Hashing engine IP
Filter
Compare
12
IP
from
7
vendors
(1
-
10)
-
ASCON Authenticated Encryption & Hashing Engine
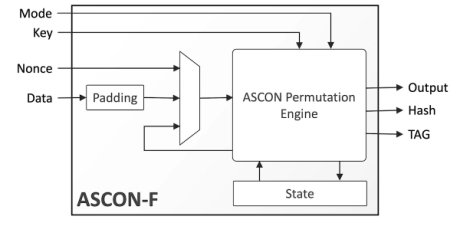
- The ASCON-F IP core is a compact, high-throughput hardware engine implementing the lightweight authenticated encryption with associated data (AEAD) and hashing algorithms described in the Ascon v1.2 specification.
- A single instance of the ASCON-F IP core can encrypt or decrypt data using the Ascon-128 and Ascon-128a functions or perform Cryptographic hashing Hash per the Ascon-Hash and Ascon-Hasha functions.
-
Security Hash, SM3 Hash and HMAC Engine
- The hash processor is a fully compliant implementation of the secure hash algorithm (SHA-1, SHA-224, SHA-256, SHA-384, SHA-512), the MD5 (message-digest algorithm 5) and SM3 hash algorithm and the HMAC (keyed-hash message authentication code) algorithm suitable for a variety of applications. HMAC is suitable for applications requiring message authentication.
-
GEON™ Secure Boot Hardware Engine
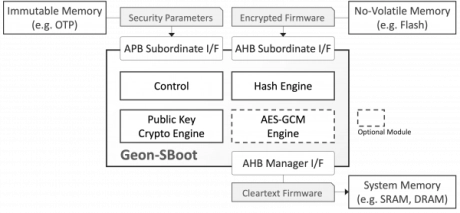
- GEON-SBoot is an area-efficient, processor-agnostic hardware engine that protects SoC designs from booting with malicious or otherwise insecure code.
- The security platform employs public-key cryptography (which stores no secret on-chip) to ensure that only unmodified firmware from a trusted source is used by the system.
-
Keccak Hash Engine
- The Keccak Hash crypto engine is an IP core and built with a focus on simplicity and seamless integration, while also following coding and verification practices in the industry.
- It operates in a single clock domain and has been extensively verified.
- It can be flexibly configured and customized to support different output lengths and security levels.
-
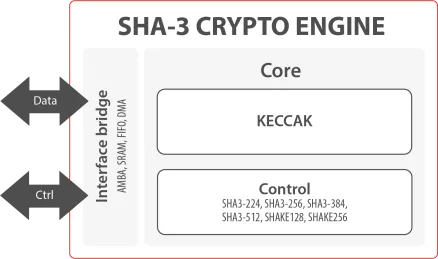
SHA-3 Crypto Engine
- The SHA-3 crypto engine has integrated flexibility and scalability to allow for high throughput and a configurable number of hashing rounds per clock cycle to optimize the silicon resource/performance ratio.
- Fixed-length or extendable-output (XOF) functions can simply be chosen per individual message through configuration settings.
-
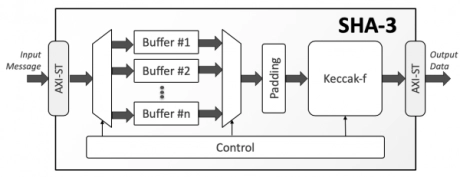
SHA-3 Secure Hash Crypto Engine
- The SHA-3 is a high-throughput, area-efficient hardware accelerator for the SHA-3 cryptographic hashing functions, compliant to NIST’s FIPS 180-4 and FIPS 202 standards.
- The accelerator core requires no assistance from a host processor and uses standard AMBA® AXI4-Stream interfaces for input and output data.
-
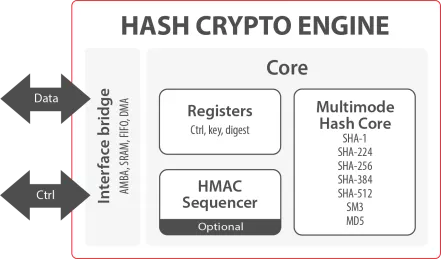
Hash Crypto Engine
- The Hash Crypto Engine is flexible and optimized hash IP core compliant with FIPS 180-3 (HASH functions), FIPS 198 (HMAC function) and OSCCA (SM3).
- With a flexible wrapper supporting a wide selection of programmable hashing modes (SHA-1, SHA-224, SHA-256, SHA-384, SHA-512, SM3 and MD5) with HMAC and several options of data interface, the Hash Crypto Engine is an easy-to-use solution with predictable resources and performances on ASIC and FPGA.
-
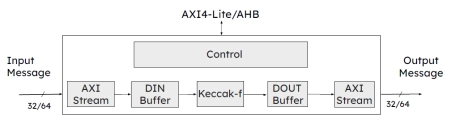
SHA-3 Crypto IP Core
- The SHA-3 – secure hash algorithms – crypto engine is a hardware accelerator for cryptographic hashing functions.
- It is an area efficient and high throughput design and compliant to NIST’s FIPS 202 standard.
- Additionally it supports all SHA-3 hash functions – SHA-3-224, SHA-3-256, SHA-3-384 and SHA-3-512 – as well as extendable output functions (XOF) – SHAKE-128 and SHAKE-256.
-
Crypto Box Toolset Secure Accelerator
- The High-Performance Hybrid Crypto Box IP core delivers maximum cryptographic throughput by combining classical asymmetric (RSA, ECC), symmetric (AES), and hashing (SHA-2/HMAC) engines with a dedicated post-quantum accelerator supporting ML-KEM (Kyber) and ML-DSA (Dilithium).
- Designed for performance-critical systems without tight area or power limitations, this IP enables ultra-fast key exchange, digital signatures, and secure data processing.
-
Multipurpose Security Protocol Accelerator
- Highly configurable security accelerator
- Support for all ciphers, hashes and MAC algorithms used in major protocols such as IPsec, SSL/TLS/DTLS, Wi-Fi, 3GPP LTE/LTE-A, SRTP, MACsec
- Cipher algorithms: AES, DES/3DES, ChaCha20, MULTI2, KASUMI, SNOW 3G, ZUC
- Cipher modes: ECB, CBC, CTR, OFB, CFB, f8, XTS, UEA1, UEA2, 128-EEA1, 128-EEA2, 128-EEA3