AES Accelerator IP
Filter
Compare
43
IP
from
10
vendors
(1
-
10)
-
AES Authenticated Encryption Accelerator with DPA or with DPA and FIA
- The SCA-resistant AES-IP-3X family of crypto accelerator cores provide semiconductor manufacturers with superior AES cipher acceleration.
- The cores are easily integrated into ASIC/SoC and FPGA devices and offer a high-level of resistance to various Side Channel Attacks like Differential Power Analysis (DPA), and optionally offer detection of Fault Injection Attacks (FIA).
-
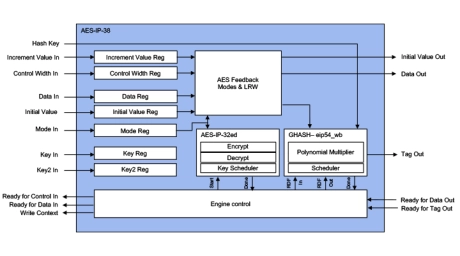
AES XTS/GCM Accelerators
- Wide bus interface
- Basic AES encrypt and decrypt operations
- Key sizes: 128, 192 and 256 bits
- Key scheduling in hardware, allowing key, key size and direction changes every 13/15/17 clocks with zero impact on throughput
- Hardware reverse (decrypt) key generation
-
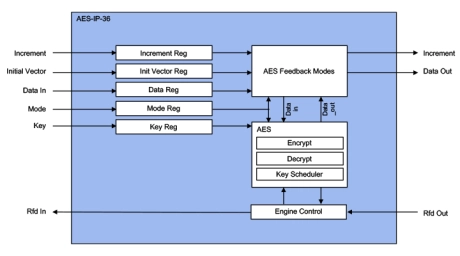
AES ECB/CBC/CTR Accelerators
- The AES-IP-36 (EIP-36) is IP for accelerating the AES symmetric cipher algorithm (FIPS-197), supporting ECB, CBC and CTR modes up to 12.8 Gbps @ 1GHz.
- Designed for fast integration, low gate count and full transforms, the AES-IP-36 accelerator provides a reliable and cost-effective embedded IP solution that is easy to integrate into high speed crypto pipelines.
-
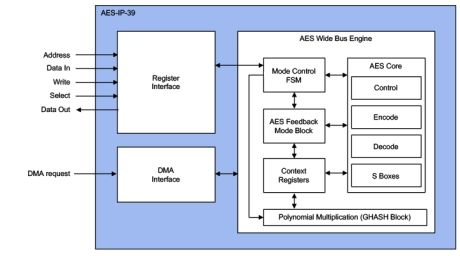
AES “All Modes” Accelerators
- The AES-IP-39 (EIP-39) is IP for accelerating the AES symmetric cipher algorithm (FIPS-197), supporting all NIST modes including ECB, CBC, CTR, CFB, OFB, CCM, GCM, CBC-MAC, CMAC, XTS, F8, F9 modes of operation up to 6.4 Gbps @ 1GHz.
- Designed for fast integration, low gate count and full transforms, the AES-IP-39 accelerator provides a reliable and cost-effective embedded IP solution that is easy to integrate into security modules needing versatile crypto.
-
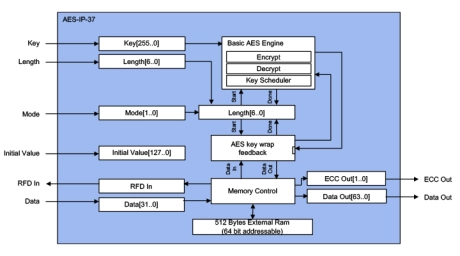
AES Key Wrap Accelerators
- Wide bus interface (128-bit data, 256-bit keys) or 32-bit register interface
- Key/KEK sizes: 128, 192 and 256 bits
- Includes key scheduling hardware
- Supported modes: NIST AES Key Wrap
- Memory interface for key, intermediate and result data storage up to 4096 bits (Maximum supported input data block size is 512 bytes)
-
Crypto Box Toolset Secure Accelerator
- The High-Performance Hybrid Crypto Box IP core delivers maximum cryptographic throughput by combining classical asymmetric (RSA, ECC), symmetric (AES), and hashing (SHA-2/HMAC) engines with a dedicated post-quantum accelerator supporting ML-KEM (Kyber) and ML-DSA (Dilithium).
- Designed for performance-critical systems without tight area or power limitations, this IP enables ultra-fast key exchange, digital signatures, and secure data processing.
-
Crypto Box Toolset Secure Accelerator
- The Hybrid Crypto Box IP core is a comprehensive, high-efficiency cryptographic solution that combines RSA, ECC, AES, and SHA-2/HMAC with a built-in accelerator for post-quantum algorithms such as ML-KEM (Kyber) and ML-DSA (Dilithium). Designed for embedded systems with balanced resource constraints, it enables secure key exchange, digital signatures, authenticated encryption, and hashing, future-proofed for the quantum era.
-
Crypto Box Toolset Secure Accelerator
- The Crypto Box IP core is a high-efficiency cryptographic solution that combines RSA, ECC, AES, and a SHA-2/HMAC engine, all with advanced protections against side-channel and fault injection attacks.
- Designed for devices with balanced budgets for performance, area, and power, it enables secure key exchange, digital signatures, data encryption, and message authentication in a unified, compact architecture.
-
Crypto Box Toolset Secure Accelerator
- The Crypto Box IP core is a compact, power-efficient cryptographic engine that combines essential asymmetric algorithms (RSA, ECC) with high-speed AES encryption in a single integrated block.
- Designed for resource-constrained embedded systems, it enables secure key exchange, digital signatures, and fast data encryption with minimal area and power overhead.The
-
Multipurpose Security Protocol Accelerator
- Highly configurable security accelerator
- Support for all ciphers, hashes and MAC algorithms used in major protocols such as IPsec, SSL/TLS/DTLS, Wi-Fi, 3GPP LTE/LTE-A, SRTP, MACsec
- Cipher algorithms: AES, DES/3DES, ChaCha20, MULTI2, KASUMI, SNOW 3G, ZUC
- Cipher modes: ECB, CBC, CTR, OFB, CFB, f8, XTS, UEA1, UEA2, 128-EEA1, 128-EEA2, 128-EEA3