency (excl. PHY)
- Smart buffer management on receive side (Rx Stream) and transmit side (merged Replay/Transmit buffer) enables lower memory footprint
-
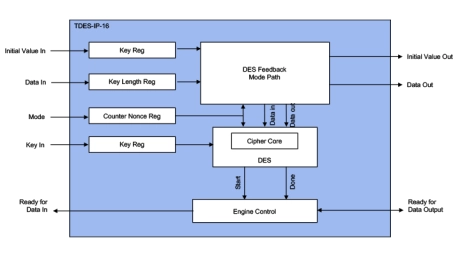
3DES ECB/CBC Accelerators
- The 3DES-IP-16 (EIP-16) is IP for accelerating the AES symmetric cipher algorithm (FIPS-46/81 – SP800-IP-20), supporting single Des and triple DES in ECB, CBC, CFB and OFB modes up to 4 Gbps @ 800MHz.
- Designed for fast integration, low gate count and full transforms, the 3DES-IP-16 accelerator provides a reliable and cost-effective embedded IP solution that is easy to integrate into high speed crypto pipelines.