AES crypto engine IP
Filter
Compare
26
IP
from
6
vendors
(1
-
10)
-
AES Mutli-Purpose crypto engine
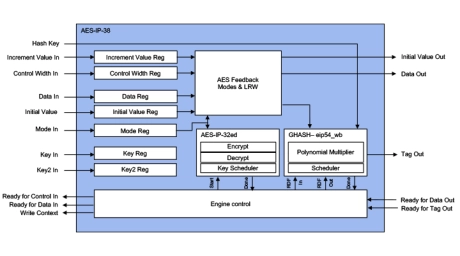
- The AES Multi-Purpose crypto engine includes a generic and scalable implementation of the AES algorithm and a configurable wrapper making the solution suitable for a wide range of low-cost & high-end applications.
-
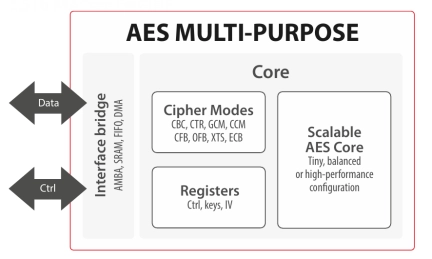
AES Multi-purpose crypto engine
- ASIC and FPGA
- Supports a wide selection of programmable ciphering modes based on NIST SP 800-38:
- Masking option available with excellent protection against SPA & DPA
- Context switching
-
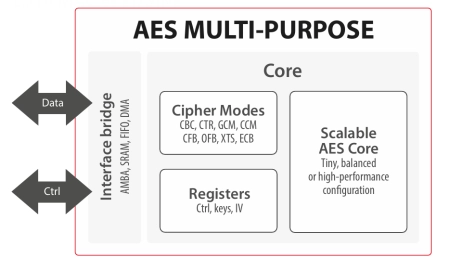
SM4-GCM Multi-Booster crypto engine
- ASIC & FPGA
- High throughput
- Guaranteed performance with small packets
-
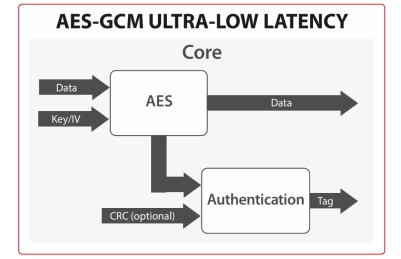
AES-GCM Ultra-low latency crypto engine
- The AES-GCM Ultra-low latency crypto engine is targeted for CXL link encryption with an implementation of the AES-GCM algorithm compliant with the NIST SP 800-38D standard.
- The unique architecture enables high throughput while maintaining an optimal resource usage.
-
Crypto Box Toolset Secure Accelerator
- The Crypto Box IP core is a high-efficiency cryptographic solution that combines RSA, ECC, AES, and a SHA-2/HMAC engine, all with advanced protections against side-channel and fault injection attacks.
- Designed for devices with balanced budgets for performance, area, and power, it enables secure key exchange, digital signatures, data encryption, and message authentication in a unified, compact architecture.
-
Crypto Box Toolset Secure Accelerator
- The Crypto Box IP core is a compact, power-efficient cryptographic engine that combines essential asymmetric algorithms (RSA, ECC) with high-speed AES encryption in a single integrated block.
- Designed for resource-constrained embedded systems, it enables secure key exchange, digital signatures, and fast data encryption with minimal area and power overhead.The
-
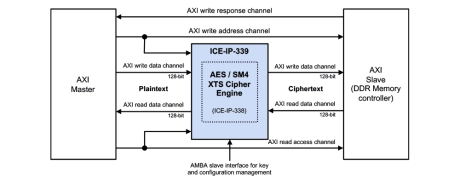
Inline cipher engine with AXI, for memory encryption
- Throughput: 128 bit (16 Byte) wide encryption/decryption per cycle
- Throughput: 1 tweak computation per 4 clock cycles
- Bidirectional design including arbitration between read and write requests
- Zero clock overhead for switching between encryption (write) and decryption (read)
- 30-40 cycle data channel latency
-
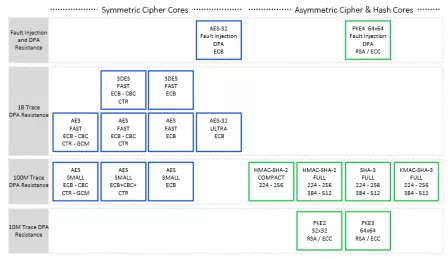
ChaCha20 DPA Resistant Crypto Accelerator
- Quicken time-to-market using precertified DPA Countermeasures
- Highly secure cryptographic engine primitives
- Extensive validation using the Test Vector Leakage Assessment (TVLA) methodology (revealing no leakage beyond 100 million traces)
- Cores protected against univariate first- and second-order side-channel attacks beyond 1 billion operations
-
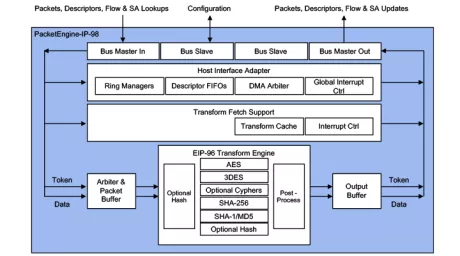
Multi-Protocol Engine with Classifier, Look-Aside, 5-10 Gbps
- Protocol aware IPsec, SSL, TLS, DTLS, 3GPP and MACsec Packet Engine with virtualization, caches classifier and Look-Aside interface for multi-core application processors
- 5-10 Gbps, programmable, maximum CPU offload by classifier, supports new and legacy crypto algorithms, AMBA interface
- Supported by Driver development kit, QuickSec IPsec toolkit, Linaro ODP, DPDK, Linux Crypto
-
AES XTS/GCM Accelerators
- Wide bus interface
- Basic AES encrypt and decrypt operations
- Key sizes: 128, 192 and 256 bits
- Key scheduling in hardware, allowing key, key size and direction changes every 13/15/17 clocks with zero impact on throughput
- Hardware reverse (decrypt) key generation