DPA Resistant AES Core
Overview
The DPA Resistant AES solution implements the AES algorithm with built-in robust, flexible side-channel resistance validated and optimized for different performance and security levels.
Key Features
- Core implements a very high-security AES primitive
- Available as AES-128 and AES-256 encrypt and decrypt
- Simple control/status interface
- Implements DPA countermeasures such as LMDPL (LUT-Masked Dual-rail with Pre-charge Logic) gate-level masking and other schemes
- No routing constraints necessary for LMDPL gate-level masking
- Design Priorities:
- Security
- Performance
- Area
Benefits
- High-performance and DPA resistance-proven AES cryptographic core
- Provides a higher level of protection than standard AES cores
- Extensively validated against side-channel attacks
- Highly flexible for integration with standard cipher modes such as CBC, ECB, etc.
- Easy-to-integrate into SoCs
Block Diagram
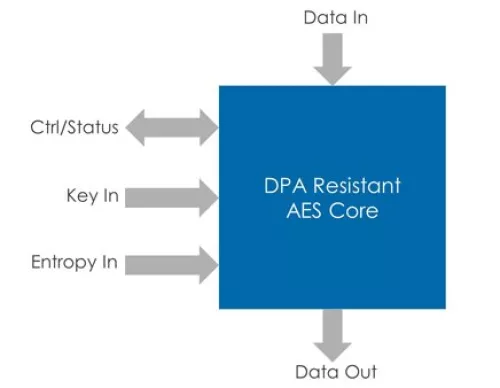
Applications
- Aerospace and Defense
- Content Protection
- Mobile
- Storage
- Secure Communications
- Automotive
- Payments/Point-of-Sale
- Internet of Things
Deliverables
- The DPA Resistant AES solution is available as either an IP core or a software library.
- DPA Resistant AES Core:
- Verilog RTL reference design
- Synthesis Inputs
- SDC constraint file suitable for FPGA or ASIC synthesis
- Documentation
- Usage guide
- Functional Testbench
- NIST-compliant test vectors
- Development and Test Environment (optional)
- DPA Workstation
- Implementation on reference FPGA board
- Integrated testing framework
- DPA Resistant AES Software Library:
- Reference design source code with build scripts and test vectors for the reference (ARM-based) platform
- Packaged libraries for a specific platform
- Development and Test Environment (optional)
- Hardware reference board for a specific platform
- DPA Workstation
- Specification sheet for DPA-resistant target level on a specific platform
- Documentation for library usage
- Cryptography Research software services
- Analysis, development, integration, optimization, and support
- Cryptography Research software support
- Quarterly or semiannual bug fixes and enhancements
- Periodic upgrades depending on customer priority
- Optional Cryptography Research services
- DPA and DPAWS training
- Software testing: testing performed either by Cryptography Research or by customer after training from Cryptography Research
Technical Specifications
Foundry, Node
Any
Maturity
Silicon proven