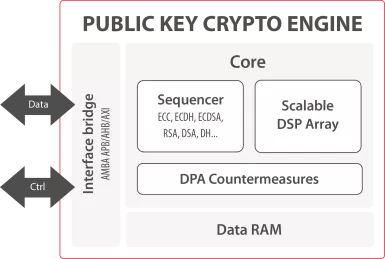
Public Key crypto engine IP
Filter
Compare
12
IP
from
4
vendors
(1
-
10)
-
Public Key Crypto Engine
- The Public Key Crypto Engine is a versatile IP core for hardware offloading of all asymmetric cryptographic operations.
- It enables any SoC, ASIC and FPGA to support efficient execution of RSA, ECC-based algorithms and more.
- The IP core is ready for all ASIC and FPGA technologies.
-
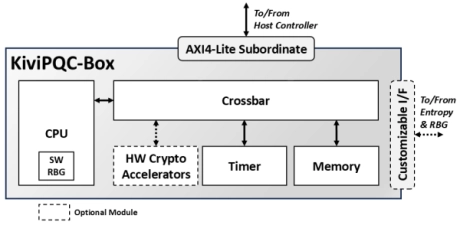
ML-KEM Key Encapsulation & ML-DSA Digital Signature Engine
- The KiviPQC™-Box is a hardware accelerator for post-quantum cryptographic operations.
- It implements both the Module Lattice-based Key Encapsulation Mechanism (ML-KEM) and the Module Lattice-based Digital Signature Algorithm (ML-DSA), standardized by NIST in FIPS 203 and FIPS 204, respectively.
-
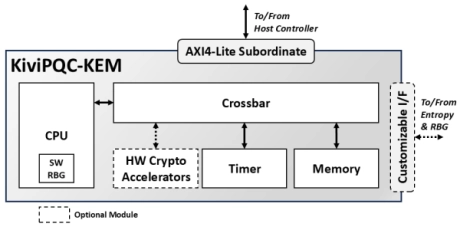
ML-KEM Key Encapsulation IP Core
- The KiviPQC™-KEM is a hardware accelerator for post-quantum cryptographic operations.
- It implements the Module Lattice-based Key Encapsulation Mechanism (ML-KEM), standardized by NIST in FIPS 203.
- This mechanism realizes the appropriate procedures for securely exchanging a shared secret key between two parties that communicate over a public channel using a defined set of rules and parameters.
-
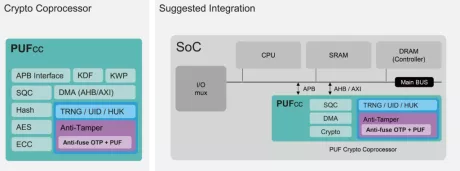
TLS 1.3 Compliant Crypto Coprocessor
- NIST CAVP certified and OSCCA standard compliant crypto engine suite
- Includes private/public key ciphers, message authentication code, hashes, and key derivation
- Key wrapping function for the secure export of keys
- Public-key coprocessor for digital signatures and key agreements over elliptic/Edward curves
-
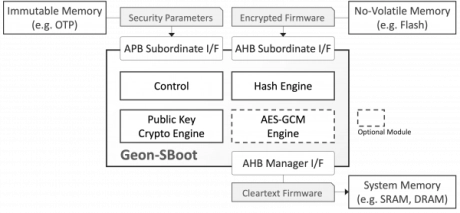
GEON™ Secure Boot Hardware Engine
- GEON-SBoot is an area-efficient, processor-agnostic hardware engine that protects SoC designs from booting with malicious or otherwise insecure code.
- The security platform employs public-key cryptography (which stores no secret on-chip) to ensure that only unmodified firmware from a trusted source is used by the system.
-
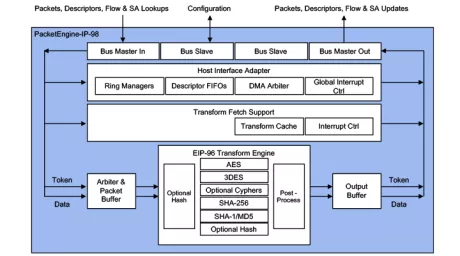
Multi-Protocol Engine with Classifier, Look-Aside, 5-10 Gbps
- Protocol aware IPsec, SSL, TLS, DTLS, 3GPP and MACsec Packet Engine with virtualization, caches classifier and Look-Aside interface for multi-core application processors
- 5-10 Gbps, programmable, maximum CPU offload by classifier, supports new and legacy crypto algorithms, AMBA interface
- Supported by Driver development kit, QuickSec IPsec toolkit, Linaro ODP, DPDK, Linux Crypto
-
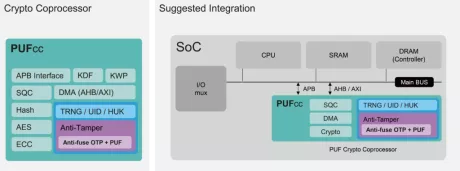
Crypto Coprocessor
- Comprehensively support all CPU architectures
- Crypto engine collective, consisting of private key cipher, message authentication code, hash, and key derivation functions that are NIST CAVP certified and OSCCA standards compliant
- Key wrapping function aiding the export of keys for external use
-
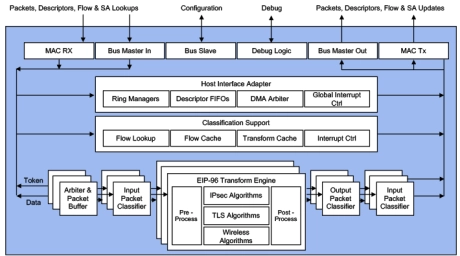
Multi-Protocol Engine with Classifier, Inline and Look-Aside, 10-100 Gbps
- Protocol aware IPsec, SSL, TLS, DTLS, 3GPP, MACsec packet engine with classifier and in-line interface for multi-core server processors
- 10-100 Gbps, programmable, maximum CPU offload by classifier, supports new and legacy crypto algorithms, streaming and AMBA interface
- Supported by Driver development kit, QuickSec IPsec toolkit, Linaro ODP.
-
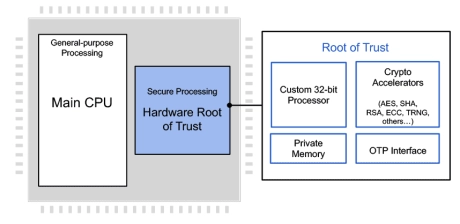
Programmable Root of Trust With DPA and FIA for US Defense
- Custom-designed 32-bit secure RISC-V processor
- Multi-layered security model protects all core components against a wide range of attacks
- Security model includes hierarchical privilege model, secure key management policy, hardware-enforced isolation/access control/protection, error management policy
- State-of-the-art DPA resistance, FIA protection and anti-tamper techniques
-
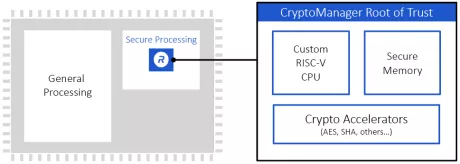
Programmable Root of Trust Family With DPA & Quantum Safe Cryptography
- Hardware Root of Trust employing a custom 32-bit RISC-V processor
- Multi-layered security model provides protection of all components in the core
- NIST CAVP and CMVP compliant for FIPS 140-3 validation
- State-of-the-art anti tamper techniques
- DPA-resistant cryptographic accelerators
- Caliptra Root of Trust for Measurement with DICE and X.509 support