Secure IP
Filter
Compare
888
IP
from
94
vendors
(1
-
10)
-
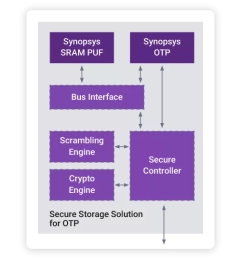
Secure Storage Solution for OTP IP
- Advanced Security: Encrypted storage in OTP using dynamic root key from SRAM PUF
- System-Level Security Extension: Add-on allows sharing the SRAM PUF to protect chip-level assets
- Flexible Security Configuration: Secure regions within OTP can be tailored to meet specific needs
-
Functional-Safety & Secure LPDDR3 Memory Subsystem
- Safe & Secure-LPDDR3 that is ready for ASIL (Automotive Safety Integrity Level) and secure by design
- Functional Safety out-of-the box design, with an extensive ASIL documentation package.
- Integrated security features into the controller. Characterized for extended operating conditions and long-term reliability.
-
ECC Secure Accelerator - High-performance ECC IP with advanced physical security
High-performance ECC IP with advanced physical security
-
ECC Secure Accelerator - Compact and Secure ECC IP Core for Resource-Constrained Devices
- Compact and Secure ECC IP Core for Resource-Constrained Devices
-
AES-XP-GCM-XTS Ultra-High-Performance Secure Core - High-Performance AES-GCM/XTS Core with Integrated SCA/FI Protection
- High-Performance AES-GCM/XTS Core with Integrated SCA/FI Protection
-
AES-XP-XTS Ultra-High-Performance Secure Core - High-Performance AES-XTS Core with RAMBAM-Based SCA/FI Protection
-
AES-XP-GCM Ultra-High-Performance Secure Core - Ultra-High-Performance AES-GCM Core with RAMBAM-Based SCA/FI Protection
- Ultra-High-Performance AES-GCM Core with RAMBAM-Based SCA/FI Protection
-
AES-SX-ULP-full Secure Core - High-Performance, Ultra Low-Power AES Encryption Core with Full Mode Support and Formally Proven SCA Protection
- High-Performance, Ultra Low-Power AES Encryption Core with Full Mode Support and Formally Proven SCA Protection
-
AES-SX-ULP-full Secure Core - High-Performance/Ultra Low Power AES Encryption Core with Full Mode Support and Formally Proven SCA Protection