Post-Quantum Cryptography IP
Filter
Compare
24
IP
from
12
vendors
(1
-
10)
-
PUF-based Post-Quantum Cryptography (PQC) Solution
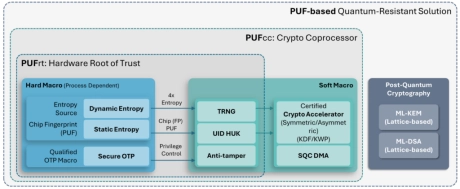
- PUFsecurity is proud to pioneer the world’s first PUF-based Post-Quantum Cryptography (PQC) solution, delivering cutting-edge, hardware-level security that sets a new standard.
- Our innovative solution integrates PUF technology with quantum-resistant cryptographic algorithms, ensuring robust key protection and seamless transition to a quantum-secure future.
-
High-Performance Hybrid Classical and Post-Quantum Cryptography
- The High-Performance Hybrid Cryptography IP core delivers accelerated support for both classical (RSA, ECC) and post-quantum (ML-KEM, ML-DSA) algorithms in a unified architecture optimized for maximum throughput.
-
Hybrid Classical and Post-Quantum Cryptography
- The Hybrid Cryptography IP core combines traditional asymmetric algorithms—such as RSA and ECC—with post-quantum standards including ML-KEM (Kyber) and ML-DSA (Dilithium)—in a single, efficient hardware module.
-
XMSS Post-Quantum Cryptography IP
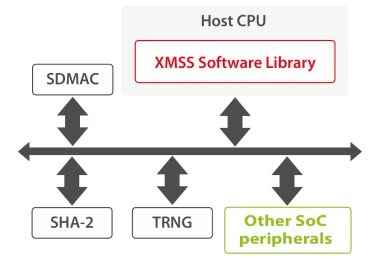
- XMSS is a Post-Quantum Cryptographic (PQC) algorithm, meaning it is mathematically designed to be robust against a cryptanalytic attack using a quantum computer.
- XMSS is a stateful Hash-Based Signature Scheme that has been recommended by NIST in 2020.
-
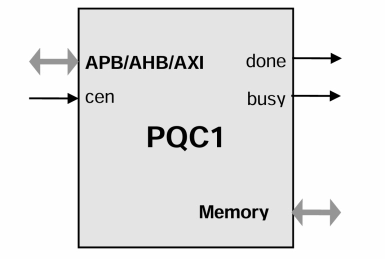
APB Post-Quantum Cryptography Accelerator IP Core
- Implements ML-KEM and ML-DSA post-quantum cryptography digital signature standards. The system interface is an microprocessor slave bus (APB, AHB, AXI options are available).
- The design is fully synchronous and requires only minimal CPU intervention due to internal microprogramming sequencer.
-
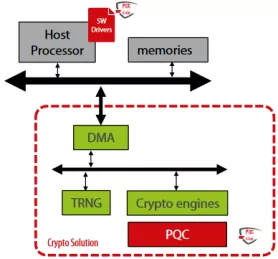
Crypto Coprocessor with integrated Post-Quantum Cryptography IPs
- The Crypto Coprocessors are a hardware IP core platform that accelerates cryptographic operations in System-on-Chip (SoC) environment on FPGA or ASIC.
- Symmetric operations are offloaded very efficiently as it has a built-in scatter/gather DMA. The coprocessors can be used to accelerate/offload IPsec, VPN, TLS/SSL, disk encryption, or any custom application requiring cryptography algorithms.
-
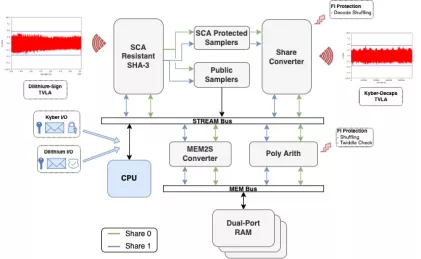
Unified Hardware IP for Post-Quantum Cryptography based on Kyber and Dilithium
- Turn-key implementations of the NIST FIPS recommended CRYSTALS post-quantum for key encapsulation (KEM) and digital signature algorithm (DSA)
-
ML-KEM / ML-DSA Post-Quantum Cryptography IP
- ML-KEM (Crystals-Kyber) and ML-DSA (Crystals-Dilithium) are Post-Quantum Cryptographic (PQC) algorithms, meaning they are mathematically designed to be robust against a cryptanalytic attack using a quantum computer.
- Both have been standardized by the NIST in it post-quantum cryptography project.
-
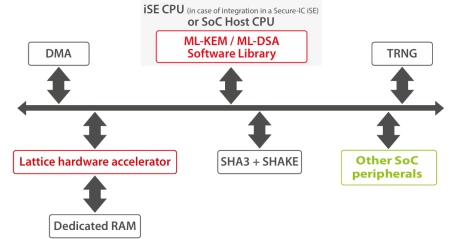
Post-Quantum Accelerator
- The Post-Quantum Cryptography IP core provides a high-efficiency hardware solution supporting ML-KEM (Kyber) and ML-DSA (Dilithium) as standardized in FIPS 203 and 204, along with additional hash-based signature schemes including SPHINCS+, XMSS, and LMS.
-
Post-Quantum ML-KEM IP Core
- Efficient Performance
- SCA/FIA Protections
- Patented High-Performance Modulo Multiplication
- Flexible Interfaces