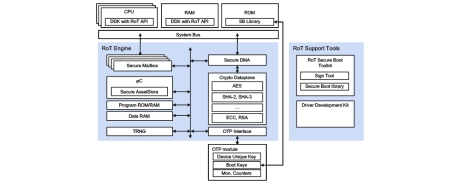
Root of Trust IP
Filter
Compare
58
IP
from
14
vendors
(1
-
10)
-
Root of Trust
- Root of Trust IP is a Hardware Secure Module (HSM) solution that provides the security foundation for processors and System on Chips (SoCs).
- It protects critical systems especially devices used in automotive, industrial, cloud, data center, and wireless applications.
-
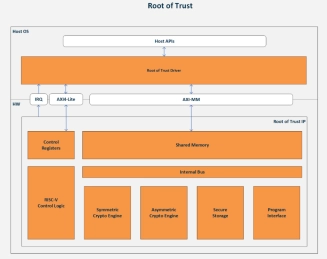
Embedded Hardware Security Module (Root of Trust) - Automotive Grade ISO 26262 ASIL-B
- The RT-64x Embedded Hardware Security Module (Root of Trust) family are fully programmable, ISO 26262 ASIL-B hardware security cores offering security by design for automotive applications.
- They protect against a wide range of failures such as permanent, transient and latent faults and hardware and software attacks with state-of-the-art anti-tamper and security techniques.
-
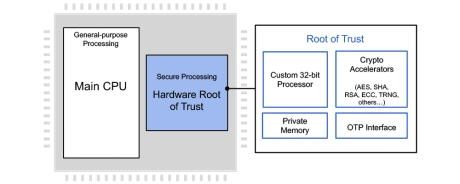
Programmable Root of Trust with Quantum Safe Cryptography acceleration, DPA-resistant & FIA-protected cryptographic accelerators and Caliptra RoTM
- The CryptoManager RT-6xx v3 Root of Trust family from Rambus is the latest generation of fully programmable FIPS 140-3 compliant hardware security cores offering Quantum Safe security by design for data center and other highly secure applications.
- Device and system architects face a growing array of security threats, including the threat of quantum computers. Across applications, one constant is the need for a hardware Root of Trust-based security implementation.
-
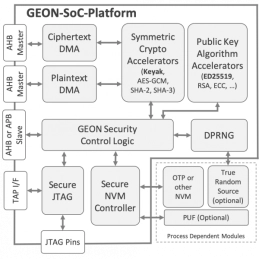
SoC Security Platform / Hardware Root of Trust
- GEON-SoC is an area-efficient, processor-agnostic, hardware root of trust for SoC designs.
- It implements secure boot and can optionally be enhanced to support firmware decryption and secure debug, or to act as a post-boot hardware security module (HSM).
-
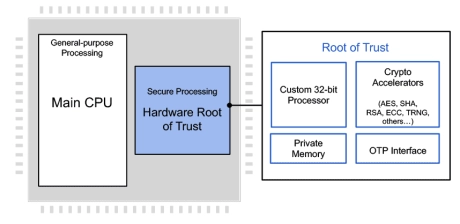
Programmable Root of Trust With DPA and FIA for US Defense
- Custom-designed 32-bit secure RISC-V processor
- Multi-layered security model protects all core components against a wide range of attacks
- Security model includes hierarchical privilege model, secure key management policy, hardware-enforced isolation/access control/protection, error management policy
- State-of-the-art DPA resistance, FIA protection and anti-tamper techniques
-
tRoot Fx Hardware Secure Modules: Programmable Root of Trust
- Efficient ARC SEM Security Processor
- SoC host and peripheral interfaces
- APEX cryptography acceleration (CryptoPack)
- Clock and reset management
-
Silicon Proven Hardware Root of Trust
- The Root of Trust (RoT) is always the trusted root within a cryptographic system. Cryptographic systems use encryption keys to encrypt data and perform functions such as digital signature creation and signature verification.
- Therefore, in order to fundamentally guarantee the operation of these functions, a hardened hardware module that is impervious to various types of attacks is used.
-
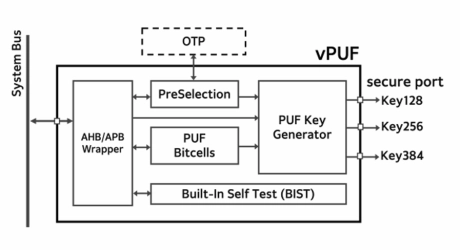
Via-PUF Security Chip for Root of Trust
-
The vPUF® IP, powered by Via PUF (Physically Unclonable Function) technology, provides a unique silicon fingerprint for inborn identity function, essential for the Root of Trust in security applications
-
-
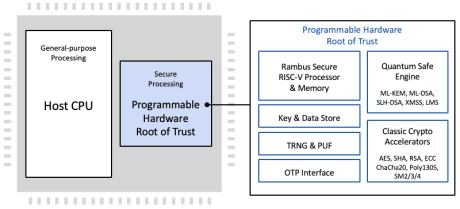
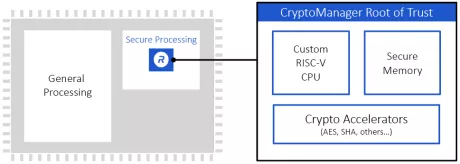
Programmable Root of Trust Family With DPA & Quantum Safe Cryptography
- Hardware Root of Trust employing a custom 32-bit RISC-V processor
- Multi-layered security model provides protection of all components in the core
- NIST CAVP and CMVP compliant for FIPS 140-3 validation
- State-of-the-art anti tamper techniques
- DPA-resistant cryptographic accelerators
- Caliptra Root of Trust for Measurement with DICE and X.509 support
-
Root of Trust - Foundational security for SoCs, secure MCU devices and sensors
- Secure Boot assist to host CPU(s) and protection of key material
- Secure firmware upgrade management for Host CPU
- Lifecycle management support
- Secure Debug support