Secure boot IP
Filter
Compare
87
IP
from
25
vendors
(1
-
10)
-
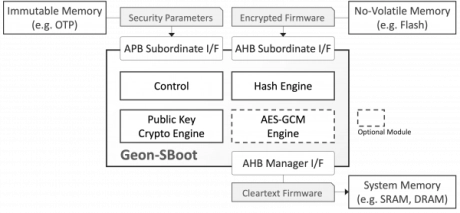
GEON™ Secure Boot Hardware Engine
- GEON-SBoot is an area-efficient, processor-agnostic hardware engine that protects SoC designs from booting with malicious or otherwise insecure code.
- The security platform employs public-key cryptography (which stores no secret on-chip) to ensure that only unmodified firmware from a trusted source is used by the system.
-
Secure Boot Software Development Kit
- Based on NIST CAVP validated cryptographic algorithms and standards
- AES-CCM and AES-CTR content encryption
- SHA-256 hashing
- RSA PKCS #1 and X9.62 EC-DSA verification
-
Crypto Box Toolset Secure Accelerator
- The High-Performance Hybrid Crypto Box IP core delivers maximum cryptographic throughput by combining classical asymmetric (RSA, ECC), symmetric (AES), and hashing (SHA-2/HMAC) engines with a dedicated post-quantum accelerator supporting ML-KEM (Kyber) and ML-DSA (Dilithium).
- Designed for performance-critical systems without tight area or power limitations, this IP enables ultra-fast key exchange, digital signatures, and secure data processing.
-
Crypto Box Toolset Secure Accelerator
- The Hybrid Crypto Box IP core is a comprehensive, high-efficiency cryptographic solution that combines RSA, ECC, AES, and SHA-2/HMAC with a built-in accelerator for post-quantum algorithms such as ML-KEM (Kyber) and ML-DSA (Dilithium). Designed for embedded systems with balanced resource constraints, it enables secure key exchange, digital signatures, authenticated encryption, and hashing, future-proofed for the quantum era.
-
Crypto Box Toolset Secure Accelerator
- The Crypto Box IP core is a high-efficiency cryptographic solution that combines RSA, ECC, AES, and a SHA-2/HMAC engine, all with advanced protections against side-channel and fault injection attacks.
- Designed for devices with balanced budgets for performance, area, and power, it enables secure key exchange, digital signatures, data encryption, and message authentication in a unified, compact architecture.
-
Crypto Box Toolset Secure Accelerator
- The Crypto Box IP core is a compact, power-efficient cryptographic engine that combines essential asymmetric algorithms (RSA, ECC) with high-speed AES encryption in a single integrated block.
- Designed for resource-constrained embedded systems, it enables secure key exchange, digital signatures, and fast data encryption with minimal area and power overhead.The
-
Secure RoT Core for Data Centers
- Efficient Performance
- SCA/FIA Protections
- Flexible Interfaces
- Security Certification Readiness
-
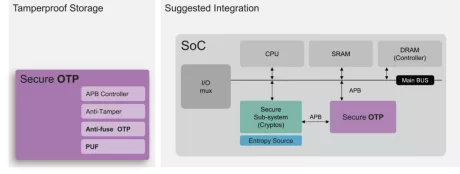
Secure OTP
- Up to 128kb mass production OTP with built-in instant hardware encryption (customization available)
- Comprehensive anti-tamper designs in physical and RTL
- APB control interface with secure/non-secure access privilege
- Four 256-bit hardware PUF fingerprints for scrambling drop-in-use Secure OTP Storage
-
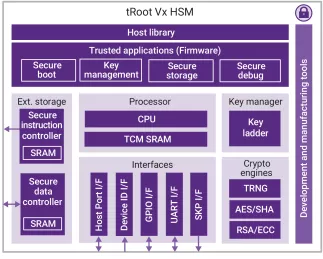
tRoot V500 Hardware Secure Module
- Complete hardware secure modules with Root of Trust give SoCs a unique, tamper-proof identity
- Enable secure services deployment
- Provide a Trusted Execution Environment to create, provision, store and manage keys
- Full hardware key protection