FIPS 140-2 IP
Filter
Compare
12
IP
from
5
vendors
(1
-
10)
-
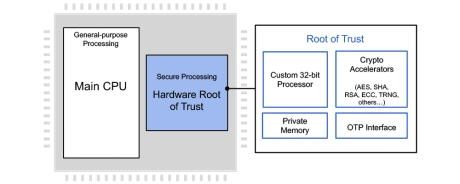
Embedded Hardware Security Module (Root of Trust) - Automotive Grade ISO 26262 ASIL-B
- The RT-64x Embedded Hardware Security Module (Root of Trust) family are fully programmable, ISO 26262 ASIL-B hardware security cores offering security by design for automotive applications.
- They protect against a wide range of failures such as permanent, transient and latent faults and hardware and software attacks with state-of-the-art anti-tamper and security techniques.
-
Cryptography Software Library
- Symmetric Ciphers
- Hashes
- RSA®
- ECC Prime Curves
- ECC Binary Curves
- Certificates (X.509 v3)
-
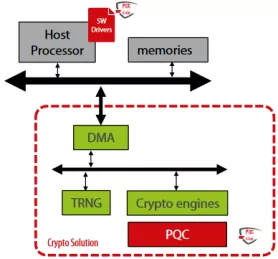
Crypto Coprocessor with integrated Post-Quantum Cryptography IPs
- The Crypto Coprocessors are a hardware IP core platform that accelerates cryptographic operations in System-on-Chip (SoC) environment on FPGA or ASIC.
- Symmetric operations are offloaded very efficiently as it has a built-in scatter/gather DMA. The coprocessors can be used to accelerate/offload IPsec, VPN, TLS/SSL, disk encryption, or any custom application requiring cryptography algorithms.
-
1G to 50G Single-Port MACsec Engine with TSN support
- Complete and compliant MACsec Packet Engine for rates from 1GbE to 50GbE with TSN support (including IEEE803.2br).
- All IEEE MACsec standards supported (incl. IEEE802.1AE-2018). Optional Cisco ClearTags.
- Supplied with the Driver Development Kit to accelerate time to market. Rambus offers MACsec Toolkit for IEEE 802.1X key management
-
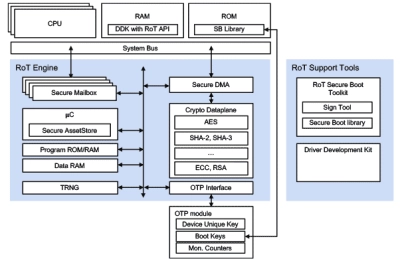
Root of Trust - Foundational security in SoCs and FPGAs for IoT servers, gateways, edge devices and sensors
- Secure Boot assist to host CPU(s) and protection of key material
- Secure firmware upgrade management for Host CPU
- Lifecycle management support
- Secure Debug support
- Secure device authentication and identity protection
-
Quantum Safe IPsec Toolkit
- Quantum Safe IPsec Toolkit (QuickSec Quantum) is first to market, complete IPsec software implementation with Quantum Safe cryptography support.
- Quantum Safe cryptography is designed to be resistant to quantum computer attacks and is required by any up-to-date security product.
-
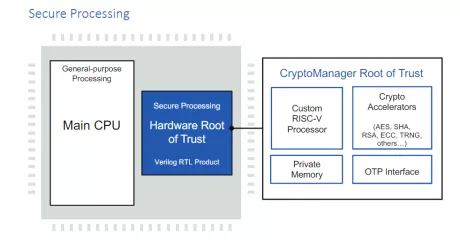
Embedded HSM Family (Root of Trust) - Automotive Grade ISO 26262 ASIL-B
- Custom-designed 32-bit RISC-V secure processor
- Security model include hierarchical privilege model, secure key management policy, hardware-enforced isolation/access control/protection, error management policy
- Standard hardware cryptographic accelerators, including AES (all modes), HMAC, SHA-2 (all modes), RSA up to 4096 bits, ECC up to 521 bits, a NIST-compliant Random Bit Generator, AXI Multi Issue Out-of-Order, and Fast DMA capability. Additional algorithms such as Whirlpool (SHE), SHA-1 (legacy), AES-CMAC, SHA-3, Poly1305, ChaCha and OSCCA SM2-3-4 are available
- Multi-layered security model protects all core components against a wide range of attacks
-
Deterministic Random Bit Generator (DRBG)
- The Deterministic Random Bit Generator is an essential silicon-proven digital IP core for all FPGA, ASIC and SoC designs that targets cryptographically secured applications.
- It is a deterministic algorithm compliant with the NIST-800-90A Rev1.
- The IP Core successfully passed NIST-800-90A Rev1 test suites and it is compliant with the FIPS-140-2 validation.
-
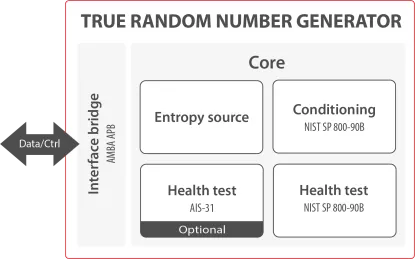
True Random and Pseudorandom Number Generator
- Satisfies Federal Information Processing Standard (FIPS) Publication 140-2 Annex C (“approved” random number generator) from the US National Institute of Standards and Technology (NIST). Passes the requirements of the NIST SP 800-22.
- High security (128 bit entropy; 256 version available)
- Initial seed provided from internal entropy source
- Automatic re-seeding
-
RSA/ECC Public Key Accelerator Farm with TRNG and AHB
- High-performance accelerator for Public Key operations, up to 4160-bit modulus size for modular exponentiations and 768-bit modulus for ECC operations
- Performs high-level key negotiate & sign/verify operations
- Synthesizable over 550 MHz in 40nm technologies and over 650 MHz in 28nm technologies
- Up to sixteen independent command/result queues