Public Key Hardware Accelerator IP
Filter
Compare
12
IP
from
6
vendors
(1
-
10)
-
Agile PQC Public Key Accelerator
- Agile IP comprised of HW/FW/SW, adaptable to future standards’ evolution
- Highly configurable IP can be tuned for specific applications with most optimal PPA
- Scalable PQC PKA IP complies with latest NIST PQC algorithms
-
Public Key Accelerator
- Modular exponentiation operations with up to 4096-bit modulus
- Prime field ECC operations with up to 571-bit modulus
- Fastest implementation is 58 kGE and 68 Op/s for 2048-bit RSA, 431 Op/s for 1024-bit RSA, 150 Op/s for 384-bit scalar multiplication
- Smallest implementation is 33 kGE and 67 Op/s for 1024-bit RSA, 24 Op/s for 384-bit scalar multiplication
-
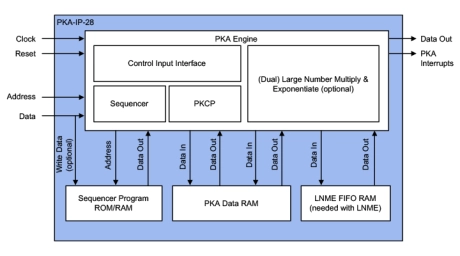
Small RSA/ECC Public Key Accelerators
- The PKA-IP-28 is a family of Public Key Accelerator IP cores designed for full scalability and an optimal “performance over gate count” deployment.
- Proven in silicon, the PKA-IP-28 public key accelerator addresses the unique needs of semiconductor OEMs and provides a reliable and cost-effective solution that is easy to integrate into SoC designs.
-
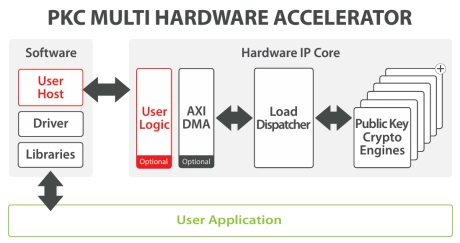
PKC Multi Hardware Accelerator IP
- The PKC Multi hardware accelerator is a secure connection engine that can be used to offload the compute intensive Public Key operations (Diffie-Hellman Key Exchange, Signature Generation and Verification), widely used for High-performance TLS Handshake.
-
ML-KEM Key Encapsulation & ML-DSA Digital Signature Engine
- The KiviPQC™-Box is a hardware accelerator for post-quantum cryptographic operations.
- It implements both the Module Lattice-based Key Encapsulation Mechanism (ML-KEM) and the Module Lattice-based Digital Signature Algorithm (ML-DSA), standardized by NIST in FIPS 203 and FIPS 204, respectively.
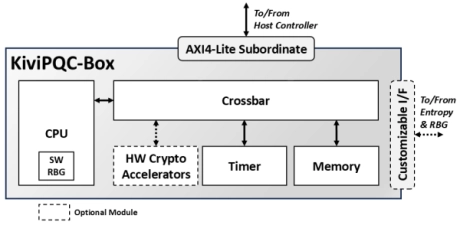
-
RSA2-AHB Accelerator Core with AHB Interface
- The core implements the exponentiation operation of the RSA cryptography Q = Pk.
- The operands for the exponentiation: k and P as well as the modulus are programmed into the memory and the calculation is started.
- Once the operation is complete, the result Q can be read through the AHB interface.
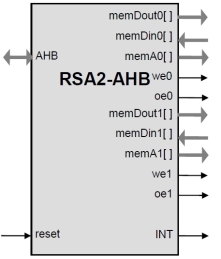
-
ML-KEM Key Encapsulation IP Core
- The KiviPQC™-KEM is a hardware accelerator for post-quantum cryptographic operations.
- It implements the Module Lattice-based Key Encapsulation Mechanism (ML-KEM), standardized by NIST in FIPS 203.
- This mechanism realizes the appropriate procedures for securely exchanging a shared secret key between two parties that communicate over a public channel using a defined set of rules and parameters.
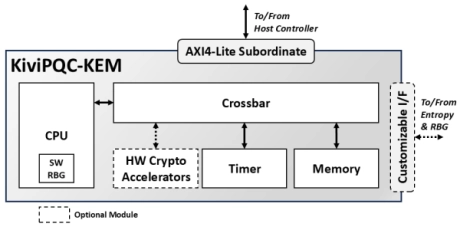
-
GEON™ Secure Boot Hardware Engine
- GEON-SBoot is an area-efficient, processor-agnostic hardware engine that protects SoC designs from booting with malicious or otherwise insecure code.
- The security platform employs public-key cryptography (which stores no secret on-chip) to ensure that only unmodified firmware from a trusted source is used by the system.
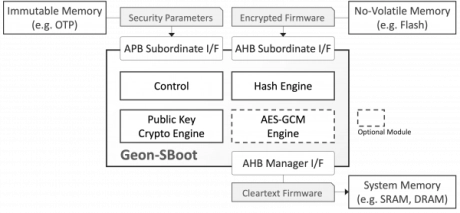
-
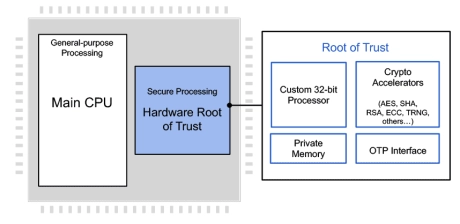
Programmable Root of Trust With DPA and FIA for US Defense
- Custom-designed 32-bit secure RISC-V processor
- Multi-layered security model protects all core components against a wide range of attacks
- Security model includes hierarchical privilege model, secure key management policy, hardware-enforced isolation/access control/protection, error management policy
- State-of-the-art DPA resistance, FIA protection and anti-tamper techniques