Crypto Module IP
Filter
Compare
31
IP
from
12
vendors
(1
-
10)
-
nQrux™ Crypto Module
- Compatible with applicable NIST, IETF, and IEEE standards, RFCs, and test vectors for compliance and certification programs

-
ASIL B / ISO 26262 and ISO 21434 Compliant 1G-25G MACsec Security Module
- Synopsys MACsec Security Modules use scalable AES-GCM cryptography to provide confidentiality, integrity, authentication, and replay protection for Ethernet traffic.
- These modules integrate seamlessly with Synopsys Ethernet MAC & PCS IP, supporting high data rates with low latency. By incorporating Synopsys MACsec Security Modules into Ethernet IP solutions, networking SoC designers can ensure end-to-end security for data in motion between Ethernet-connected devices.
-
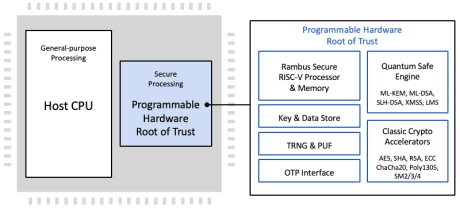
Quantum Safe, ISO 21434 Automotive-grade Programmable Hardware Security Module
- The automotive-grade CryptoManager RT-7xx v3 Root of Trust family is the next generation of fully programmable ISO 26262 and ISO 21434 compliant hardware security modules offering Quantum Safe security by design for secure automotive applications.
- The CryptoManager RT-7xx family protects against a wide range of hardware and software attacks through state-of-the-art side channel attack countermeasures and anti-tamper and security techniques.
-
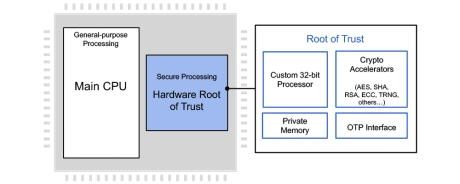
Embedded Hardware Security Module (Root of Trust) - Automotive Grade ISO 26262 ASIL-B
- The RT-64x Embedded Hardware Security Module (Root of Trust) family are fully programmable, ISO 26262 ASIL-B hardware security cores offering security by design for automotive applications.
- They protect against a wide range of failures such as permanent, transient and latent faults and hardware and software attacks with state-of-the-art anti-tamper and security techniques.
-
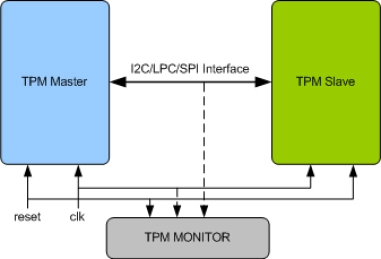
Trusted Platform Module (TPM) Verification IP
- Full TPM master device and slave device functionality.
- Compliant to the Trusted Computing Group (TCG) Trusted Platform Module(TPM) Version 1.1b/1.2 and 2.0 Specification
- Compliant with TCG PC client-specific TPM Interface Specification (TIS) version 1.2/1.3
- Hardware Asymmetric Crypto Engine.
-
Hardware Security Module
- GRHSM is an isolated system-on-chip (SoC) that can be used as a subsystem in a larger SoC design to implement a hardware security module or otherwise provide security functions to the larger system.
- Use cases include crypto key storage, boot authentication, supervision, and offloading of cryptographic functions.
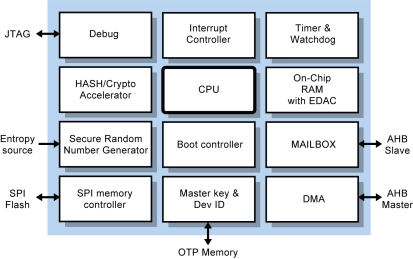
-
tRoot V500 Hardware Secure Module
- Complete hardware secure modules with Root of Trust give SoCs a unique, tamper-proof identity
- Enable secure services deployment
- Provide a Trusted Execution Environment to create, provision, store and manage keys
- Full hardware key protection
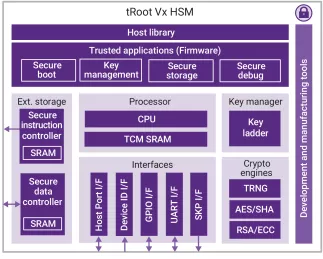
-
tRoot F022 Hardware Secure Module (w/ ARC EM22FS)
- ASIL B Certified tRoot Hardware Secure Module provides the Root of Trust for a system, protects against malicious attacks, and prevents random and systematic faults
- Meets stringent ISO 26262 safety process and documentation requirements (ASIL D systematic grade)
- Fully programmable solution safeguards against evolving threats with high-grade security
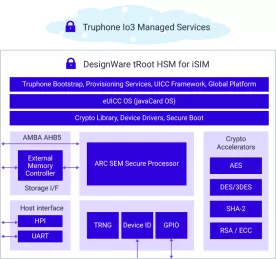
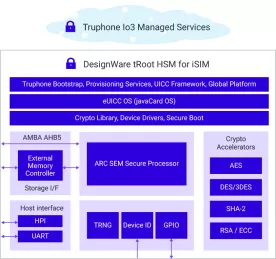
-
tRoot V023 FS Hardware Secure Module, ASIL-B compliant (w/ ARC EM22FS)
- ASIL B Certified tRoot Hardware Secure Module provides the Root of Trust for a system, protects against malicious attacks, and prevents random and systematic faults
- Meets stringent ISO 26262 safety process and documentation requirements (ASIL D systematic grade)
- Fully programmable solution safeguards against evolving threats with high-grade security
-
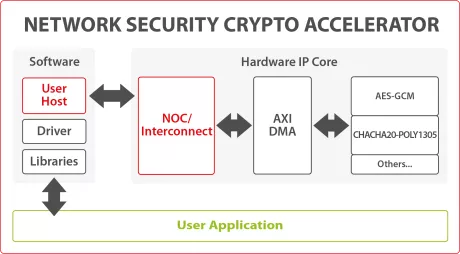
Network Security Crypto Accelerator
- The Network Security Crypto Accelerator is a hardware IP core platform that accelerates cryptographic operations in System-on-Chip (SoC) environment on FPGA or ASIC.
- This IP is used to accelerate/offload MACsec, IPsec, VPN, TLS/SSL, disk encryption, or any other custom application, requiring symmetric cryptography algorithms.