Publick Key Cryptography Engine IP
Filter
Compare
11
IP
from
5
vendors
(1
-
10)
-
Fast Public Key Engine with DPA or with DPA and FIA
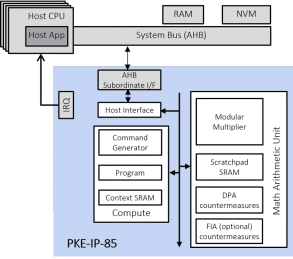
- The SCA-resistant PKE-IP-85 family of Public Key Engine cores provide semiconductor manufacturers with superior public key cryptography acceleration.
- The cores are easily integrated into ASIC/SoC and FPGA devices, offer a high-level of resistance to Differential Power Analysis (DPA), and, optionally, offer detection of Fault Injection Attacks (FIA).
-
Public Key Crypto Engine
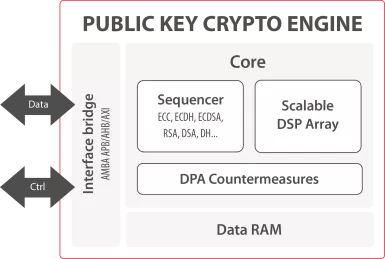
- The Public Key Crypto Engine is a versatile IP core for hardware offloading of all asymmetric cryptographic operations.
- It enables any SoC, ASIC and FPGA to support efficient execution of RSA, ECC-based algorithms and more.
- The IP core is ready for all ASIC and FPGA technologies.
-
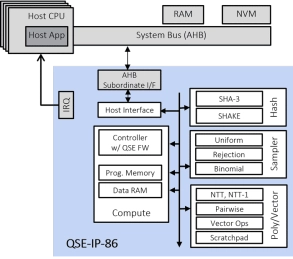
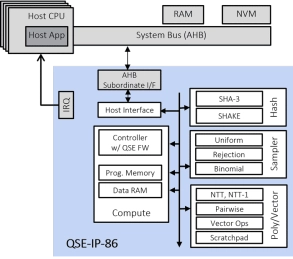
Fast Quantum Safe Engine for ML-KEM (CRYSTALS-Kyber) and ML-DSA (CRYSTALS-Dilithium)
- The Quantum Safe Engine (QSE) IP provides Quantum Safe Cryptography acceleration for ASIC, SoC and FPGA devices.
- The QSE-IP-86 core is typically integrated in a hardware Root of Trust or embedded secure element in chip designs together with a PKE-IP-85 core that accelerates classic public key cryptography and a TRNG-IP-76 core that generates true random numbers.
-
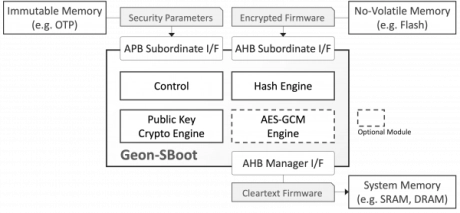
GEON™ Secure Boot Hardware Engine
- GEON-SBoot is an area-efficient, processor-agnostic hardware engine that protects SoC designs from booting with malicious or otherwise insecure code.
- The security platform employs public-key cryptography (which stores no secret on-chip) to ensure that only unmodified firmware from a trusted source is used by the system.
-
Fast Quantum Safe Engine for ML-KEM (CRYSTALS-Kyber) and ML-DSA (CRYSTALS-Dilithium) with DPA
- Compliant with FIPS 203 ML-KEM and FIPS 204 ML-DSA standards
- Uses CRYSTALS-Kyber, CRYSTALS-Dilithium quantum-resistant algorithms
- Includes SHA-3, SHAKE-128 and SHAKE-256 acceleration
- The embedded QSE CPU combined with Rambus-supplied firmware implements the full FIPS 203/204 protocols
-
ECDSA signature verification engine
- Optional Side Channel Attacks countermeasures
- Input/Output EC point verification
- Fully synthesizable, synchronous design
-
ECDSA signature verification engine
- Supported Elliptic Curves
- Optional Side Channel Attacks countermeasures
- Input/Output EC point verification
- Fully synthesizable, synchronous design
-
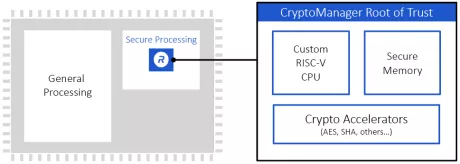
Programmable Root of Trust Family With DPA & Quantum Safe Cryptography
- Hardware Root of Trust employing a custom 32-bit RISC-V processor
- Multi-layered security model provides protection of all components in the core
- NIST CAVP and CMVP compliant for FIPS 140-3 validation
- State-of-the-art anti tamper techniques
- DPA-resistant cryptographic accelerators
- Caliptra Root of Trust for Measurement with DICE and X.509 support
-
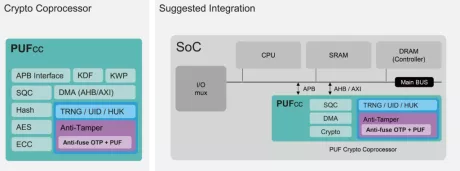
TLS 1.3 Compliant Crypto Coprocessor
- NIST CAVP certified and OSCCA standard compliant crypto engine suite
- Includes private/public key ciphers, message authentication code, hashes, and key derivation
- Key wrapping function for the secure export of keys
- Public-key coprocessor for digital signatures and key agreements over elliptic/Edward curves
-
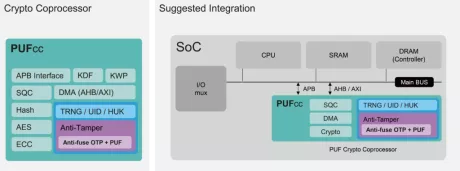
Crypto Coprocessor
- Comprehensively support all CPU architectures
- Crypto engine collective, consisting of private key cipher, message authentication code, hash, and key derivation functions that are NIST CAVP certified and OSCCA standards compliant
- Key wrapping function aiding the export of keys for external use