MACsec IP
Filter
Compare
81
IP
from
15
vendors
(1
-
10)
-
HPC MACsec Security Modules for Ethernet
- IEEE 802.1ae, IEEE 802.1br Support
- 100 Gbps—1.6 Tbps
- Can reach higher throughputs scalable to 3.2 Tbps
- Supports also lower performance modes down to 10 Gbps
-
ASIL B / ISO 26262 and ISO 21434 Compliant 1G-25G MACsec Security Module
- Synopsys MACsec Security Modules use scalable AES-GCM cryptography to provide confidentiality, integrity, authentication, and replay protection for Ethernet traffic.
- These modules integrate seamlessly with Synopsys Ethernet MAC & PCS IP, supporting high data rates with low latency. By incorporating Synopsys MACsec Security Modules into Ethernet IP solutions, networking SoC designers can ensure end-to-end security for data in motion between Ethernet-connected devices.
-
P1619 / 802.1ae (MACSec) GCM/XTS/CBC-AES Core
- Small size: From 70K ASIC gates (at throughput of 18.2 bits per clock)
- 500 MHz frequency in 90 nm process
- Easily parallelizable to achieve higher throughputs
- Completely self-contained: does not require external memory. Includes encryption, decryption, key expansion and data interface
-
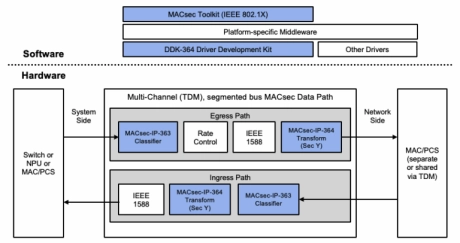
1.6T/3.2T Multi-Channel MACsec Engine with TDM Interface (MACsec-IP-364)
- The MACsec-IP-364 is a MACsec/IPsec engine developed specifically for high-speed, multi-rate and multi-port Ethernet devices.
- Its architecture provides an optimal multi-protocol solution for aggregate throughput for 1.6T and 3.2T.
- The MACsec-IP-364 is ideal for deployment in data center, enterprise and carrier network applications, as well as network-attached high-performance computing.
-
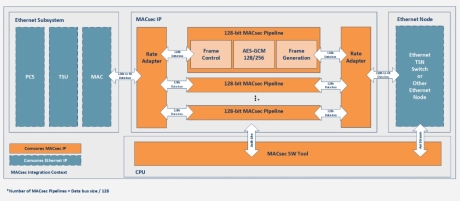
100G / 200G / 400G / 800G / 1.6T MACsec
- The MACsec IP provides Ethernet Layer 2 Security for port authentication, data confidentiality and data integrity as standardized in IEEE 802.1AE.
- It protects components in Ethernet networks especially very high-speed Ethernet used in cloud, data center, and backhaul networks.
- The MACsec IP is a fully compliant solution that provides line-rate encryption and supports VLAN-in-Clear.
-
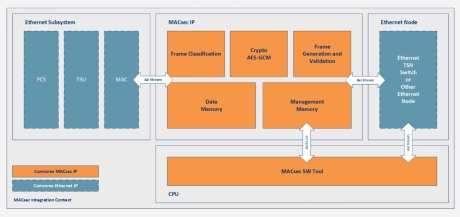
10M MACsec
- The MACsec IP provides Ethernet Layer 2 Security for port authentication, data confidentiality and data integrity as standardized in IEEE 802.1AE.
- It protects components in Ethernet networks especially very low-speed Ethernet used in automotive, industrial, and consumer applications.
- The MACsec IP is a fully compliant solution that provides line-rate encryption and is optimized for the smallest area size.
-
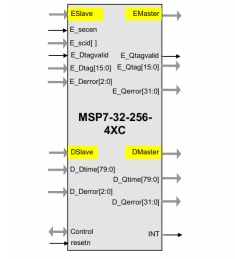
MSP7-32 MACsec IP core for FPGA or ASIC
- The MSP7 implementation fully supports the IEEE 802.1ae (MACsec) algorithm for 128-bit bit keys, including AES support in Galois Counter Mode (GCM) per NIST publication SP800-38D.
- The core is designed for flow-through operation. MSP7 supports encryption and decryption modes (encrypt-only and decrypt-only options are available.
-
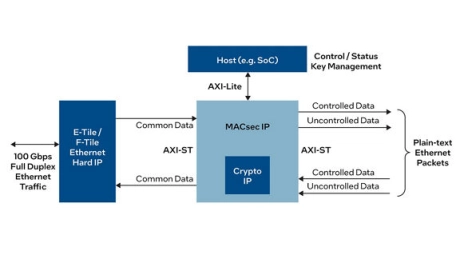
MACsec Intel® FPGA IP
- The MACsec Intel® FPGA IP core implements the IEEE Media Access Control Security standard as defined in 802.1AE (2018) as fully configurable soft IP
- MACsec provides data confidentiality and integrity for the Ethernet protocol and is commonly used to secure network traffic in 5G systems, between the cloud and data center, and between IoT devices.
-
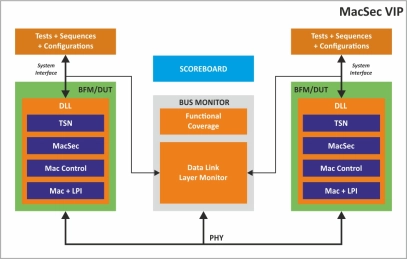
MacSec Verification IP
- Provides Ethernet fully compliant to 802.3-2018 supporting all media independent interfaces for (1/10/25/40/50/100/200/400/800 G)
- Provides MacSec as per IEEE standard 802.1AE-2018 specification
- Supports controlled and uncontrolled ports
- Encodes and decodes MacSeC PDUs
- Protects and validates macSec Pdus using AES-GCM-128 Cipher suites
- Cryptographic protection
- Modification and Addition of MSDU
- Uses configurable secure association key for encryption and authentication
- Supports Vlan and jumbo frames
- Supports Replay protection and ICV Works in tandem with gPTP (IEEE 802.1AS)/ PTP (IEEE 1588)
- Supports controlled and uncontrolled ports
- Encodes and decodes MacSeC PDUs
-
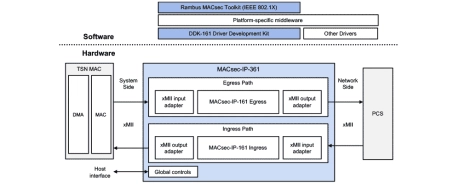
1G to 50G Single-Port MACsec Engine with xMII interface and TSN support
- MACsec solution for integration between MAC and PCS side supporting 1GbE to 50GbE rates with optional TSN support (including IEEE803.2br).
- For MACsec function integrates the MACsec-IP-161 with all IEEE MACsec standards supported. Optional Cisco ClearTags.
- Supplied with the Driver Development Kit to accelerate time to market. Rambus offers MACsec Toolkit for IEEE 802.1X key management