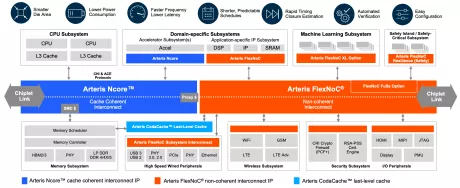
On-Chip Security IP
Filter
Compare
39
IP
from
14
vendors
(1
-
10)
-
SoC Security Platform / Hardware Root of Trust
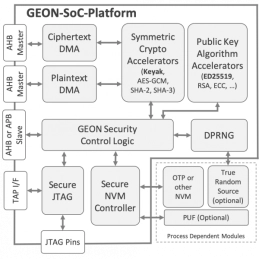
- GEON-SoC is an area-efficient, processor-agnostic, hardware root of trust for SoC designs.
- It implements secure boot and can optionally be enhanced to support firmware decryption and secure debug, or to act as a post-boot hardware security module (HSM).
-
Hardware Security Module
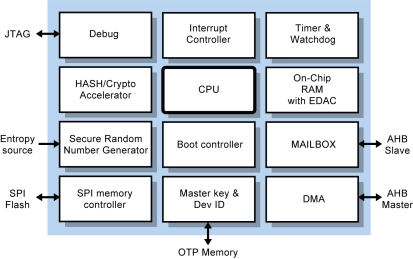
- GRHSM is an isolated system-on-chip (SoC) that can be used as a subsystem in a larger SoC design to implement a hardware security module or otherwise provide security functions to the larger system.
- Use cases include crypto key storage, boot authentication, supervision, and offloading of cryptographic functions.
-
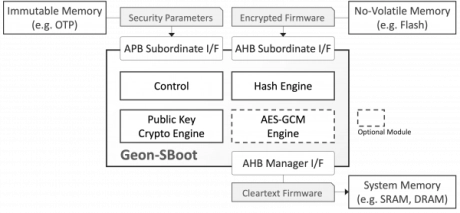
GEON™ Secure Boot Hardware Engine
- GEON-SBoot is an area-efficient, processor-agnostic hardware engine that protects SoC designs from booting with malicious or otherwise insecure code.
- The security platform employs public-key cryptography (which stores no secret on-chip) to ensure that only unmodified firmware from a trusted source is used by the system.
-
-
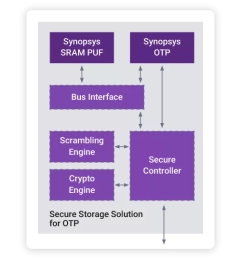
Secure Storage Solution for OTP IP
- Advanced Security: Encrypted storage in OTP using dynamic root key from SRAM PUF
- System-Level Security Extension: Add-on allows sharing the SRAM PUF to protect chip-level assets
- Flexible Security Configuration: Secure regions within OTP can be tailored to meet specific needs
-
Cryptographic Cores IP
- The Cryptographic Cores IP portfolio delivers secure, high-performance implementations of symmetric, asymmetric, and post-quantum algorithms.
- Designed for low-area, low-latency operation, the silicon-proven cores help SoC designers and embedded teams build trusted, efficient devices for IoT, automotive, medical, and industrial markets.
-
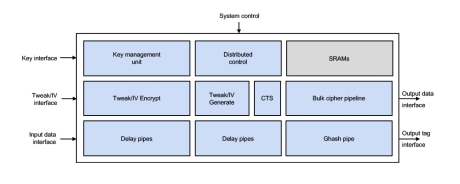
High-speed Inline Cipher Engine
- The ICE-IP-338 data path can be scaled to widths that are multiples of 128 bit to allow a tradeoff between area and performance that best fits the target application.
- Configuration options include or exclude support for CipherText Stealing (CTS), the GCM mode, and the SM4 algorithm and/or Datapath Integrity logic.
- The cryptographic AES and SM4 primitives can be provided with or without side channel attack DPA countermeasures.
-
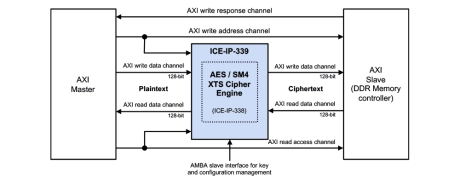
Inline cipher engine with AXI, for memory encryption
- Throughput: 128 bit (16 Byte) wide encryption/decryption per cycle
- Throughput: 1 tweak computation per 4 clock cycles
- Bidirectional design including arbitration between read and write requests
- Zero clock overhead for switching between encryption (write) and decryption (read)
- 30-40 cycle data channel latency
-
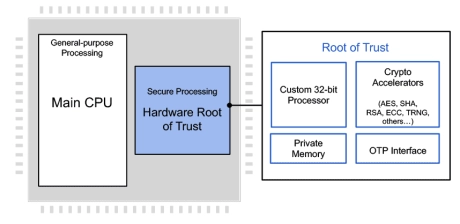
Programmable Root of Trust With DPA and FIA for US Defense
- Custom-designed 32-bit secure RISC-V processor
- Multi-layered security model protects all core components against a wide range of attacks
- Security model includes hierarchical privilege model, secure key management policy, hardware-enforced isolation/access control/protection, error management policy
- State-of-the-art DPA resistance, FIA protection and anti-tamper techniques
-
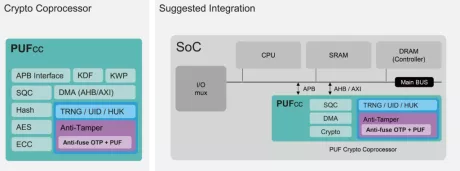
TLS 1.3 Compliant Crypto Coprocessor
- NIST CAVP certified and OSCCA standard compliant crypto engine suite
- Includes private/public key ciphers, message authentication code, hashes, and key derivation
- Key wrapping function for the secure export of keys
- Public-key coprocessor for digital signatures and key agreements over elliptic/Edward curves