Secure Boot Hardware Engine IP
Filter
Compare
26
IP
from
11
vendors
(1
-
10)
-
GEON™ Secure Boot Hardware Engine
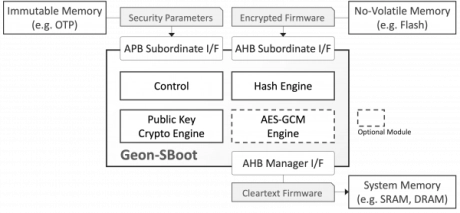
- GEON-SBoot is an area-efficient, processor-agnostic hardware engine that protects SoC designs from booting with malicious or otherwise insecure code.
- The security platform employs public-key cryptography (which stores no secret on-chip) to ensure that only unmodified firmware from a trusted source is used by the system.
-
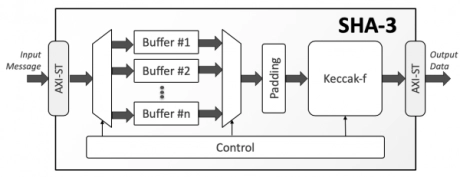
SHA-3 Secure Hash Crypto Engine
- The SHA-3 is a high-throughput, area-efficient hardware accelerator for the SHA-3 cryptographic hashing functions, compliant to NIST’s FIPS 180-4 and FIPS 202 standards.
- The accelerator core requires no assistance from a host processor and uses standard AMBA® AXI4-Stream interfaces for input and output data.
-
tRoot Vx Hardware Secure Modules
- The Synopsys tRoot Vx HSMs include a highly secure hardware Root of Trust that enables devices to boot securely and permits encryption and decryption of sensitive data allowing it to be stored in non-secure devices or memory. It provides a completely secure environment in a non-secure system from which applications can execute secure cryptographic services.
- The tRoot Vx HSMs secure SoCs by using unique code protection mechanisms that provide run-time tamper detection and response. Code privacy protection is achieved without the added cost of dedicated secure memory. This unique feature reduces system complexity and cost by allowing the tRoot Vx HSM’s firmware to reside in any non-secure memory space.
- Commonly, tRoot Vx programs reside in shared system DDR memory. Due to the confidentiality and integrity provisions of the secure instruction controller, this memory is effectively private to the HSM and impervious to attempts to modify it originating in other subsystems in the chip, or from outside. The tRoot Vx HSM’s ROM-less architecture can support system design changes at any time without risk of exposing the system memory to threats and without additional engineering development cost. To minimize the number of attack vectors, tRoot Vx HSMs use a simple interface with a limited set of interactions with the host processor.
-
Secure Boot Software Development Kit
- Based on NIST CAVP validated cryptographic algorithms and standards
- AES-CCM and AES-CTR content encryption
- SHA-256 hashing
- RSA PKCS #1 and X9.62 EC-DSA verification
-
Secure RoT Core for Data Centers
- Efficient Performance
- SCA/FIA Protections
- Flexible Interfaces
- Security Certification Readiness
-
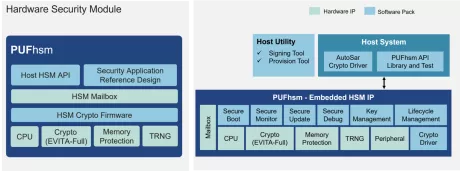
Embedded Hardware Security Module for Automotive and Advanced Applications
- Pre-integrated CPU
- Full suite of hardware-accelerate cryptographic engine (Meet EVITA-Full requirements)
- Complete SDK with APIs for HSM operations to support chip security applications.
- MailBox Interface to facilitate communication between the main system and HSM.
-
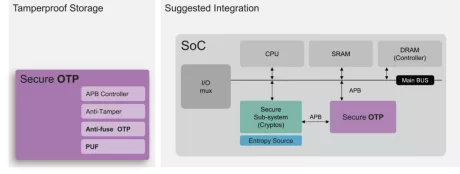
Secure OTP
- Up to 128kb mass production OTP with built-in instant hardware encryption (customization available)
- Comprehensive anti-tamper designs in physical and RTL
- APB control interface with secure/non-secure access privilege
- Four 256-bit hardware PUF fingerprints for scrambling drop-in-use Secure OTP Storage
-
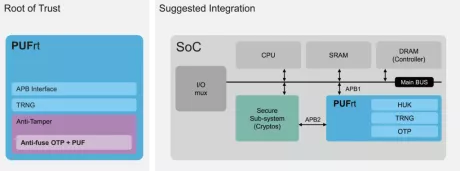
Hardware Root of Trust IP
- Built-in standard APB controller with privilege control to create secure/non-secure separation. Additionally, interface customization is available for different design requirements.
- Four 256-bit hardware PUF chip fingerprints, include a self-health check that can be used as a unique identification(UID) or a root key(seed).
- High-quality true random number generator (TRNG)
- 8k-bit mass production OTP with built-in instant hardware encryption (customization available)
-
100% Secure Cryptographic System for RSA, Diffie-Hellman and ECC with AMBA AHB, AXI4 and APB
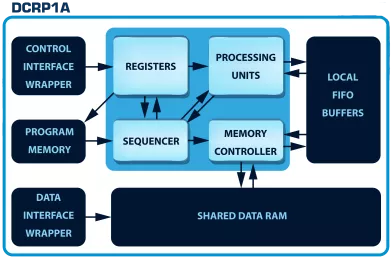
- The DCRP1A - CryptOne IP is a 100% secure cryptographic system
- CryptOne is a fully scalable, hardware-accelerated cryptographic system
- Designed for next-generation SoCs, FPGAs, and secure embedded systems, it delivers 100% secure asymmetric cryptography acceleration for demanding applications.